Conversation
Jarkko Sakkinen
jarkko
Edited 1 year ago
If #Radare2 vs #Rizin makes no sense to you, perhaps #Python will. It is pretty solid tool for driving #Capstone :-)
Transcript:
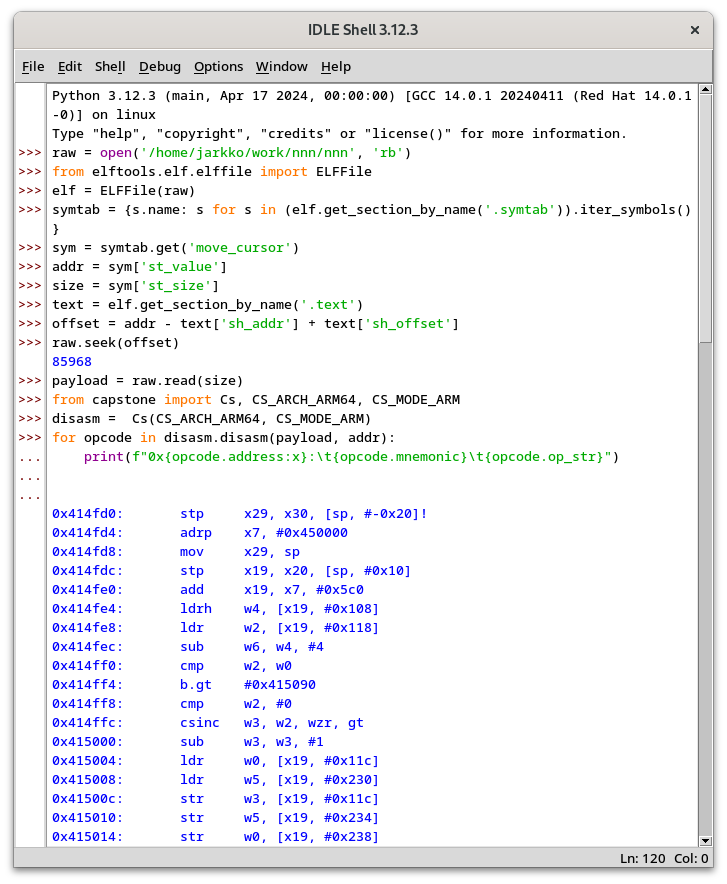
raw = open('/home/jarkko/work/nnn/nnn', 'rb')
from elftools.elf.elffile import ELFFile
elf = ELFFile(raw)
symtab = {s.name: s for s in (elf.get_section_by_name('.symtab')).iter_symbols()}
sym = symtab.get('move_cursor')
addr = sym['st_value']
size = sym['st_size']
text = elf.get_section_by_name('.text')
offset = addr - text['sh_addr'] + text['sh_offset']
raw.seek(offset)
payload = raw.read(size)
from capstone import Cs, CS_ARCH_ARM64, CS_MODE_ARM)
disasm = Cs(CS_ARCH_ARM64, CS_MODE_ARM)
for opcode in disasm.disasm(payload, addr):
print(f"0x{opcode.address:x}:\t{opcode.mnemonic}\t{opcode.op_str}")
Just got a bit familiar this. The main benefits are obviously:
- Recursive traversal #disassembly (vs linear sweep style in
objdump) - Re-usable analysis
- No boundaries how you can post-process the analysis (or visualize it)
I find this super fascinating!
Jarkko Sakkinen
jarkko
Next test run might be to combine this with #angr perhaps... https://angr.io/
Anisse @ FOSDEM
Aissen@social.treehouse.systems@jarkko afaik both r2 and rz rely on capstone (partially)
Jarkko Sakkinen
jarkko
Edited 1 year ago
@Aissen Forks confuse me too much, if I don't know the clear reasoning for them, and they both are quite rich and complex tools, and I would not want invest learning "the wrong one". So I just decided to take the beef, use the tool that I already know (Python), and move forward with my life I guess 🤷
Jarkko Sakkinen
jarkko
Edited 1 year ago
@rjzak Ghidra is something that I use sometimes just get ideas but this more when I already have "a target of interest". I.e. I know what data etc. I'm looking for :-)
Both are used for disassembly but still pretty different type of instruments.
Depite reverse engineering of malware and kernel engineering have commonalities in tools, they're still different type of Sudoku's... Malware has more "easter eggs" so to speak ;-) And requires factors more dynamic analysis and simulation.
Both are used for disassembly but still pretty different type of instruments.
Depite reverse engineering of malware and kernel engineering have commonalities in tools, they're still different type of Sudoku's... Malware has more "easter eggs" so to speak ;-) And requires factors more dynamic analysis and simulation.