Posts
258Following
43Followers
126Omar Sandoval
osandovsj
sj[1] https://lore.kernel.org/20260218054320.4570-1-sj@kernel.org
[2] https://damonitor.github.io/posts/damon_cpus_write_monitoring_rfc_v3_plan/
#linux #kernel #damon #lsfmmbpf #numa_balancing
Greg K-H
gregkhhttp://www.kroah.com/log/blog/2026/02/16/linux-cve-assignment-process/
sj
sjTo quote the summary:
"So, 2024 was a year DAMON has more publicly and widely adopted, and extended
itself for more use cases."
[1] https://lore.kernel.org/20260216210625.68098-1-sj@kernel.org
#linux #kernel #damon #2024 #yearly_retro
K. Ryabitsev-Prime 🍁
monsieuriconWe need more redundancy for these systems. After exiting Equinix, we are reduced to just 2 nodes (and hence, we're now down to 1 until I rebuild the RAID array on the one that's currently offline).
If you can donate us a server with at least 70TB of space and lots of bandwidth, I'd like to hear from you, but it has to come with hosting, as we don't have any physical datacentres any more and must rely on the kindness of strangers to host them.
sj
sj1. I proposed [1] an LSF/MM/BPF session for discussing how production-level data access-aware transparent hugepages can be developed.
2. DAMON has nominated [2] as one of Linux kernel Machine Lerarning Library's demonstration targets.
[1] https://lore.kernel.org/20260211022845.68865-1-sj@kernel.org
[2] https://lore.kernel.org/c24a209d5a4af0c4cc08f30098998ce16c668b58.camel@ibm.com
#linux #kernel #lsfmmbpf
Kernel Recipes
KernelRecipes@fosstodon.orgSince we’re not superstitious, the 13th edition of KR will take place September 21–23, 2026 (black cats strictly forbidden during this edition — even on a leash… 😄). We hope to see loads of you there!
And because we want to keep offering the best possible conditions for three days of good vibes and community for everyone, feel free to support this edition by becoming a sponsor. All the info is here!
Jonathan Corbet
corbethttps://lwn.net/ml/all/caa37f28-a2e8-4e0a-a9ce-a365ce805e4b@stanley.mountain
He says: "The situation isn't great. The zero day bot can't do cross function analsysis and it only looks at checks with a low false positive rate. We're missing out on a bunch of bugs." *Not* missing those bugs sounds like it would be a good thing.
sj
sj[1] https://github.com/damonitor/damo/tree/next
#linux #kernel #damon #damo #command_autocompletion
K. Ryabitsev-Prime 🍁
monsieuriconhttps://youtu.be/wOi_qHSO7KY
Vlastimil Babka 🇨🇿🇪🇺🇺🇦
vbabka@mastodon.socialOnce again there's a kernel developer position open in the SUSE Labs Kernel Core team I'm part of! https://suse.wd3.myworkdayjobs.com/en-US/Jobsatsuse/job/Czech-Republic-EMEA/Linux-Kernel-Generalist_71007379
Jonathan Corbet
corbetThere are many things I would like to do with my time. Defending LWN from AI shitheads is rather far from the top of that list. I *really* don't want to put obstacles between LWN and its readers, but it may come to that.
(Another grumpy day, sorry)
Thorsten Leemhuis (acct. 1/4)
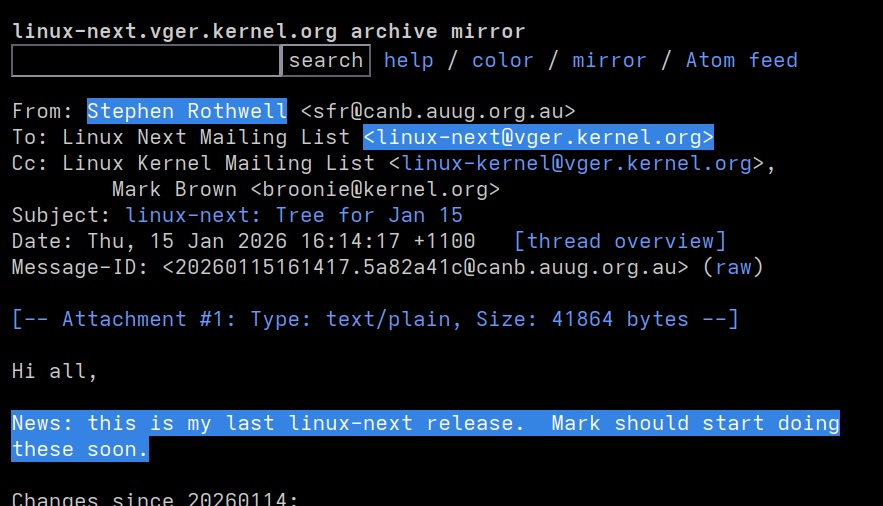
kernellogger@hachyderm.io""News: this is my last linux-next release. Mark should start doing these soon."" – Stephen Rothwell in https://lore.kernel.org/linux-next/20260115161417.5a82a41c@canb.auug.org.au/
Reminder, Stephen announced that he would be stepping down a few weeks ago[1]]
Many many thanks, Stephen, for all your work over nearly 18 years[2], much much appreciated!
And thanks @broonie for picking up this thankless task!
[1] https://hachyderm.io/@kernellogger/115739700056940486
[2] Tue, 12 Feb 2008 – Announce: Linux-next (Or Andrew's dream :-)) – https://lore.kernel.org/all/20080212120208.f7168a91.sfr@canb.auug.org.au/
Jonathan Corbet
corbethttps://www.webpronews.com/linux-kernels-future-tab-integrates-rust-navigates-ai-boosts-collaboration/
Google News propagates that stuff - something they have long refused to do with LWN's original material. But somehow we're supposed to continue to exist to feed material into that machine?
Sorry, having a grumpy day.
Christian Brauner 🦊🐺
brauner@mastodon.socialRE: https://mastodon.social/@brauner/115871045863565861
Be sure to request an invite to #lsfmmbpf 2026 in Zagreb, Croatia!
Greg K-H
gregkhsj
sjIn 2025, I made 2nd and 1st biggest changes to Linux kernel memory management subsystem among the 321 people, in terms of lines of changes (6,661 / 73,685 lines) and commits (199 / 1,870 commits).
For the Linux kernel whole tree, the numbers become 71-st (11,362 / 4,809,577 lines) and 25th (333 / 75,462 commits) among 5,637 people.
For open source projects other than Linux, I made around 564,210 lines of changes with around 2,157 commits.
For more details of the stats and how it was made, refer to https://sjp38.github.io/posts/my_opensource_commits_stat_2025/
#2025 #commits #statistics #linux #kernel #damon #memory_management
Linus Torvalds
torvaldsGPLv2 affirmation…
I don’t generally post here as people have probably noticed, but here’s a pdf of a recent court ruling, and this turns out to be the easiest way for me to link to a copy of it, since I don’t really maintain any web presence normally and I don’t want to post pdf’s to the kernel mailing lists or anything like that.
And the reason I want to post about it, is that it basically validates my long-held views that the GPLv2 is about making source code available, not controlling the access to the hardware that it runs on.
The court case itself is a mess of two bad parties: Vizio and the SFC. Both of them look horribly bad in court - for different reasons.
Vizio used Linux in their TVs without originally making the source code available, and that was obviously not ok.
And the Software Freedom Conservancy then tries to make the argument that the license forces you to make your installation keys etc available, even though that is not the case, and the reason why the kernel is very much GPLv2 only. The people involved know that very well, but have argued otherwise in court.
End result: both parties have acted badly. But at least Vizio did fix their behavior, even if it apparently took this lawsuit to do so. I can’t say the same about the SFC.
Please, SFC - stop using the kernel for your bogus legal arguments where you try to expand the GPLv2 to be something it isn’t. You just look like a bunch of incompetent a**holes.
The only party that looks competent here is the judge, which in this ruling says
Plaintiff contends the phrases, “machine-readable” and “scripts used to control compilation and installation” support their assertion in response to special interrogatory no. 4 that Defendant should “deliver files such that a person of ordinary skill can compile the source code into a functional executable and install it onto the same device, such that all features of the original program are retained, without undue difficulty.”
The language of the Agreements is unambiguous. It does not impose the duty which is the subject of this motion.
Read as a whole, the Agreements require Vizio to make the source code available in such a manner that the source code can be readily obtained and modified by Plaintiff or other third parties. While source code is defined to include “the scripts used to control compilation and installation,” this does not mean that Vizio must allow users to reinstall the software, modified or otherwise, back onto its smart TVs in a manner that preserves all features of the original program and/or ensures the smart TVs continue to function properly. Rather, in the context of the Agreements, the disputed language means that Vizio must provide the source code in a manner that allows the source code to be obtained and revised by Plaintiff or others for use in other applications.
In other words, Vizio must ensure the ability of users to copy, change/modify, and distribute the source code, including using the code in other free programs consistent with the Preamble and Terms and Conditions of the Agreements. However, nothing in the language of the Agreements requires Vizio to allow modified source code to be reinstalled on its devices while ensuring the devices remain operable after the source code is modified. If this was the intent of the Agreements, the Agreements could have been readily modified to state that users must be permitted to modify and reinstall modified software on products which use the program while ensuring the products continue to function. The absence of such language is dispositive and there is no basis to find that such a term was implied here. Therefore, the motion is granted.
IOW, this makes it clear that yes, you have to make source code available, but no, the GPLv2 does not in any way force you to then open up your hardware.
My intention - and the GPLv2 - is clear: the kernel copyright licence covers the software, and does not extend to the hardware it runs on. The same way the kernel copyright license does not extend to user space programs that run on it.
sj
sj[1] https://social.kernel.org/notice/B1QVooy6voIN85T33I
[2] https://youtu.be/f09kvPvYMsM?si=EXUiMTrZSpwTXMGy
#ossummit #linux #kernel #hkml