Posts
591Following
105Followers
121- Linux Kernel Developer @ Oracle (Linux Kernel MM) (2025.02 ~ Present)
- Reviewer for the Linux Slab & Reverse Mapping subsystem
- Former Intern @ NVIDIA, SK Hynix, Panmnesia (Security, MM and CXL)
- B.Sc. in Computer Science & Engineering, Chungnam National University (Class of 2025)
Opinions are my own.
My interests are:
Memory Management,
Computer Architecture,
Circuit Design,
Virtualization
A blog post I wrote about folios
Harry (Hyeonggon) Yoo
hyeyooDuring the COVID period, I've been taking computer science classes at university remotely while working on 42's assignments in person at 42 Seoul. (Yeah, that was quite intense!)
What I learned there wasn't knowledge itself, but how to approach problems I had never once thought about before, through discussions with peers. That learning process contributed greatly to my growth as an engineer in my early twenties (fun fact, hyeyoo is the nickname 42 gave me!).
These days, sadly, it feels like there are more and more people giving up on logical thinking (AI isn't going to replace logical thinking and problem solving skills, at least in the near future :/)
It's quite sad that 42 Seoul, a school that cultivated the ability to learn and think, and approach challenging problems, is closing its doors due to practical reasons.
[1] https://en.wikipedia.org/wiki/42_(school)
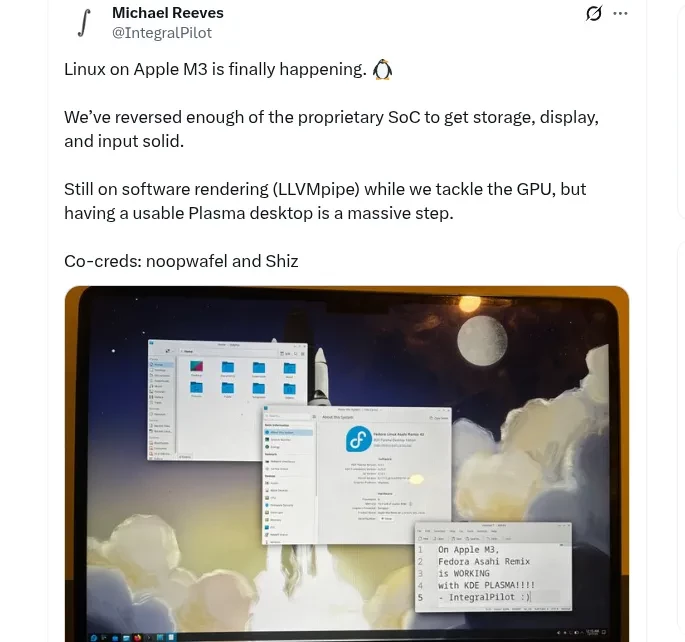
Phoronix
phoronix@masto.aiApple M3 Progress On Linux: Asahi Can Boot To KDE Desktop - But No GPU Acceleration Yet
While the Asahi Linux project has made good progress on bringing Linux to Apple Silicon hardware, much of the success and in turn upstreaming to the Linux kernel has been around the aging M1 and M2 Macs. Apple M3 and newer has been a struggle but progress is being made. One of the Asahi Linux developers shared the ability now to boot to the KDE Plasma desktop with the experimental As…
https://www.phoronix.com/news/Apple-M3-Linux-Boot-To-KDE
K. Ryabitsev-Prime 🍁
monsieuriconIf you're a Gmail or Outlook user and you're subscribed to high-volume mailing lists, you're probably routinely missing mail. Korgalore is a tool that monitors mailing lists via lore.kernel.org and can import mail directly into your inbox so you don't miss any of it. You can also couple korgalore with lei for powerful filtering features that can reduce the firehose to what you'd actually find useful.
https://people.kernel.org/monsieuricon/tracking-kernel-development-with-korgalore
Vlastimil Babka 🇨🇿🇪🇺🇺🇦
vbabka@mastodon.socialOnce again there's a kernel developer position open in the SUSE Labs Kernel Core team I'm part of! https://suse.wd3.myworkdayjobs.com/en-US/Jobsatsuse/job/Czech-Republic-EMEA/Linux-Kernel-Generalist_71007379
Harry (Hyeonggon) Yoo
hyeyooVlastimil Babka 🇨🇿🇪🇺🇺🇦
vbabka@mastodon.socialWith the current RAM prices, let me remind you of my solution from 2017 that unfortunately wasn't merged, but maybe it's time to revisit it? https://lore.kernel.org/all/20170401211813.15146-1-vbabka@suse.cz/
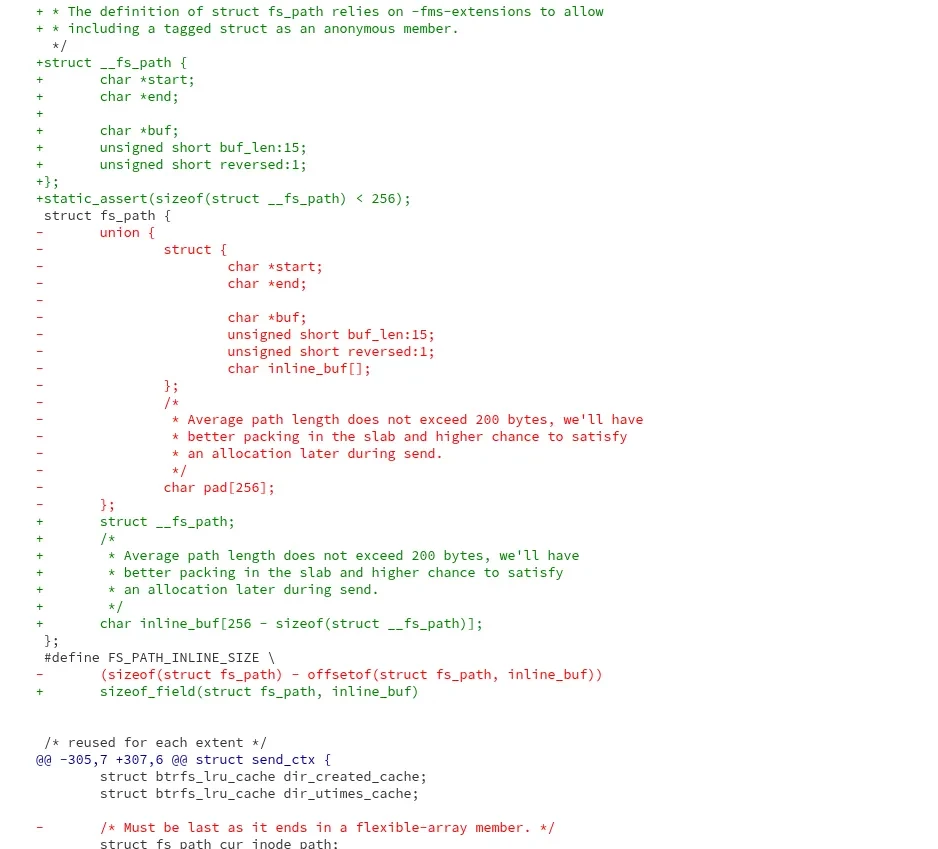
Phoronix
phoronix@masto.aiLinux 6.19 Goes Ahead And Enables Microsoft C Extensions Support
Last month I reported on Linux 6.19 looking to enable Microsoft C Extensions support throughout the Linux kernel with setting the -fms-extensions compiler option to allow Microsoft C Extensions when building the kernel. Linus Torvalds today merged that support without objections...
https://www.phoronix.com/news/Linux-6.19-Enables-MS-Ext
Harry (Hyeonggon) Yoo
hyeyooHope this is helpful when I'm testing something or reviewing complicated code
Wuzzy
Wuzzy@cyberplace.socialNew TLDs just dropped:
🌐 .com: community (discussion board)
🌐 .org: oranges, or the color orange, or both
🌐 .net: everything about nets EXCEPT computer networks
🌐 .gov: Grand ObserVatory. Astronomy-related
🌐 .mil: Moms in Love. Lesbian-friendly place
🌐 .int: Integers. Everything about one number, for example: 25.int
🌐 .edu: Ethylene diurea (an organic compund)
Vlastimil Babka 🇨🇿🇪🇺🇺🇦
vbabka@mastodon.socialRE: https://mastodon.social/@workchronicles/115534588198704665
This is how I present the lkp perf improvement reports for my patches, yeah.
Vlastimil Babka 🇨🇿🇪🇺🇺🇦
vbabka@mastodon.socialOh wow, what a loss for RH! https://lore.kernel.org/linux-mm/20251103103659.379335-1-david@kernel.org/T/#u
Vlastimil Babka 🇨🇿🇪🇺🇺🇦
vbabka@mastodon.socialOn Thursday, I sent this RFC: https://lore.kernel.org/lkml/20251023-sheaves-for-all-v1-0-6ffa2c9941c0@suse.cz/
On Friday, there was the expected phoronix coverage. But also an unexpected one:
https://www.nytimes.com/2025/10/24/learning/word-of-the-day-sheaf.html
Harry (Hyeonggon) Yoo
hyeyooA lot has happened in my personal life this week (nothing serious, don’t worry). Everything seems to be settled now thankfully.
I've found that often people ask advice and want a _certain kind of reply_.
Then I give my actual one and get ignored.
This is why I don't really bother replying to 'how do you get started in the kernel' type questions so much now :)
People want some dopamine hit 'inspirational' message that massages their ego.
And you can find ENDLESS fuckers on this site who will give you that, the type who wear fancy scarfs and never reply to anybody who is 'below' them.
But they're lying to you guys.
The truth is the truth.
I have the same experience when people ask about weight loss...
It's very much the case that holywood/internet versions of laudable qualities are in strict contrast to how they actually look.
Courage, persistence, resilience, strength are all extremely gritty, nasty, unpleasant things that often get you ostracised.
Much easier to kid yourself and live in some opium-fuelled dream of how the world is. But people don't seem to like to wake up to that :)