Posts
5328Following
346Followers
529OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkko
In 2024, Octamed 8 was released after 25 year break. It's pretty amazing, at least to me, that there can be 25 year gap, and still have a vibrant and loyal following and committed user base.
Jarkko Sakkinen
jarkko
This my main UI reference or something I will taken now a lot of inspiration from at least because Octamed is superb and nice to use. And stands time just like Vim :-)
1. Octamed was made by a Finn Teijo Kinnunen.
2. Had major share on invention of such electronic music genres at their epoch such as breakbeat, jungle and drum'n'bass.
3. Still widely used as it does the job and has predictability unreachable on a signal chain with adaptive latency prevention algorithms, and especially with hardware samplers and such this makes ones life better.
4. I like it too a lot, it's great for what it does :-)
That is next 6 months at least because I want my tracker to level that I can do a full track with no other tools, and it is surprising how bottomless pit different usage patterns are (and not necessarily bugs, something just works or doesn't). And now that I actually have really good design and implementation for the engine it makes me less eager to less, it's fun to try things out :---)
#octamed #amiga
1. Octamed was made by a Finn Teijo Kinnunen.
2. Had major share on invention of such electronic music genres at their epoch such as breakbeat, jungle and drum'n'bass.
3. Still widely used as it does the job and has predictability unreachable on a signal chain with adaptive latency prevention algorithms, and especially with hardware samplers and such this makes ones life better.
4. I like it too a lot, it's great for what it does :-)
That is next 6 months at least because I want my tracker to level that I can do a full track with no other tools, and it is surprising how bottomless pit different usage patterns are (and not necessarily bugs, something just works or doesn't). And now that I actually have really good design and implementation for the engine it makes me less eager to less, it's fun to try things out :---)
#octamed #amiga
Jarkko Sakkinen
jarkko
Edited 8 days ago
Tracker will take some time and especially since I'm doing C rewrite, which is right now completely broken (literally a start from scratch).
However, the elegant C implementation will motivate me more as a developer as I enjoy it more, and thus will eventually get the project there.
With Rust implementation I know I would give up at some point. E.g., in this type of project you want to leave space for downscaling to very low-end computers, and more towards 80s/90s hardware we go, more opcodes cost relative to memory access costs. Thus I don't want compiler to do any memory safety stuff for instance. Software must have full control of generated opcodes.
The code base looks in style a lot like kernel code and utilizes its popular patterns such as ops structs and container_of macros. And coding style is of course kernel coding style.
However, the elegant C implementation will motivate me more as a developer as I enjoy it more, and thus will eventually get the project there.
With Rust implementation I know I would give up at some point. E.g., in this type of project you want to leave space for downscaling to very low-end computers, and more towards 80s/90s hardware we go, more opcodes cost relative to memory access costs. Thus I don't want compiler to do any memory safety stuff for instance. Software must have full control of generated opcodes.
The code base looks in style a lot like kernel code and utilizes its popular patterns such as ops structs and container_of macros. And coding style is of course kernel coding style.
Jarkko Sakkinen
jarkko
Edited 11 days ago
Old school file browsing experience :-) Rendered as a single GLSL shader program (except top and bottom bar). There's now 1:1 correspondence between shader programs and screens. Most importantly this stabilizes latency for each tick in audio playback (smaller CPU time variance).
#tracker #polyend #chiptune
#tracker #polyend #chiptune
Jarkko Sakkinen
jarkko
I really enjoy working on this tracker project. When I got pattern editor, I knew that it will become something. It will take at least a year to really nail every bit but it has the critical mass of getting done (eventually) :-)
Very early work on sample editor.
Very early work on sample editor.
Jarkko Sakkinen
jarkko
Edited 17 days ago
also has polyend's 8 channel view :-) in this view text fields need some work but yeah looking pretty good
Jarkko Sakkinen
jarkko
Edited 19 days ago
it's glitchy atm because heavy changes how pattern editor is rendering but getting there ;-) music courtesy of 4mat - red sector theme
Jarkko Sakkinen
jarkko
Moxie seems to be only person in the planet nailing login like it was 2021 :-)
Linear email-link-passkey track.
First time I witnessed this like it should be done everywhere really since five years ago.
Linear email-link-passkey track.
First time I witnessed this like it should be done everywhere really since five years ago.
Jarkko Sakkinen
jarkko
Edited 1 month ago
Test code I have cleaned up relocated:
https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/vcam-test.git
From this i spin off at least some kind of initial kselftest.
https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/vcam-test.git
From this i spin off at least some kind of initial kselftest.
Jarkko Sakkinen
jarkko
Edited 1 month ago
Here vcam-test outputs to /dev/vcam and in sequence streams /dev/video0 and renders the output to KMS/DRM initialized frame buffer.
I need to flatten the ioctl interface of /dev/vcam a bit but otherwise this is looking pretty reasonable...
I need to flatten the ioctl interface of /dev/vcam a bit but otherwise this is looking pretty reasonable...
Jarkko Sakkinen
jarkko
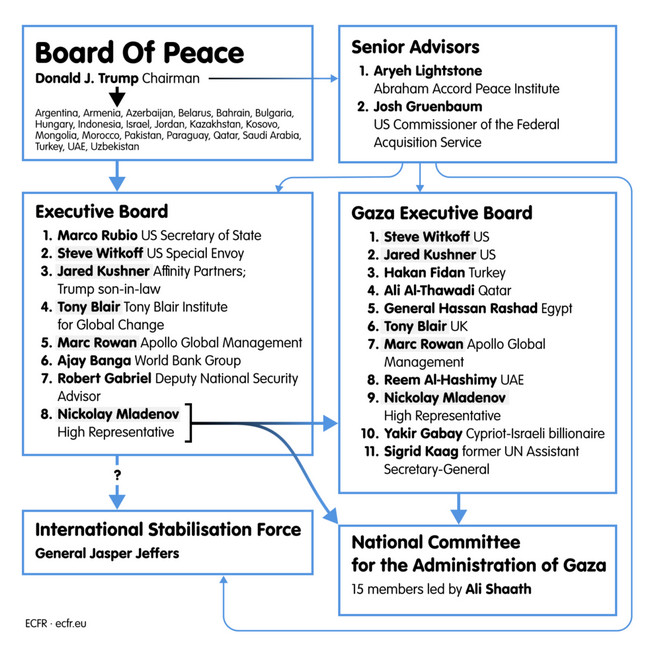
lol, who would guessed: tony blair is in the executive board
... and trump just called brits who participated to Nato wars as "losers"
🇬🇧
... and trump just called brits who participated to Nato wars as "losers"
🇬🇧
Jarkko Sakkinen
jarkko
Edited 1 month ago
shout out both to my personal friends (which there are many) in denmark, and also danish colleagues and collaborators in open source!
#denmark #greenland
#denmark #greenland