Greg K-H
gregkhGreg K-H
gregkhGreg K-H
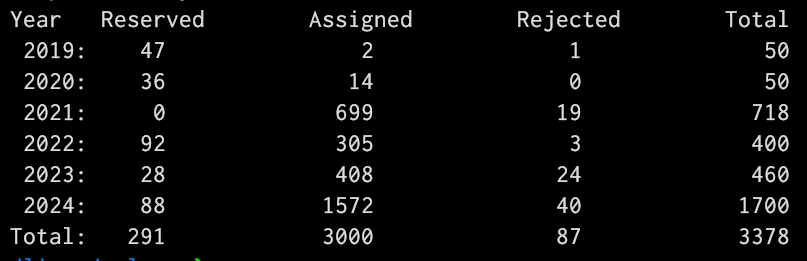
gregkhSorry to nit-pick, just wanted to be specific as 3000 in 6 months originally seemed like a lot to me before I went back and looked at these numbers.
Also, for those who want to play along on their own, just clone our vulns.git repo at git.kernel.org and look at the information directly there yourself, it's all being reviewed and assigned in the open, unlike other projects...
Brahms
brahms@chaos.social@kurtseifried @gregkh isnt that partly because the kernel devs are kinda trolling the cve community (or rather the weird corpos profiting of the community)?
I mean, every kernel bug is worth a cve, just update your stuff and you dont need to "manage your vulnerabilities"
Brahms
brahms@chaos.social@gregkh @kurtseifried @mathaetaes this must be a troll or a case of survivorship bias
Florencio Cano
florenciocano@infosec.exchangeA CVE does not mean a high risk. Companies should upgrade only when it's worth it, not only because there are known defects that could potentially be exploited. I totally agree companies should invest in automating upgrades, but not because there are many CVEs and always evaluating cost vs benefit.
Greg K-H
gregkhPavel Machek
pavelBrahms
brahms@chaos.social@gregkh @kurtseifried just to clarify: wasnt meant in a negative way.
This is something you have to do (as you made clear in your post back then), I personally just think that it is mostly work for you with little gain. The "trolling" was more a reference to the "every bug is a bug, [so its also a cve]" philosophy resulting in a huge amount of cve`s being created, maybe not the best wording on my site :s
Jérôme Petazzoni
jpetazzo@hachyderm.io@kurtseifried @gregkh that's ten CVE per day? 🤯 I know the kernel is a complex beast but that number feels totally bonkers
@kurtseifried While I can agree with "run current", note that as of now, my understanding is that *every* kernel bug gets a CVE. Every single one. No matter how remote a possibility exploitation of it would be. So the number of CVEs assigned maps fairly well to the number of bugs fixed; not to the number of actual *known* security issues.
Brahms
brahms@chaos.socialafter talking with a collegue about it I realized that im not the target group for this change, so I most likely misunderstood the reasoning behind it!
i will get back after listening through the episode, thanks for the link!
Greg K-H
gregkhAnd it's nice to see we aren't alone here with "big numbers", it's going to be an interesting thing to watch shake out as "take responsibility" rules/laws come into being in different locations. I agree with you in that the quantity is just going to get larger over time.
Thomas Depierre
Di4na@hachyderm.io@kurtseifried @gregkh @joshbressers I mean, they probably did, but we did not knew about it :D
Greg K-H
gregkhThomas Depierre
Di4na@hachyderm.io@gregkh @joshbressers @kurtseifried exactly. It is just that it takes time to get all the vulnerabilities shoved in your face
Jean-Baptiste Maillet
jbm@infosec.exchange@kurtseifried in this regard, I wonder about the plan of companies such as Red Hat or Canonical selling long term support.
(note: I don't know much about their exact offering, I'm into embedded stuff, building everything from sources anyhow.).