Posts
590Following
105Followers
121- Linux Kernel Developer @ Oracle (Linux Kernel MM) (2025.02 ~ Present)
- Reviewer for the Linux Slab & Reverse Mapping subsystem
- Former Intern @ NVIDIA, SK Hynix, Panmnesia (Security, MM and CXL)
- B.Sc. in Computer Science & Engineering, Chungnam National University (Class of 2025)
Opinions are my own.
My interests are:
Memory Management,
Computer Architecture,
Circuit Design,
Virtualization
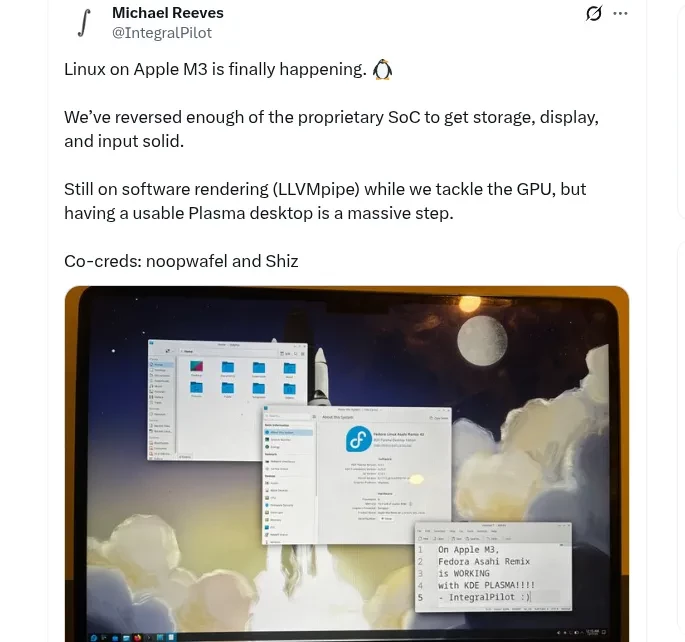
Phoronix
phoronix@masto.aiApple M3 Progress On Linux: Asahi Can Boot To KDE Desktop - But No GPU Acceleration Yet
While the Asahi Linux project has made good progress on bringing Linux to Apple Silicon hardware, much of the success and in turn upstreaming to the Linux kernel has been around the aging M1 and M2 Macs. Apple M3 and newer has been a struggle but progress is being made. One of the Asahi Linux developers shared the ability now to boot to the KDE Plasma desktop with the experimental As…
https://www.phoronix.com/news/Apple-M3-Linux-Boot-To-KDE
K. Ryabitsev-Prime 🍁
monsieuriconIf you're a Gmail or Outlook user and you're subscribed to high-volume mailing lists, you're probably routinely missing mail. Korgalore is a tool that monitors mailing lists via lore.kernel.org and can import mail directly into your inbox so you don't miss any of it. You can also couple korgalore with lei for powerful filtering features that can reduce the firehose to what you'd actually find useful.
https://people.kernel.org/monsieuricon/tracking-kernel-development-with-korgalore
Vlastimil Babka 🇨🇿🇪🇺🇺🇦
vbabka@mastodon.socialOnce again there's a kernel developer position open in the SUSE Labs Kernel Core team I'm part of! https://suse.wd3.myworkdayjobs.com/en-US/Jobsatsuse/job/Czech-Republic-EMEA/Linux-Kernel-Generalist_71007379
Harry (Hyeonggon) Yoo
hyeyooVlastimil Babka 🇨🇿🇪🇺🇺🇦
vbabka@mastodon.socialWith the current RAM prices, let me remind you of my solution from 2017 that unfortunately wasn't merged, but maybe it's time to revisit it? https://lore.kernel.org/all/20170401211813.15146-1-vbabka@suse.cz/
Harry (Hyeonggon) Yoo
hyeyoohttps://lore.kernel.org/all/20230401094658.11146-1-vbabka@suse.cz