I can finally reveal some research I've been involved with over the past year or so.
We (@redford, @mrtick and I) have reverse engineered the PLC code of NEWAG Impuls EMUs. These trains were locking up for arbitrary reasons after being serviced at third-party workshops. The manufacturer argued that this was because of malpractice by these workshops, and that they should be serviced by them instead of third parti
es.
1/4
We found that the PLC code actually contained logic that would lock up the train with bogus error codes after some date, or if the train wasn't running for a given time. One version of the controller actually contained GPS coordinates to contain the behaviour to third party workshops.
It was also possible to unlock the trains by pressing a key combination in the cabin controls. None of this was documented.
2/4
The key unlock was deleted in newer PLC software versions, but the lock logic remained.
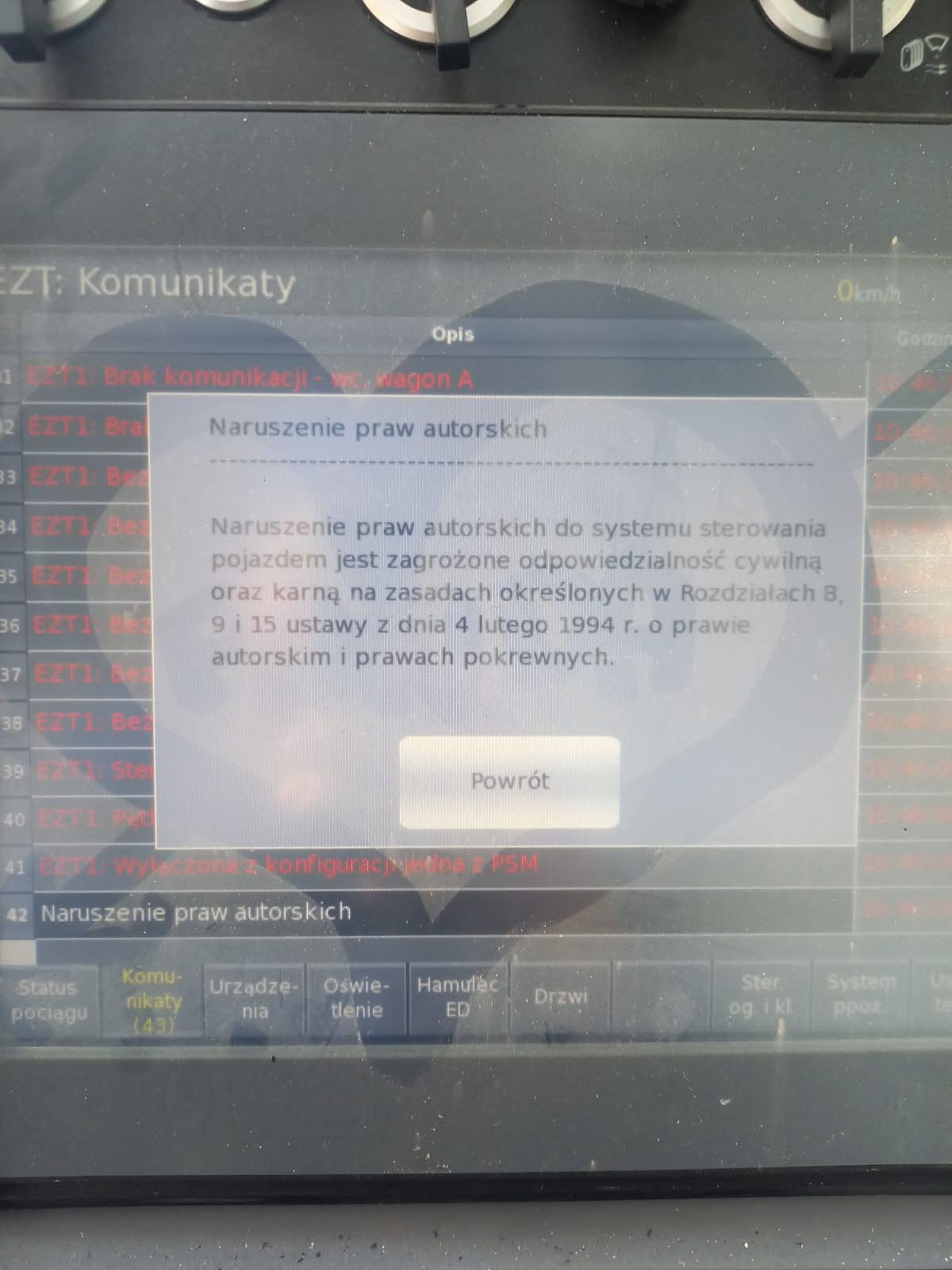
After a certain update by NEWAG, the cabin controls would also display scary messages about copyright violations if the HMI detected a subset of conditions that should've engaged the
lock but the train was still operational.
The trains also had a GSM telemetry unit that was broadcasting lock conditions, and in some cases appeared to be able to lock the train remotely.
3/4
@redford and @mrtick held an unrecorded talk a bout this at OhMyHack in Warsaw - I unfortunately couldn't make it because of Munich snow.
For now this is making the rounds in Polish-speaking sources, but we do have a talk scheduled about this at 37C3, in which we plan to do a deep dive into this and actually publish our findings.
@zaufanatrzeciastrona 's article about this: https://zaufanatrzeciastrona.pl/post/o-trzech-takich-co-zhakowali-prawdziwy-pociag-a-nawet-30-pociagow/
Kevin Karhan 
kkarhan@mstdn.social
@q3k Does any regulator know of this #Sabotage of #CriticalInfrastructure by the #Manufacturer?
I'm shure these trains ain't exclusive to to one country and regulators from @BNetzA and @kartellamt@social.bund.de to @EU_Commission will likely be very interested in such deliberate acts of #AntiCompetiton, #AntiRepair and basically attacks on #PublicTransport #infrastructure done by #NEWAG to fleece customers!
I mean, this is next-level assholeism and makes #JohnDeere and #Apple look like #RightToRepair fans.
@kkarhan @BNetzA @EU_Commission
Some relevant agencies are aware of the problem and are looking into this - can't say more than that yet.
@q3k @kkarhan @BNetzA @EU_Commission Some people in that manufacturer's offices ought to be sweating cold right now
Kevin Karhan 
kkarhan@mstdn.social
@raulinbonn @q3k @BNetzA @EU_Commission
I hope so, because they should not get away with 'we did it to enshure train safety and compliance' excuses.
This is just flat-out criminal behaviour!
Imagine if MAN were to disable trucks if they did get serviced by fire departments or logistics firms onsite instead of driven to a service center...
Andreas K
yacc143@mastodon.social@kkarhan @raulinbonn @q3k @BNetzA @EU_Commission
They should be treated as terrorists, or at least accomplices.
They basically installed backdoors that could be used by anyone (including terrorists) to trivially sabotage infrastructure.
@yacc143 @kkarhan @q3k @BNetzA @EU_Commission Of course as terrorists themselves, not just accomplices. Because they installed backdoors for themselves to surgically (while "invisibly") sabotage infrastructure at will.
qwertyoruiopz
qwertyoruiop@nso.group@q3k @redford @mrtick @zaufanatrzeciastrona At what point do people call this kind of stuff a protection racket?
Henry
hl@social.lolJohn Burns
JohnJBurnsIII@kzoo.to@q3k @redford @mrtick @zaufanatrzeciastrona
Is that a hack... or something put in place by company or its contractors?
Your post said 3rd party? Is that to mean they were using cheaper service providers?
---
I can only imagine what riders experienced.
yaoi gagarin
outie@slime.global@JohnJBurnsIII @q3k it reads to me as "DRM to ensure that orgs who bought the trains were only using maintenance contractors authorised by the manufacturer" and I'm pretty sure that there's regulation against that kind of thing in other vehicles (cars, say)
Adam Williamson 
adamw@fosstodon.org
@outie @JohnJBurnsIII @q3k yeah, I think you're missing the story here, John. It's the train manufacturer doing very sketchy stuff to try and prevent operators from having them maintained anywhere but their shops. Like if your car maker slipped some bogus code in that made your car refuse to start if you had it serviced at the local garage. Or your phone manufacturer doing the same, ahem, Apple.
Matěj Cepl 🇪🇺 🇨🇿 🇺🇦
mcepl@floss.social@adamw @outie @JohnJBurnsIII @q3k And now let's see what @EU_Commission will do about that. It's good to mention, that for the anticompetitive behaviour (and worse) they can fine the manufacturer up to 10% of their worldwide turnover (not profit, turnover).
Steve Freeman
sf105@mastodonapp.uk@jon it’s the sort of thing I would have expected safety regulators to pick up
Jon Worth
jon@gruene.social@sf105 whether regulators have adequate time to check to that level of detail though?
Jon Worth
jon@gruene.social@StOnSoftware @sf105 Were this somewhere other than Poland... I'd wager it'd have made a lot more controversy! (Sorry, but its rail industry - operators and manufacturers - still think very nationally there)
Konstantin Weddige
weddige@gruene.social@jon this might be interesting for you if you haven't seen it yet.