sj
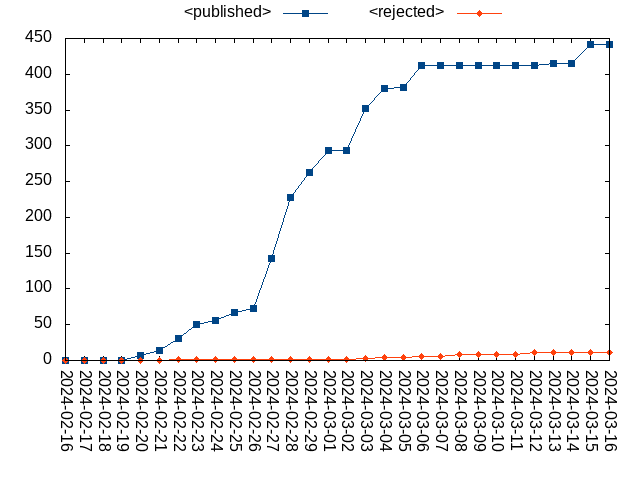
sjI wanted to know simple daily Linux kernel CVE statistics just for fun, so wrote a script[1] and plotted the output.
$ ./vulns_stat.sh ./vulns/ 30 | ../gnuplot/plot.py --data_fmt table --type labeled-lines --xtics_rotate -90 cve_stat_30_days.png
[1] https://github.com/sjp38/lazybox/blob/master/cve_stat/vulns_stat.sh
Issa
Issa@fosstodon.org@sj wow. so, that's 450 security bugs in one month? 😳 😳 😳 😳 . can you confirm pls? what kernel?
sj
sjIssa
Issa@fosstodon.org@sj am really shocked with no of bugs. linux is still far from being secure. but patching such high number is good & inevitable . what was the kernel that you scanned?
spmatich vk3spm 
spmatich@ioc.exchange
spmatich vk3spm 
spmatich@ioc.exchange
@sj @spmatich I don’t know if this *the* link, but it’s a link from synopsys a security product vendor. The post specifically links kernel CVE changes to NVD changes. So it seems at least some vendors have the position that the two events, Linux kernel having its own CNA team, and NVD stopped tagging CVSS, are correlated somehow