Posts
218Following
37Followers
109sj
sjMore formal announcement: https://lore.kernel.org/r/20240416184044.98993-1-sj@kernel.org
#linux #kernel #damon #ossummit
sj
sj[1] https://github.com/awslabs/damo/blob/v2.3.0/release_note#L4
[2] https://github.com/awslabs/damo/blob/v2.3.0/USAGE.md#footprints
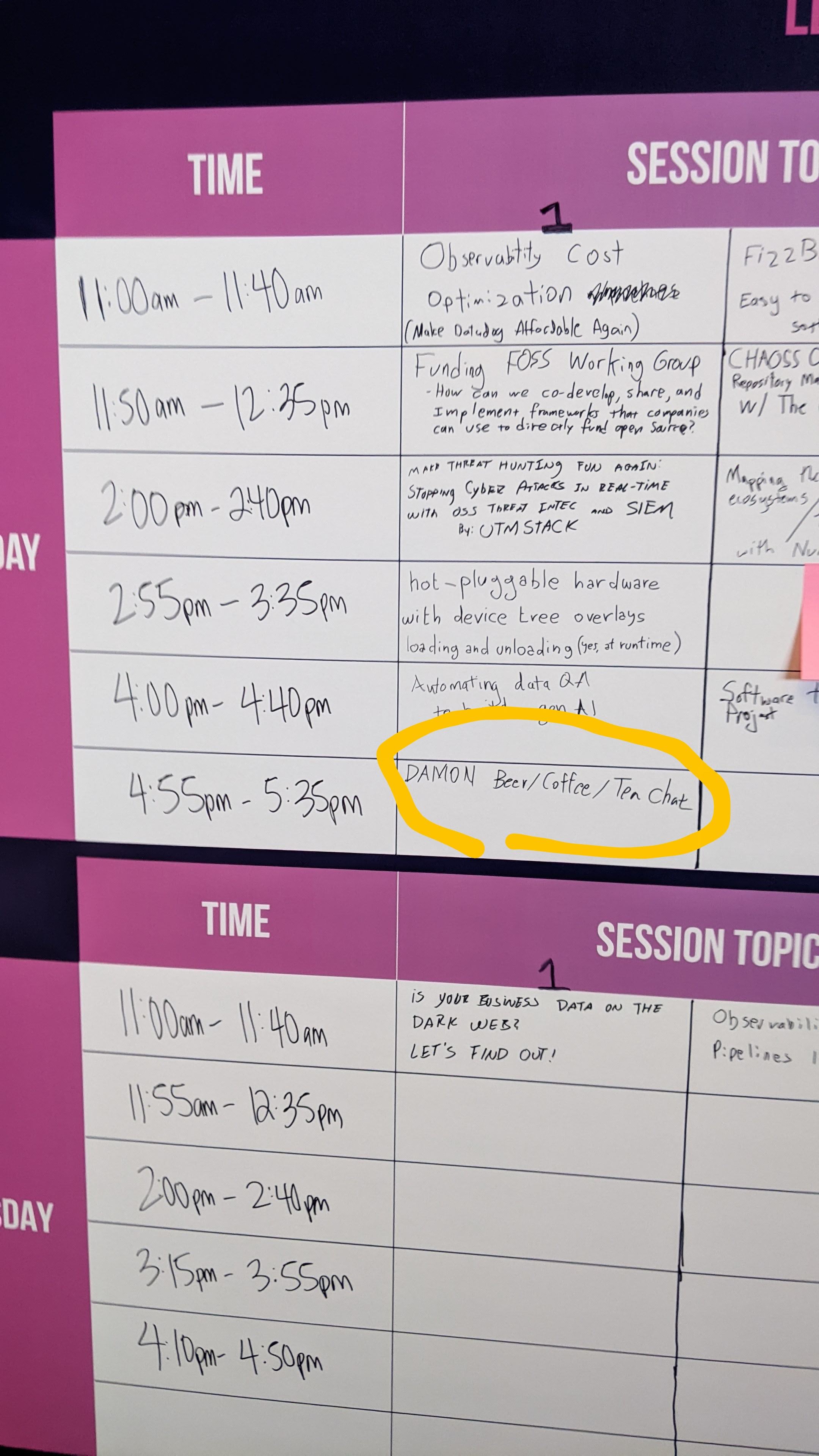
[3] https://sched.co/1aBOg
#linux #kernel #damon #damo
sj
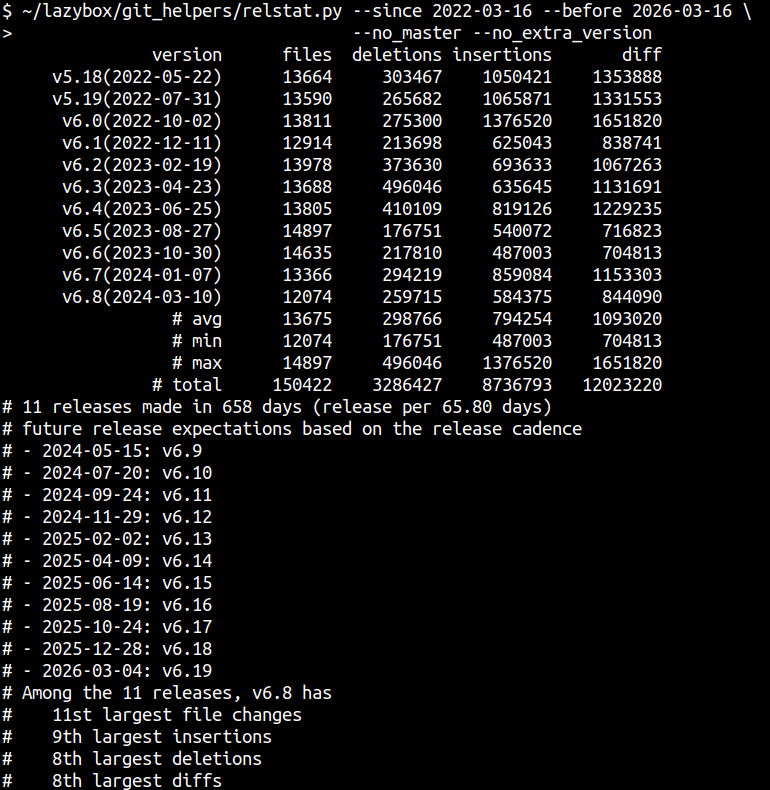
sjI sometimes do git log --author to know developers including myself for just fun, retrospects, or interviews. It was not easy to get the whole picture with my poor brain. Hence I wrote a script: https://github.com/sjp38/lazybox/blob/master/git_helpers/profile_author.py
E.g.,
$ ./profile_author.py "SeongJae Park" --branch linus/master --repo ~/linux --max_files 10
since 2023-04-14 until 2024-04-13
# <changed_lines> <file>
746 mm/damon/sysfs-schemes.c
735 Documentation/admin-guide/mm/damon/usage.rst
646 mm/damon/core.c
522 Documentation/mm/damon/design.rst
405 tools/testing/selftests/damon/_damon_sysfs.py
291 include/linux/damon.h
273 mm/damon/sysfs.c
179 mm/damon/core-test.h
100 Documentation/ABI/testing/sysfs-kernel-mm-damon
86 mm/damon/sysfs-test.h
# 5035 total lines
# 52 total files
# 172 commits
sj
sj[1] https://github.com/sjp38/hackermail/blob/v1.0.3/USAGE.md#public-inbox-search
#hackermail
sj
sjhttps://oracle.github.io/kconfigs/?config=UTS_RELEASE&config=DAMON&config=DAMON_RECLAIM&config=DAMON_LRU_SORT
#linux #kernel #damon
RE: https://snake.club/users/brenns10/statuses/112208220192120480
Stephen Brennan
brenns10@snake.clubI made a tool to help view kernel configuration values and compare them across many Linux distributions. Here's a blog post introducing it:
https://blogs.oracle.com/linux/post/explore-linux-kernel-kconfigs
Or, you can skip right to the tool here:
https://oracle.github.io/kconfigs/
Source is available here:
https://github.com/oracle/kconfigs
sj
sj"""
To recap, the long-awaited DAMOS auto-tuning feature has merged. More people
from the academy and the industry explored and contributed on DAMON. DAMON
user-space tool got more useful features. We will have yet another DAMON
presentation and discussion at OSSummit NA and LSF/MM/BPF.
"""
#linux #kernel #damon
sj
sj[1] https://github.com/awslabs/damo/blob/v2.2.8/USAGE.md#recording-memory-footprints
#linux #kernel #damon #damo
sj
sj[1] https://github.com/sjp38/hackermail/blob/v1.0.2/release_note
[2] https://github.com/sjp38/hackermail/blob/v1.0.2/USAGE.md#drafts
#hackermail #hkml
sj
sjsj
sj[1] https://github.com/sjp38/hackermail/blob/v1.0.1/release_note
[2] https://github.com/sjp38/hackermail/blob/v1.0.1/USAGE.md#synchronizing
#hackermail #hkml
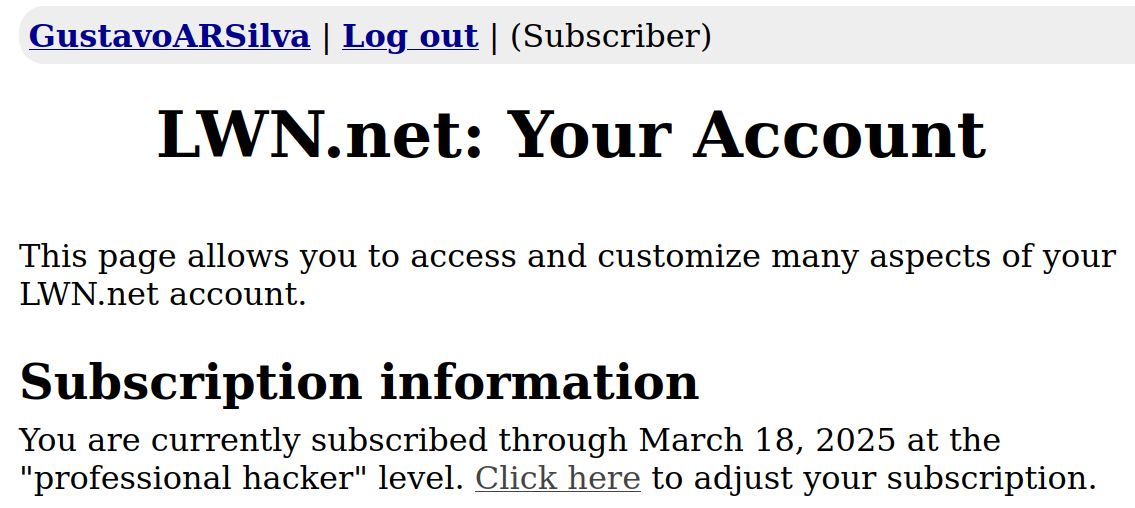
Gustavo A. R. Silva 
gustavoars@fosstodon.org
I just renewed my subscription to @LWN
The best content about bleeding-edge Linux kernel development! 🐧 🙌
You should really consider subscribing if you haven't done it yet. 🙂
sj
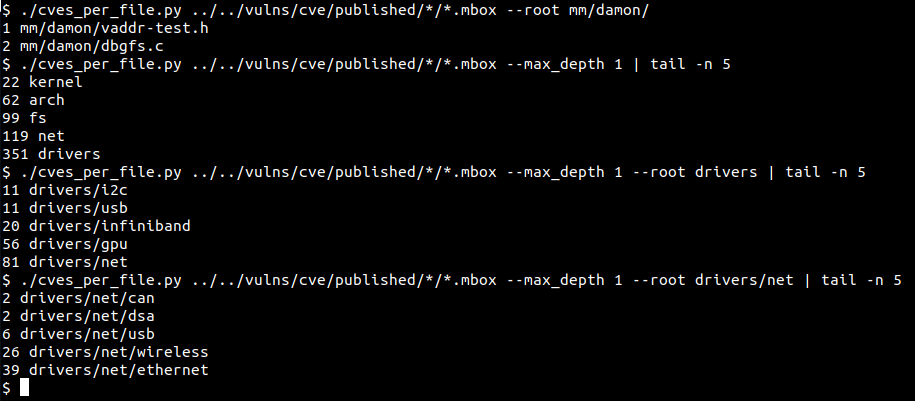
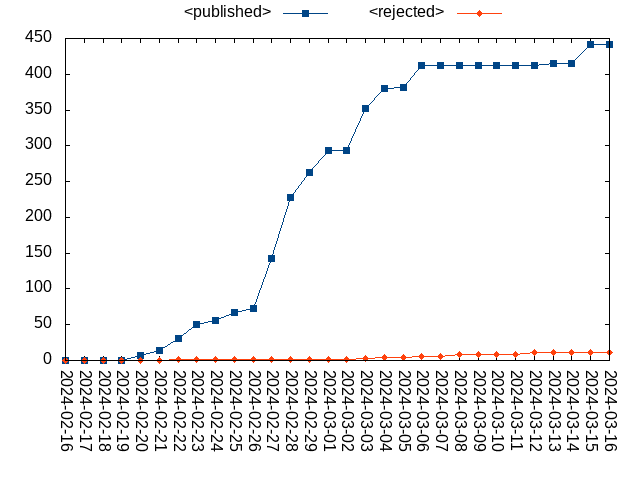
sjI wanted to know simple daily Linux kernel CVE statistics just for fun, so wrote a script[1] and plotted the output.
$ ./vulns_stat.sh ./vulns/ 30 | ../gnuplot/plot.py --data_fmt table --type labeled-lines --xtics_rotate -90 cve_stat_30_days.png
[1] https://github.com/sjp38/lazybox/blob/master/cve_stat/vulns_stat.sh
sj
sj[1] https://social.kernel.org/notice/AfkOGGMJWyDFsvYXdA
[2] https://github.com/sjp38/lazybox/blob/master/git_helpers/relstat.py
#linux #kernel #release_stat
sj
sjMemory management subsystem pull request[1] for Linux 6.9-rc1 has been posted. To quote Andrew’s summary for DAMON part:
- More DAMON work from SeongJae Park in the series
- “mm/damon: make DAMON debugfs interface deprecation unignorable”
- “selftests/damon: add more tests for core functionalities and corner cases”
- “Docs/mm/damon: misc readability improvements”
- “mm/damon: let DAMOS feeds and tame/auto-tune itself”
[1] https://lore.kernel.org/all/20240313200532.34e4cff216acd3db8def4637@linux-foundation.org/
LWN.net is now @LWN@lwn.net
LWN@fosstodon.orgThe 6.8 kernel has been released https://lwn.net/Articles/964784/ #LWN
sj
sj[1] https://events.linuxfoundation.org/lsfmmbpf/
[2] https://lore.kernel.org/damon/20240129204749.68549-1-sj@kernel.org/
#linux #kernel #damon #lsfmm #lsfmmbpf
sj
sj[1] https://github.com/awslabs/damo/tree/v2.2.4
[2] https://github.com/awslabs/damo/blob/v2.2.4/USAGE.md#profile
#linux #kernel #damon #damo #profiling
sj
sj[1] https://pasalabs.org/papers/2024/Eurosys24_M3_Camera_Ready.pdf
[2] https://2024.eurosys.org/
#linux #kernel #damon #eurosys
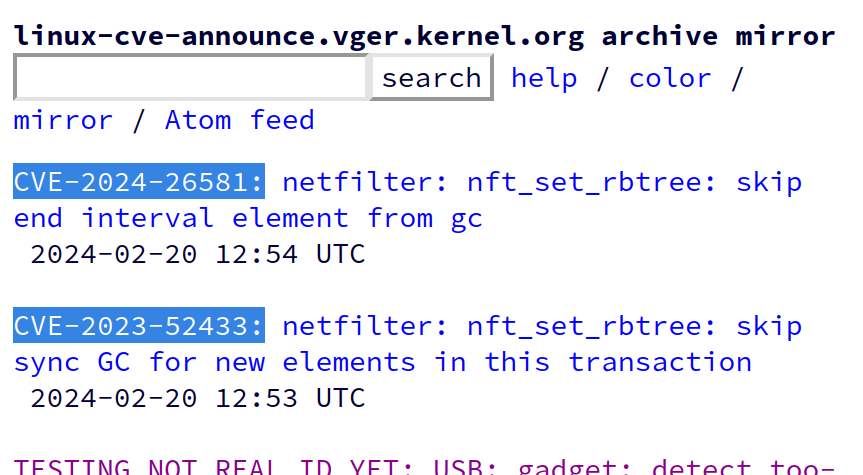
Thorsten Leemhuis (acct. 1/4)
kernellogger@fosstodon.orgThe #Linux #kernel CVE team released their first two CVEs:
* CVE-2023-52433: netfilter: nft_set_rbtree: skip sync GC for new elements in this transaction
https://lore.kernel.org/linux-cve-announce/2024022058-outsell-equator-e1c5@gregkh/
* CVE-2024-26581: netfilter: nft_set_rbtree: skip end interval element from gc
https://lore.kernel.org/linux-cve-announce/2024022024-uniquely-recluse-d893@gregkh/
For more details on the new #LinuxKernel CVE process, see https://docs.kernel.org/process/cve.html (recently added by https://git.kernel.org/torvalds/c/5928d411557ec5d53832cdd39fc443704a3e5b77 )
Screenshot from https://lore.kernel.org/linux-cve-announce/