Posts
12Following
15Followers
4I also post at https://toot.io/@amit on a wider range of topics and interests.
Amit Shah
amitJonathan Corbet
corbethttps://lwn.net/ml/all/4d7tq6a7febsoru3wjium4ekttuw2ouocv6jstdkthnacmzr6x@f2zfbe5hs7h5
Linux Plumbers Conference
linuxplumbersconf@mastodon.socialGreat news! In-person registration for LPC 2024 is reopened!
https://lpc.events/blog/current/index.php/2024/08/16/registration-is-now-reopened/
Amit Shah
amit"There was an error displaying the search results. Please try again."
when its upstream is down. It's also weird to see the website load properly, not acknowledge any disruption in service, and still fail all searches...
LWN.net is now @LWN@lwn.net
LWN@fosstodon.orgA few relevant quotes https://lwn.net/Articles/967420/ #LWN
Jonathan Corbet
corbetPart of the success in getting this into Debian may be the result of there being no xz maintainer there. It is "maintained" by people whose attention is normally elsewhere doing occasional non-maintainer updates.
This code will have been running on the machines of a lot of distribution maintainers. If it has already been exploited, it could be that its real purpose has already been achieved and the real problem is now elsewhere. I sure hope somebody can figure out a way to determine if this backdoor has been used.
The multi-front nature of the attack, including multiple efforts to get the malicious code installed more widely more quickly, suggests we're not just dealing with a lone sociopath. I fear we'll never know who was really behind this, but I would sure like to.
There is surely more where this cam from.
Jonathan Corbet
corbetAlso if you're on F41 and/or think you might have installed the vulnerable xz anywhere, note that the exploit has not been fully analyzed and no one really knows what it could do. I'm currently reinstalling a couple of machines from scratch and have regenerated my SSH keys.
Linus Torvalds
torvaldsSome of you know today as π-day.
But the real insiders know that today is the 30th anniversary of the 1.0 release of Linux.
sj
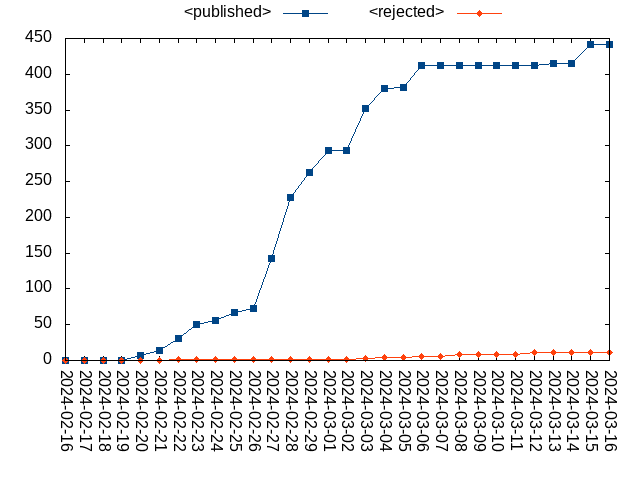
sjI wanted to know simple daily Linux kernel CVE statistics just for fun, so wrote a script[1] and plotted the output.
$ ./vulns_stat.sh ./vulns/ 30 | ../gnuplot/plot.py --data_fmt table --type labeled-lines --xtics_rotate -90 cve_stat_30_days.png
[1] https://github.com/sjp38/lazybox/blob/master/cve_stat/vulns_stat.sh
Framework 

frameworkcomputer@fosstodon.org
A good time to remind everyone that we are remote-first and are hiring: http://jobs.frame.work
Sovereign Tech Agency
sovtechfund@mastodon.socialWe’re seeking input from #FOSS maintainers as we design a fellowship program pilot. We want to test a support mechanism that addresses structural issues in the FOSS ecosystem, and support maintainers who work on open digital infrastructure in the public interest.
If you maintain open source projects, we would be very grateful if you could take ten minutes to respond to the survey:
https://survey.sovereigntechfund.de/968766
Please also repost and share with FOSS maintainers you know. Thanks!