Posts
366Following
96Followers
4259Greg K-H
gregkhGreg K-H
gregkhGreg K-H
gregkh@kernellogger Your data is going to be a bit skewed here, we have ONLY processed the v6.7..v6.7.1 and most of the v6.7.1..v6.7.2 commits so far for CVE-related stuff, which by far the majority have only Fixes: tags due to my travel schedule during those releases (i.e. I didn’t have the cycles to catch up with the cc: stable@ tagged commits. I bet the numbers will level out over time as we catch up with the rest of the commits in the v6.7.Y releases.
And it’s good to see people paying attention, thank you!
Thorsten Leemhuis (acct. 1/4)
kernellogger@fosstodon.orgDid a quick *rough* check:
* 65 #Linux #kernel CVE announcements from Greg so far
* 55 of those refer to a mainline commit
* 10 of those were marked for backporting to stable/longterm
And that's why Greg backports a lot of #LinuxKernel mainline commits to stable/longterm that are *not* tagged for backporting -- and why "only backport changes mainline developers[1] tagged for backporting" is a bad idea.
[1] reminder, such tagging is optional, as participation in stable/longterm is optional
Greg K-H
gregkhGreg K-H
gregkhsjvn
sjvn@mastodon.socialThe #Linux kernel developers are now issuing their own, more accurate Common Vulnerabilities and Exposures #security bulletins. https://opensourcewatch.beehiiv.com/p/linux-gets-cve-security-business by @sjvn
The Linux kernel developers are now in charge of its Common Vulnerabilities and Exposures (CVE) security problems.
lcamtuf 


lcamtuf@infosec.exchange
Computer folks, remember the precedence of operators! Consult this handy list if in doubt:
() [] -> .
! ~ ++ --
* / %
+ -
<< >>
< <= > >=
== != &=
=== &&& |||
?: ??= ( ^..^)ノ
(╯°□°)╯︵ ┻━┻
Kees Cook (old account)
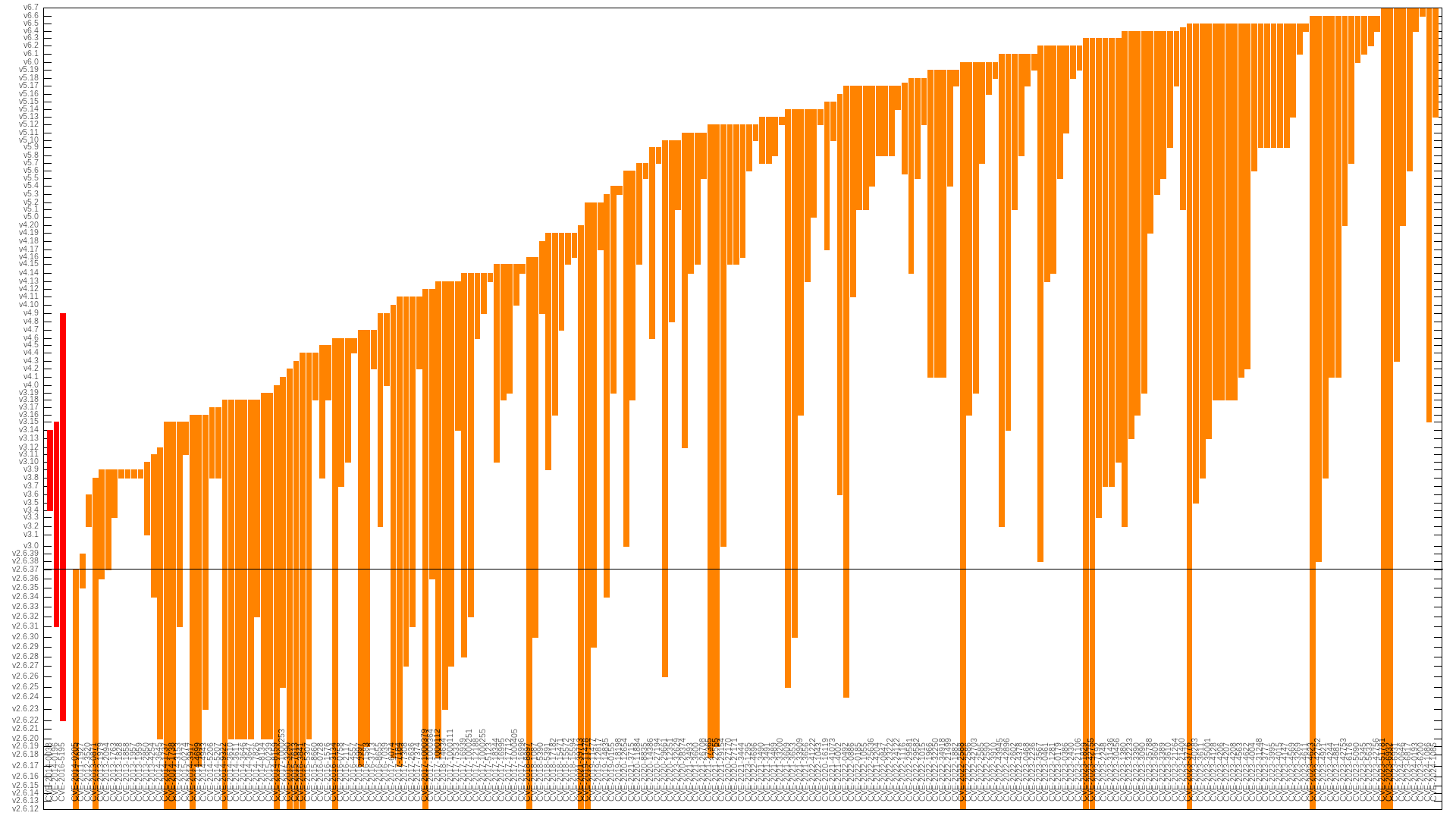
kees@fosstodon.orgv6.5 fixed almost twice as many "high" CVEs (19) than the second most prolific release, v6.6 (11), with v6.4 & v5.17 tied for 3rd place (9). It seems like the rate of fixing is picking up.
Ignoring the first git release (v2.6.12), the "high" flaw introduction counts are relatively even. Highest (i.e. most well tested/researched) releases have been v3.8 (9), v3.18 & v2.6.20 tied (8), and v5.9 & v4.1 tied (6).
But certainly more flaws are in all releases -- they just haven't been found yet.
Kees Cook (old account)
kees@fosstodon.orgLast time I did a Linux kernel security flaw lifetime analysis was back in 2021. It showed the average time between flaw introduction and fix was 5.5 years for 108 "high priority" CVEs:
https://outflux.net/slides/2021/lss/kspp.pdf
I refreshed my dataset today and was surprised to see that now with 103 more CVEs, it's still holding at 5.5 years. This actually means Linux is getting faster at finding issues, but the (diminishing) technical debt of the past is still dragging down the average.
Greg K-H
gregkhGreg K-H
gregkhThe current scripts I wrote want a one-to-one mapping, but we will fix this in the future. Let's get the simple ones working first please. The mapping of commit to version numbers is complex enough to get right, we are still hashing it out as to the proper way to encode it all correctly.
See the huge comment block in the tool `bippy` for the issues involved in just single commit tracking: https://git.kernel.org/pub/scm/linux/security/vulns.git/tree/scripts/bippy#n255
LWN.net is now @LWN@lwn.net
LWN@fosstodon.org[$] A turning point for CVE numbers https://lwn.net/Articles/961978/ #LWN
Greg K-H
gregkhAnyway, I understand your basic point, but I think the way that other governments are starting to treat open source projects, this is something that everyone is going to have to deal with soon enough.