Posts
208Following
156Followers
169Jens Axboe
axboe@fosstodon.orgMentioned this in passing, but want to publicly thank Dell for sponsoring a big test box. Tons of storage, tons of bandwidth, and now 100G connected in my little lab for great io_uring networking testing as well. They even stopped by my office for a day to rack mount it!
Boston Bike Blockers
BostonBikeBlockers@mastodon.socialCambridge Street, Cambridge.
This isn't a lack of parking; this is a driver who couldn't be bothered to pull all the way into the space.
Harry Sintonen
harrysintonen@infosec.exchangeI implemented Ken Thompson’s Reflections on Trusting Trust (1984 Turing Award Lecture) compiler #backdoor for the GNU Compiler Collection (GCC). The backdoor maintains persistence by re-injecting itself to any new versions of the compiler built. The secondary payload modifies a test application by adding a backdoor password to allow authentication bypass:
$ cat testapp.c
#include <string.h>
#include <stdio.h>
#include <stdlib.h>
int main(int argc, char **argv)
{
if (argc == 2 && !strcmp(argv[1], "secret"))
{
printf("access granted!\n");
return EXIT_SUCCESS;
}
else
{
printf("access denied!\n");
return EXIT_FAILURE;
}
}
$ gcc -Wall -O2 -o testapp.c -o testapp
$ ./testapp kensentme
access granted!
$
I spent most time (around two hours) writing the generalized tooling that produces the final quine version of the malicious payload. Now that this is done, the actual code can be adjusted trivially to exploit more target code without any need to adjust the self-reproducing section of the code. This method of exploitation could be extended to target various binaries: SSH Server, Linux Kernel, Setuid binaries and similar. While itself written in C, the secondary payloads can target any programming languages supported by GCC.
It should be noted that GCC build checks for malicious compiler changes such as this. This check can – of course – also be bypassed. However, most serious projects have measures in place to avoid hacks of this nature.
Some links:
- Ken Thompson's "Reflections on Trusting Trust" paper: https://www.cs.cmu.edu/~rdriley/487/papers/Thompson_1984_ReflectionsonTrustingTrust.pdf
- David A. Wheeler: "Fully Countering Trusting Trust through Diverse Double-Compiling (DDC) - Countering Trojan Horse attacks on Compilers" https://dwheeler.com/trusting-trust/
#hacking #exploitdevelopment #kenthompson #infosec #cybersecurity @vegard
LWN.net is now @LWN@lwn.net
LWN@fosstodon.org[$] Gentoo bans AI-created contributions https://lwn.net/Articles/970072/ #LWN
K. Ryabitsev-Prime 🍁
monsieuriconFor a few years now I've been trying to convince these callers that they have reached the wrong person and that I'm actually with "Lennox Foundation Repair." Yes, I do IT because I'm in charge of the laptop used to inspect the subfloors with a camera.
I know this is petty, but it brings me 2 minutes of schadenfreude joy as I hear the poor sod on the other end of the line get progressively more and more confused.
(Bonus points if you get the "I'm a flooring inspector" reference.)
K. Ryabitsev-Prime 🍁
monsieuriconInitial implementation. The goal was to show a quick summary without outputting a wall of obtuse text.
Thorsten Leemhuis (acct. 1/4)
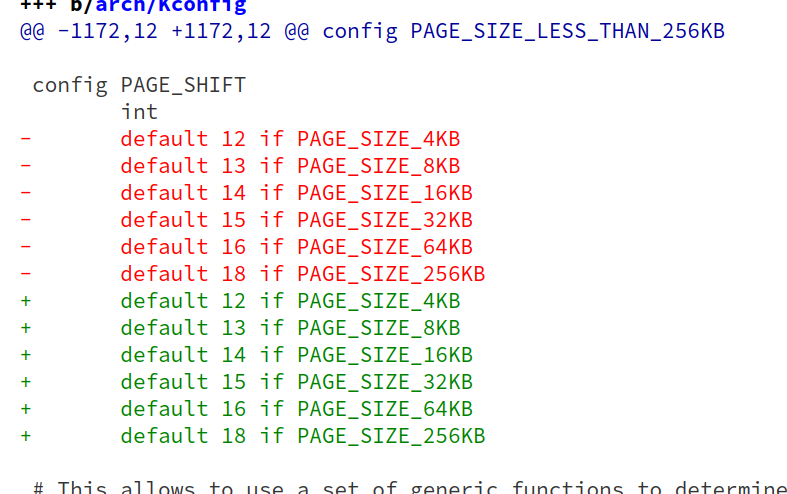
kernellogger@fosstodon.orgLinus is a bit devious 😬
"'Kconfig: add some hidden tabs on purpose
[…] showed breakage in some third-party kernel config parsing tool.
[…] let's make sure it gets fixed. Because if you can't parse tabs as whitespace, you should not be parsing the kernel Kconfig files.
In fact, let's make such breakage more obvious than some esoteric ftrace record size option. If you can't parse tabs, you can't have page sizes."'
https://git.kernel.org/torvalds/c/d5cf50dafc9dd5faa1e61e7021e3496ddf7fd61e
Henrik Grimler
grimler@mastodon.socialHappy to announce that I am now a Trusted Contributor in the @postmarketOS project! It has been around 3.5 years since I found out about it and started contributing (mostly with ports and mainline linux support for various Samsung devices). It really feels great to be part of a joint effort to give devices a second life, and decrease the amount of #eWaste in the world!
Sy Brand
TartanLlama@mastodon.socialI managed to embed a programming language interpreter inside DWARF debug information on Linux.
I'll be giving a very cursed talk about how it works at Pure Virtual C++ at the end of the month:
https://devblogs.microsoft.com/cppblog/pure-virtual-cpp-2024-sessions-announced/
Andrew Plotkin
zarfeblong@mastodon.gamedev.placeI guess the takeaway from the xz backdoor situation is:
If you’re an open-source project maintainer, and somebody starts getting on your case for not doing enough free work for them, you reply “big Jia Tan energy there” and then block them forever.
Paying maintainers who accept monetary donations is a good start, but the real critical thing people need to do is stop abusing maintainers. Stop abusing random people on the internet in general. Seriously.
I know we've all got capitalism brain worms, but sometimes the only thing that is accomplished by throwing money at a project is creating a customer entitlement dynamic that pointlessly increases the stress placed on volunteers.
Ask maintainers what kind of support they need.
Chips and Cheese
chipsandcheese@techhub.socialHello you fine Internet folks
Today's article is on a Mainframe. A system that has seemingly dethroned the king of the mainframe, IBM.
Today, we are looking at Control Data Corporation's CDC 6600, the fastest mainframe available today!
Hope y'all enjoy!
https://chipsandcheese.com/2024/04/01/inside-control-data-corporations-cdc-6600/
Tony Hoyle
tony@hoyle.me.uk"Scotland's new hate crime law has come into force, with JK Rowling and Elon Musk among its critics."
First line of the article and I'm already a big fan of the new law.
The War on Cars
TheWarOnCars@mastodon.social"In 2022, cars killed 7,508 pedestrians, the equivalent of 18 fully-loaded Boeing 747s crashing with zero survivors. That means a pedestrian died roughly every 70 minutes, with no breaks in the tide of fatalities for weekends or holidays."
https://www.motor1.com/features/713936/pedestrian-deaths-emergency/
BrianKrebs
briankrebs@infosec.exchangeLa la la. No this doesn't sound sketch.
Telegram is offering a new way to earn a premium subscription free of charge: all you have to do is volunteer your phone number to relay one-time passwords (OTP) to other users. This, in fact, sounds like an awful idea — particularly for a messaging service based around privacy.
https://www.theverge.com/2024/3/25/24111818/telegram-peer-to-peer-login-otp-two-factor-volunteer
Julia Evans
b0rk@jvns.caknowing where you are in git
https://wizardzines.com/comics/knowing-where-you-are-in-git/