Posts
4949Following
329Followers
495OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkoJarkko Sakkinen
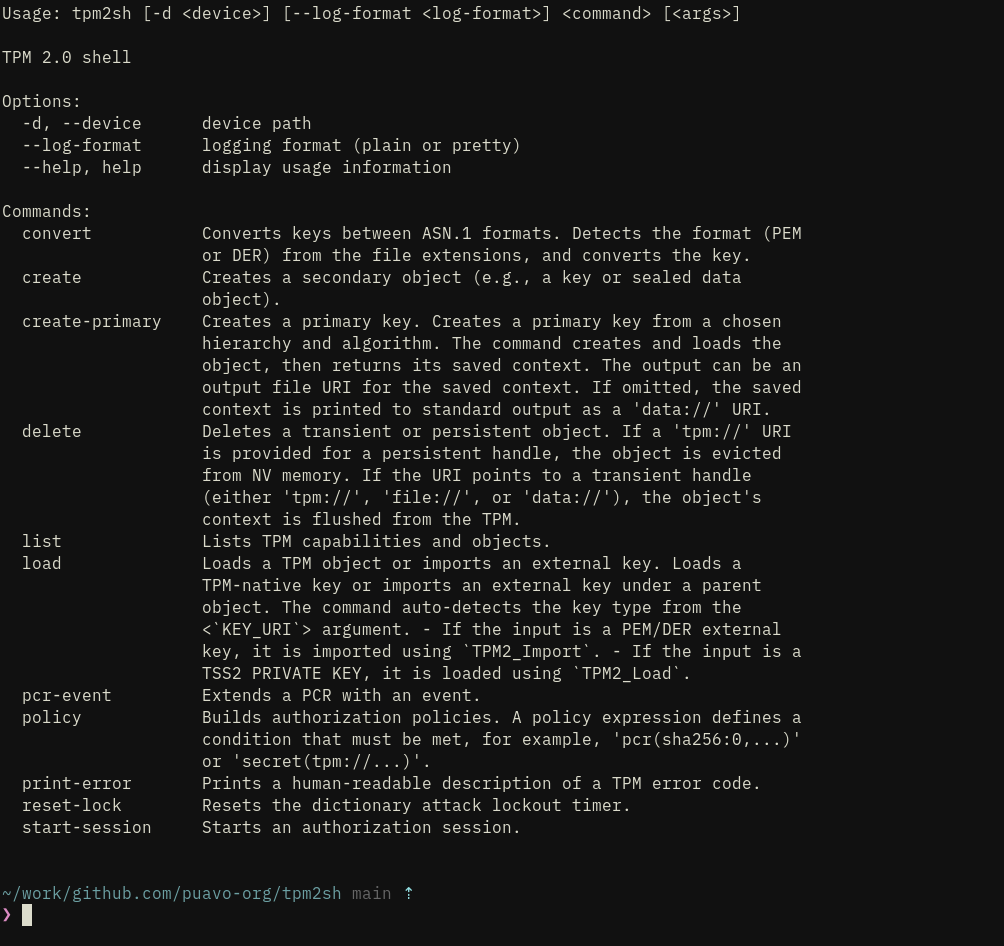
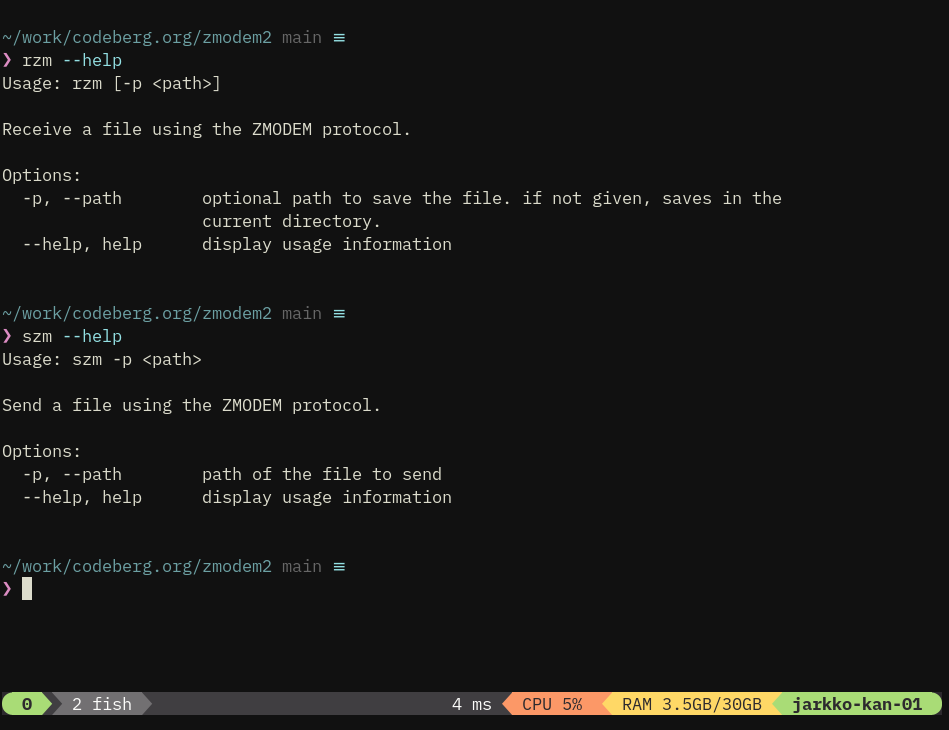
jarkkotpm2sh 0.11.16
This is the release where things mostly work and is first usable version for wider audience than just me.
Functionality is focused on key management and it is quite limited on operations.
That said, it the most important functionalities, and most difficult to implement, in place:
- Implicit creation of HMAC sessions to protect communication, and hiding its complexity . It is still a stub as parameter encryption is not in place but the mechanism is working correctly.
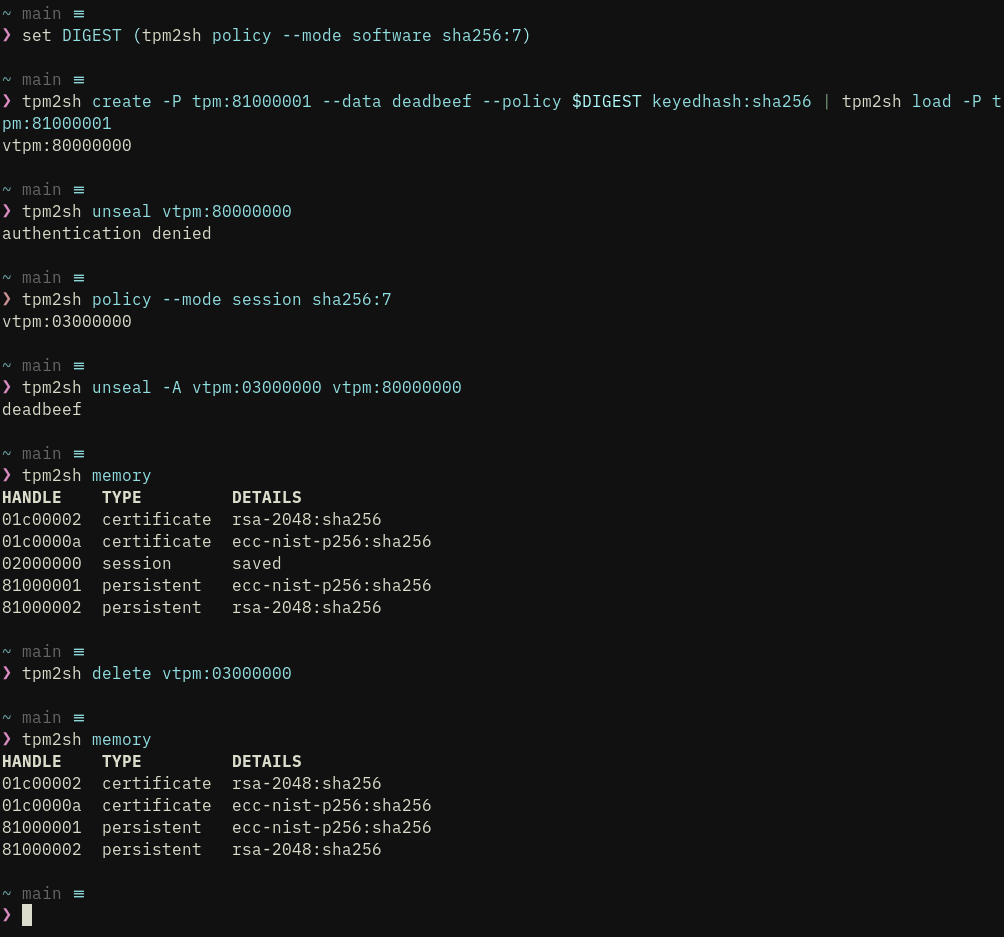
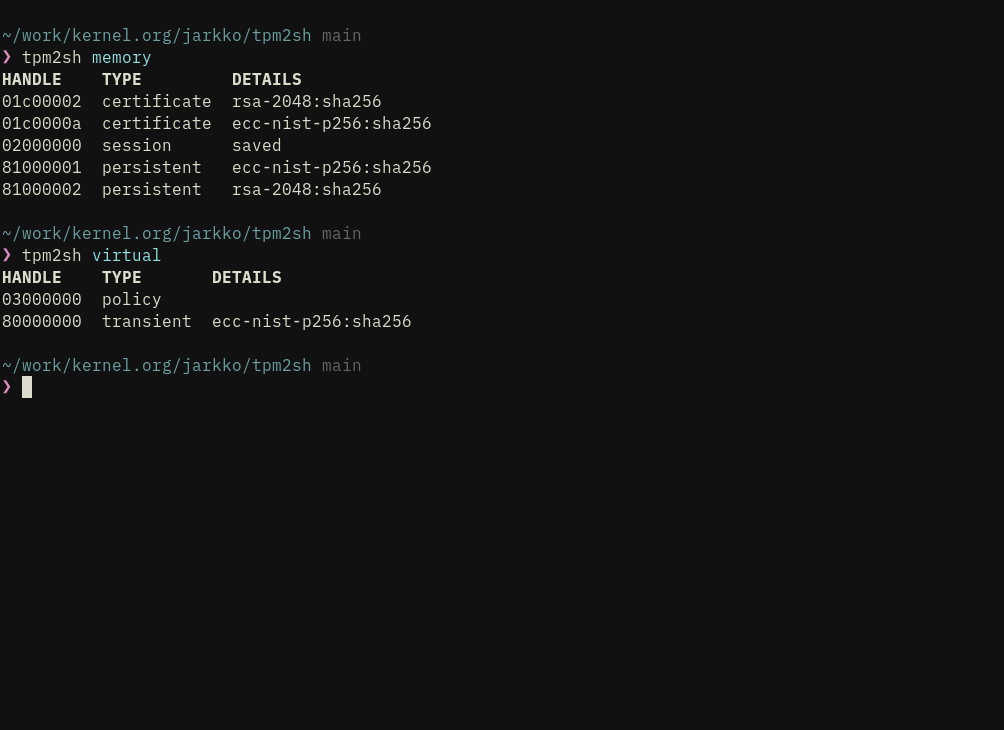
- Key management including direct support for PKCS#1, PKCS#8 and SEC1 external keys with custom parsers so that dependencies are light for e.g., BuildRoot embedded/VM targets. 3, Seamless over-subscription with key context cache (in ~/.cache/tpm2sh). Detects stale contexts from previous power cycles. “Cache keys” can be referred bit “key:<hex grip>” type of “URI”, where grip is 8 bytes of the key’s name hash.
- Seamless policy sessions with policy command, which can output both composite digest and session handle.
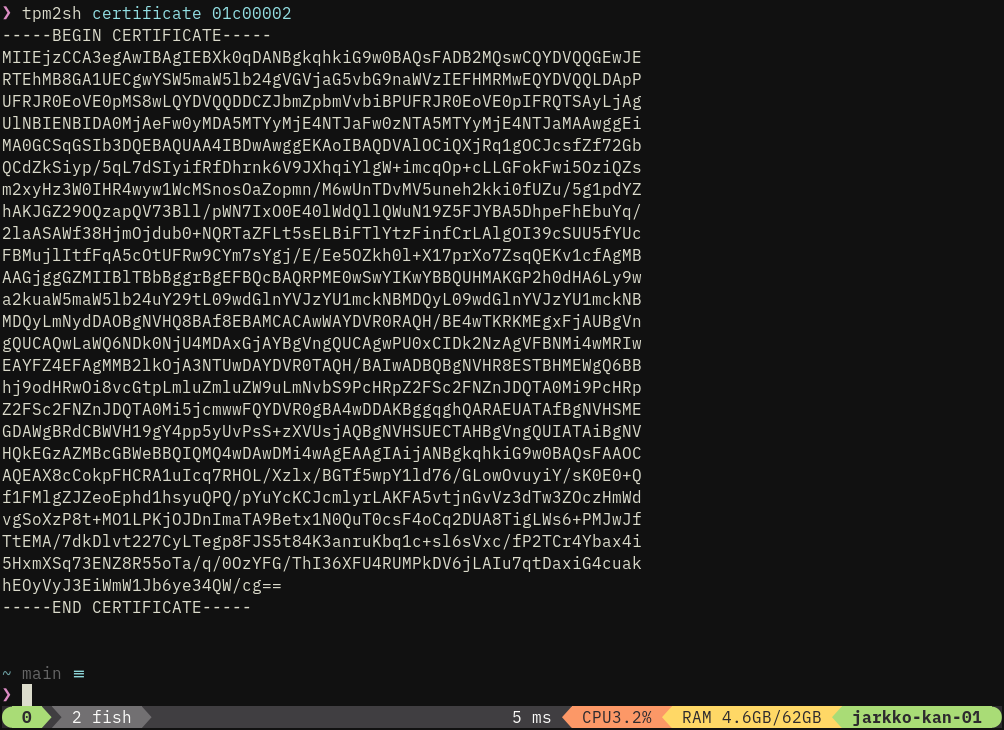
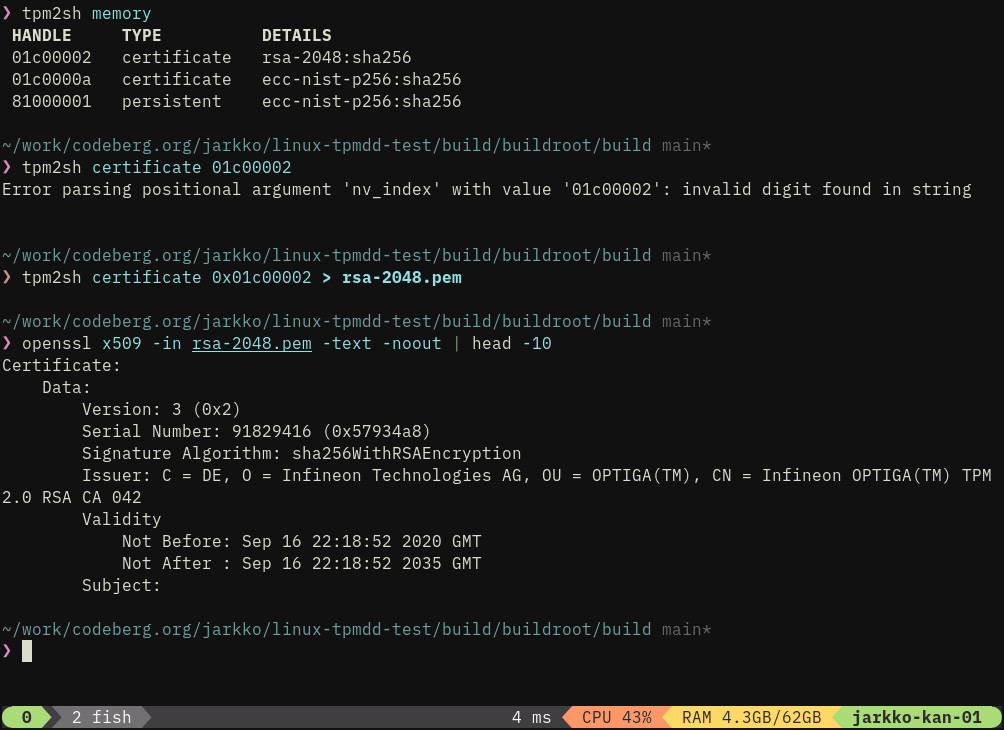
- Intuitive way to download vendor certificates from the chip.
- Full support for the TPMKey ASN.1 format, which is what kernel speaks.
Adding signing etc. ops would have been worse mistake to do before getting this basis right.
It’s not aiming to do all what tpm2-tools does but more like do stuff that I want to do and implementing that as a command-line tool :-) I.
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkko#buildroot
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkohttps://github.com/puavo-org/tpm2sh/issues/2
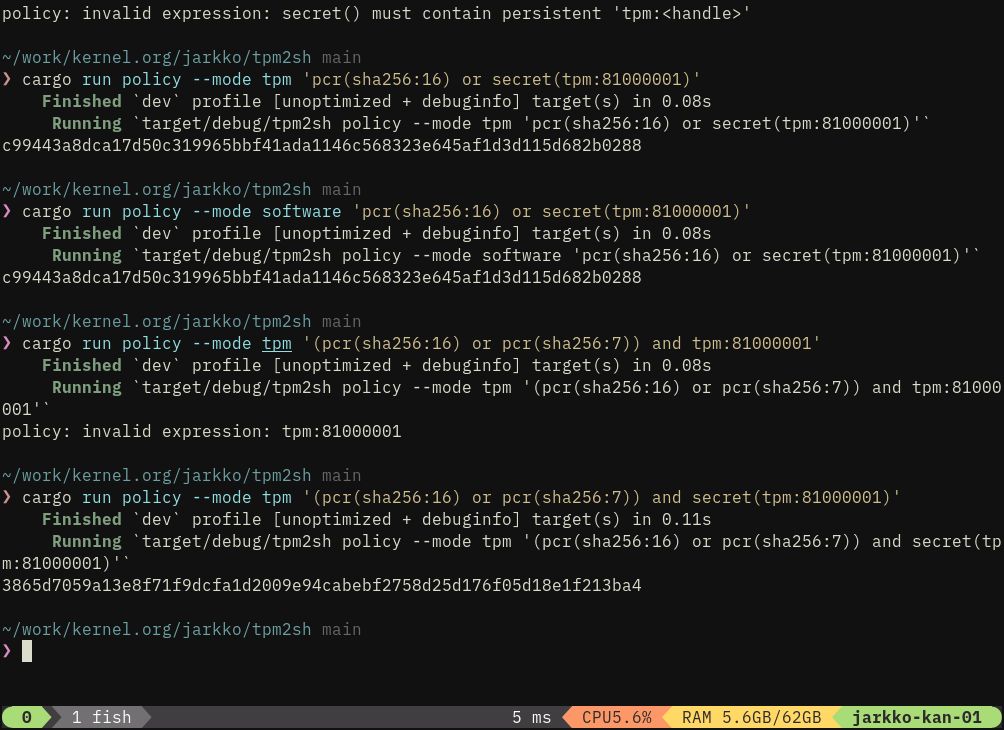
Many of the things are just minor collapses while turning this over and over again. Sessions need still a bit of work but lot of the functionality is already there...
I'd like to add quote generation etc. for Remote Attestation purposes but it is definitely out of scope and better just to stabilize the command set.
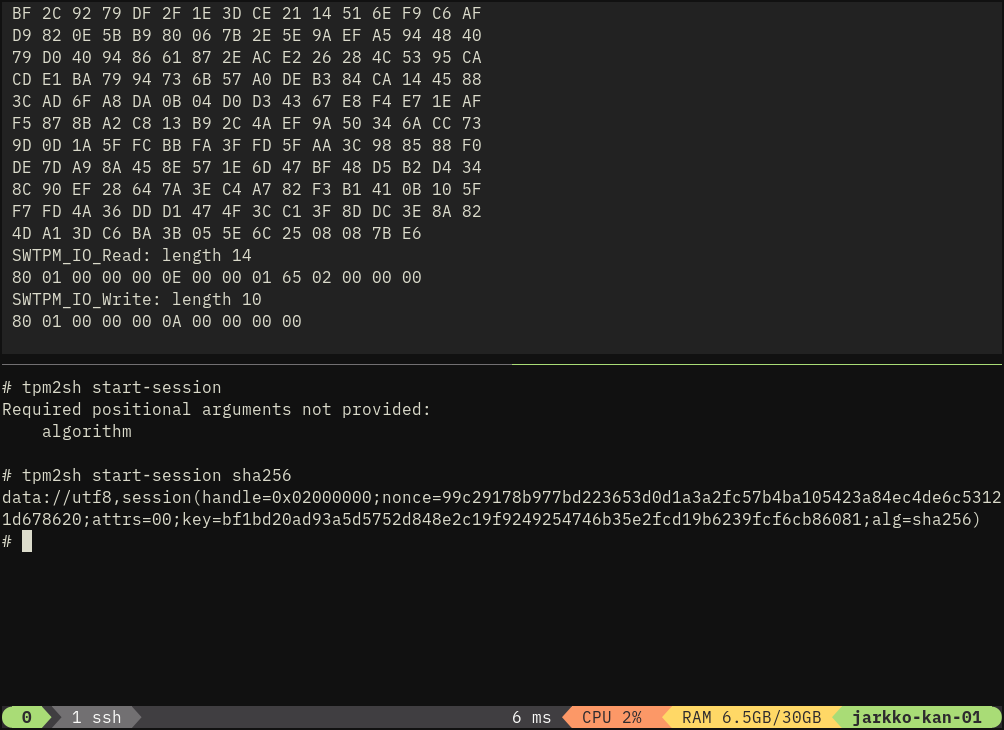
Sessions are represented like this (to be cosmetic tweaked in some places):
session://handle=0x02000000;nonce=135eac83db00e0c691fba1653405e79f8f285964e18add0488337fc7caf90606;attrs=00;key=;alg=sha256
And there's already `--session` argument but further I'll add an environment variable TPM2SH_SESSION, which command not only read but also update (to enable chaining e.g., nonce needs to be updated).
The general gist and main goal of the command set and "command-line experience" is to enable both user interactive experience and also TPM2 access for shell implemented tools such as password managers.
Load loads both external PKCS#8 and TPM ASN.1. Convert command converts PKCS#8 to TPM ASN.1.
So instead of this:
tpm2_createprimary --hierarchy o -G rsa2048 -c owner.txt
tpm2_evictcontrol -c owner.txt 0x81000001
openssl genrsa -out private.pem 2048
tpm2_import -C 0x81000001 -G rsa -i private.pem -u key.pub -r key.priv
tpm2_encodeobject -C 0x81000001 -u key.pub -r key.priv -o key.priv.pem
openssl asn1parse -inform pem -in key.priv.pem -noout -out key.priv.der
You can just:
tpm2sh create-primary rsa:2048:sha256 --output file://owner.txt
openssl genrsa -out private.pem 2048
tpm2sh convert --parent "tpm://0x81000001" file://private.pem --output file://key.priv.der
#linux #rust #tpm
Jarkko Sakkinen
jarkko1. last year it was 70th anniversary of twin town friendship between tampere and kiova (tampere is my hown town).
2. kiova has a street called "tampere", which was named in 2014 to celebrate 60th anniversary of friendship, which has lasted well over its "soviet origins".
my generation does not know what it is like to be at war obviously and it would be obnoxious to say that "i get it" when it comes to war at ukraine. however, we owe to our grandparents to not forget, not make compromises and generally not to be ignorant of the situation.
🇺🇦 🇫🇮
Jarkko Sakkinen
jarkkoThe current feature set of upcoming tpm2sh 0.11. It’s quite basic but everything is tested with care and e.g., load does all the import dance for PKCS8 RSA and ECC keys without having to mess with openssl command line. I.e. single robust load command instead of:
tpm2_createprimary --hierarchy o -G ecc -c owner.txt
tpm2_evictcontrol -c owner.txt 0x81000001
openssl ecparam -name prime256v1 -genkey -noout -out private.pem
tpm2_import -C 0x81000001 -G ecc -i private.pem -u key.pub -r key.priv
tpm2_encodeobject -C 0x81000001 -u key.pub -r key.priv -o key.priv.pem
openssl asn1parse -inform pem -in key.priv.pem -noout -out key.priv.der
And generally flows are somewhat polished and will be polished further before released to not have any rough corners. Finally most of non-trivial functionality is tested against built-in TPM emulator MockTPM.
Sometime after 0.11 release I’ll add also --dry-run switch that can exercise TPM commands with the emulator before applying them to the chip.
Jarkko Sakkinen
jarkkoIn the end of the day this is superior despite adding up a new trick to my sack of random macro hacks:
tpm_integer!(u8, TpmUint8, Unsigned);
tpm_integer!(i8, TpmInt8, Signed);
tpm_integer!(u16, TpmUint16, Unsigned);
tpm_integer!(i32, TpmInt32, Signed);
tpm_integer!(u32, TpmUint32, Unsigned);
tpm_integer!(u64, TpmUint64, Unsigned);
Now the names match TCG specification names, and they are also first fully zerocopy migrated types. This way previously redundant looking field now is actually self-documenting field.
Other zerocopy types will get the nasty “Cast” postfix up until migration is complete (e.g., TpmBufferCast).
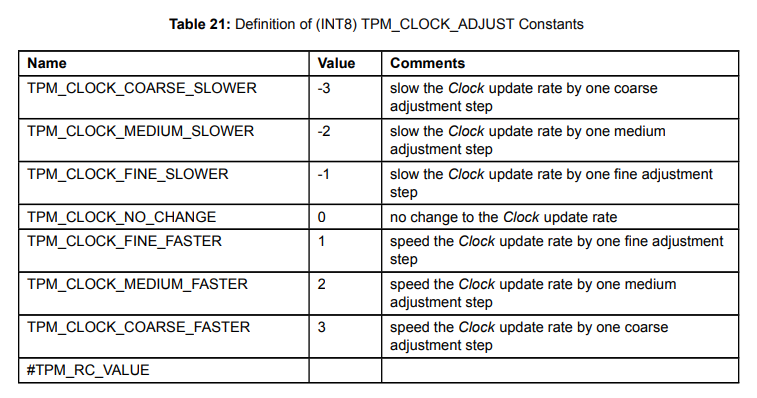
For the record, the last field is used to address exactly one quirk related to TCG specs: TPM_CLOCK_TIME, meaning that “invalid discriminant error” needs too versions :-/
I’m sure we would get numbers going from zero to six, and “get this complex science” as e.g., most of have ability to read, and understand nuances such as the difference between slower and faster… This is DailyWTF proximity enough level bad definition that I tend to like that TPM_CLOCK_TIME exist…
Jarkko Sakkinen
jarkko- Text files are more readable than code generation (unless you are a compiler).
- Text files has factors better outreach than code generation.
- Text files are non-executable read-only data.
- A bug in a static text file is a typo. Typo is a distraction for sure, but it does not radiate software bugs.
- The factor it simplifies command argument processing is much heavier than some minor redundancy that using text files introduces.
- Text files can be read without building a project.
#rust #clap #lexopt
Jarkko Sakkinen
jarkkoLast fix: https://github.com/puavo-org/tpm2sh/commit/3627530516fdcc8739b3c7aea6fab6a136201bfa
It's a bidirectional test where both the client and the emulator are based on tpm2-protocol. The other side sends commands and parses responses, and the other side send responses and parses commands.
Given the fair amount of software crypto involved to perform any possible bidirectional handshake it is shows off pretty well how robust the implementation is.
#rust #tpm #linux
Jarkko Sakkinen
jarkkoNow that I don't do active development on tpm2-protocol, I'm going to make the first actually somewhat stable 0.11.0 release of tpm2sh.
It has quite verbose interface, which will break also easily for that reason. Thus, before pursuing seriously to the possible bugs, I developed MockTPM, a simple TPM emulator that is used as the "TPM end" for subcommand integration tests..,
#linux #kernel #rust #tpm