Posts
5080Following
332Followers
504OpenPGP: 3AB05486C7752FE1
The Tor Project
torproject@mastodon.social📣 Attention all change-makers! Join our mission to protect online privacy and freedom by applying for one of our exciting open positions. You will contribute to a meaningful cause while growing professionally in a supportive and collaborative environment. 🚀💪 Don't miss out - apply now and be a part of something bigger than yourself! https://www.torproject.org/about/jobs/
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoEven if that causes a few additional calls around the hooks call site, it removes abstraction shenanigans and other unnecessary boilerplate code, and thus makes reading and debugging kernel code overall more pleasing experience.
E.g. documentation [1] states that "the Linux capabilities modules will always be included" but really does not gives existential reason for abstracting it that way. Maybe there are legit reasons for doing that but they are undocumented and I get a feeling that i'm in a spaceship with a bunch of architecture astronauts :-) [2]
[1] https://www.kernel.org/doc/html/latest/admin-guide/LSM/index.html
[2] https://www.joelonsoftware.com/2001/04/21/dont-let-architecture-astronauts-scare-you/
Jarkko Sakkinen
jarkkoI’ve understood by reading LKML and LWN that the problem that nested LSM’s is trying can be described as follows:
- Host is using LSM A.
- Container is using LSM B.
Given that the most of the popular LSM’s are made for the sake of SELinux being too tedious to configure I’ve sometimes wondered why they could not just convert their policy to SELinux policy, and not be kernel features in the first place 🤷
That said, LSM’s are not my area really, and could easily overlook some aspects that might make them useful as kernel features.
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoThorsten Leemhuis (acct. 1/4)
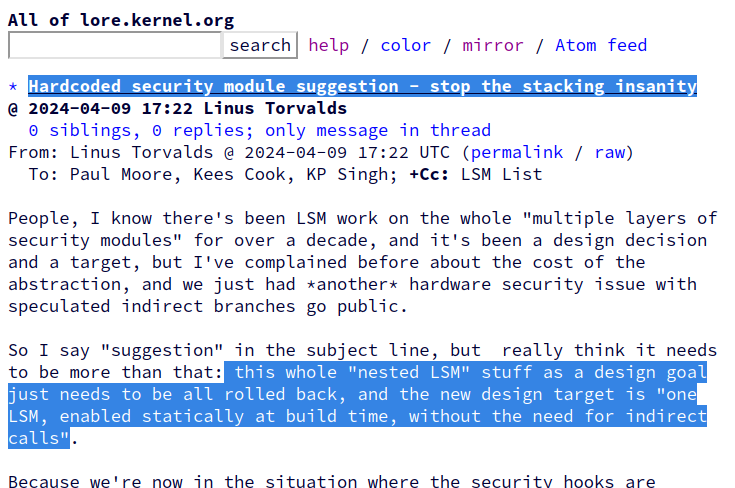
kernellogger@fosstodon.orgHardcoded security module suggestion - stop the stacking insanity
"'[…]this whole "nested LSM" stuff as a design goal just needs to be all rolled back, and the new design target is "one LSM, enabled statically at build time, without the need for indirect calls."
Because we're now in the situation where the security hooks are actually a source of not just horrible performance issues, but also actual insecurity[…]"'
Thorsten Leemhuis (acct. 1/4)
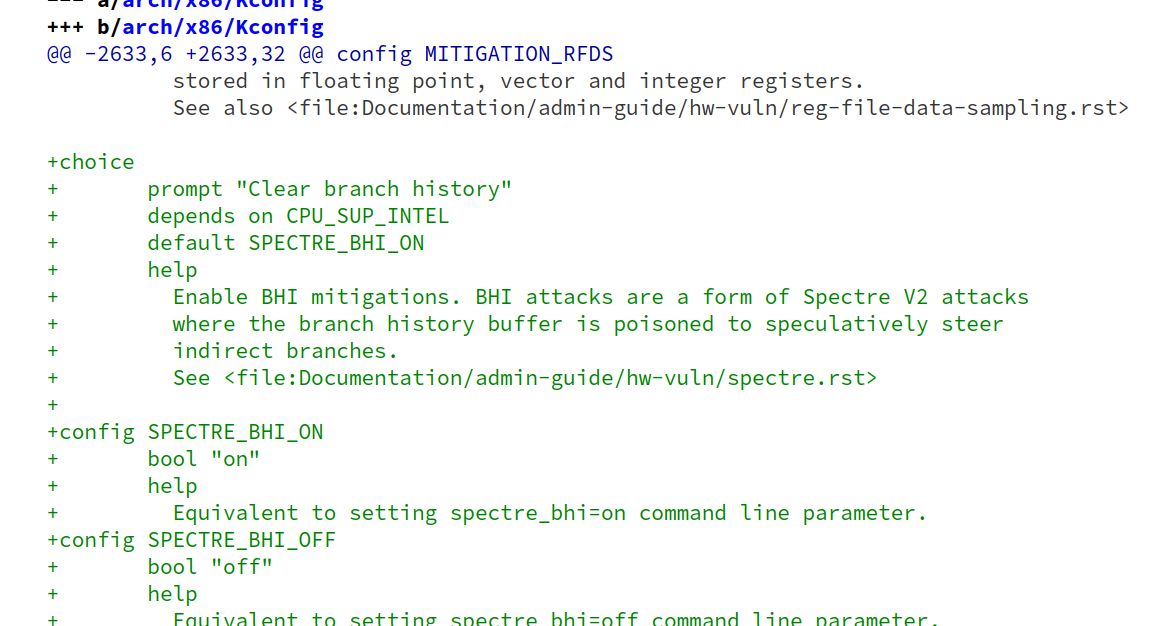
kernellogger@fosstodon.orgMitigations for the "native BHI(Branch History Injection)"[1] hardware vulnerability have just been merged into #Linux mainline: https://git.kernel.org/torvalds/c/2bb69f5fc72183e1c62547d900f560d0e9334925
"'BHI attacks may allow a malicious application to influence indirect branch prediction in kernel by poisoning the branch history. […]"
[1] for details, see https://www.vusec.net/projects/native-bhi/
Jarkko Sakkinen
jarkkoDo not need anything too high end, as long as the durability and overall quality are acceptable...
Jarkko Sakkinen
jarkkohttps://www.amazon.de/dp/B0CSD529PW?psc=1&ref=ppx_yo2ov_dt_b_product_details
The USB HAT with UART-micro-USB bridge I got is https://www.amazon.de/dp/B072Q5S1XH?psc=1&ref=ppx_yo2ov_dt_b_product_details. I ordered couple of these (other for raspberry pi 400).
huge workflow improvements with less than 100 EUR investment :-)
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoAccording to the news, he has to report to the police every other day, and is only allowed to move in a restricted area in the city of Espoo. So if he wants to escape, he has 48h of time window to do that, no idea if he is under surveillance or not.
BrianKrebs
briankrebs@infosec.exchangeA Finnish court has decided to let alleged mass extortionist Julius "Zeekill" Kivimaki free pending the rest of his trial, without even an ankle bracelet. This is a guy who was hiding in France under an assumed name and passport when police arrested him and sent him back to Finland to face charges that he extorted thousands of patients of the Vastaamo psych practice in 2020.
https://www.hs.fi/kotimaa/art-2000010206299.html
"The processing of the data breach and blackmail case is scheduled to continue on Wednesday at 9 o'clock.
"The trial will continue, even if he doesn't show up," Vainio formulates Kivimäki's arrival for the upcoming hearings."
They've taken away his passport, but it's not hard to walk out of Finland. Hope they're following him around wherever he goes.
https://krebsonsecurity.com/2023/11/alleged-extortioner-of-psychotherapy-patients-faces-trial/
Jarkko Sakkinen
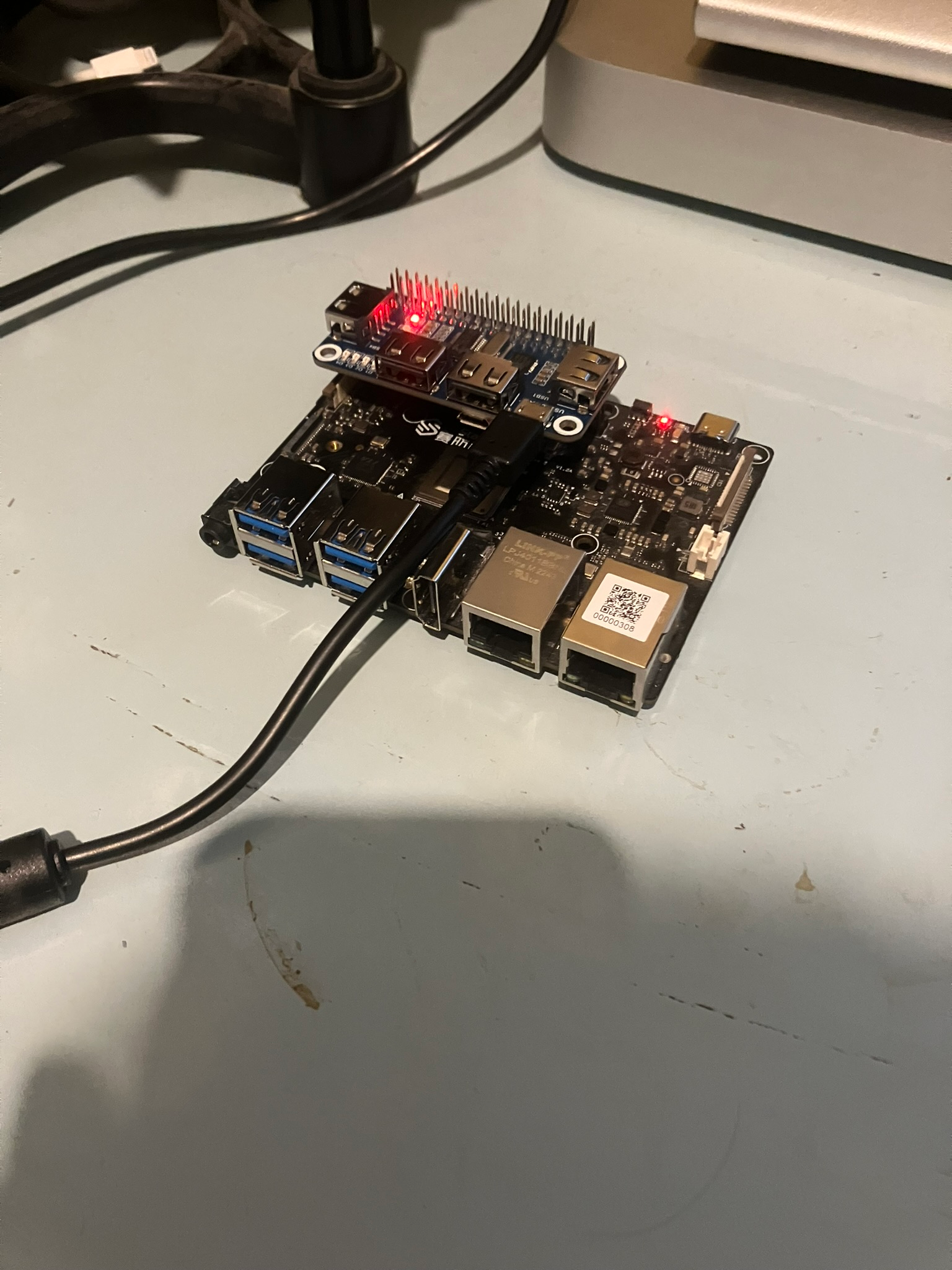
jarkkoOverall I think VisionFive2 is overall better board than e.g. BeagleV for kernel development tasks because:
- 2/3 of price
- twice more memory at least in the 8GB version
- Hat that can supply power and UART through micro-USB is about half price of comparable mikrobus and the overall setup is more compact in price.
I had no idea how the CPU’s compare but for my tasks I neither care :-) I guess they help each other to mature in Linux kernel because the hardware platform are from the same family (jh7100 for beaglev and jh7110 for visionfive2). For some other task, e.g. building something around the SBC, the evalution might different.
I came to these conclusions based on working with VisionFive2 and I do not have BeagleV at my hands so that my cause some dilation but at least this board feels like better bang for the buck.
Still would love to get my hands on BeagleV too and get more familiar with it, and yeah, competition is a great thing, and can’t wait for more Beagleboard RISC-V products.
#riscv #visionfive2 #beaglev #beagleboard #raspberrypi #mikrobus
Jarkko Sakkinen
jarkkoSuper-nice additional benefit of this shield: one cable less. Before I needed power cable and USB-TTL for TTY. Now only by connecting micro-USB to the shield it draws the power and provides serial access.
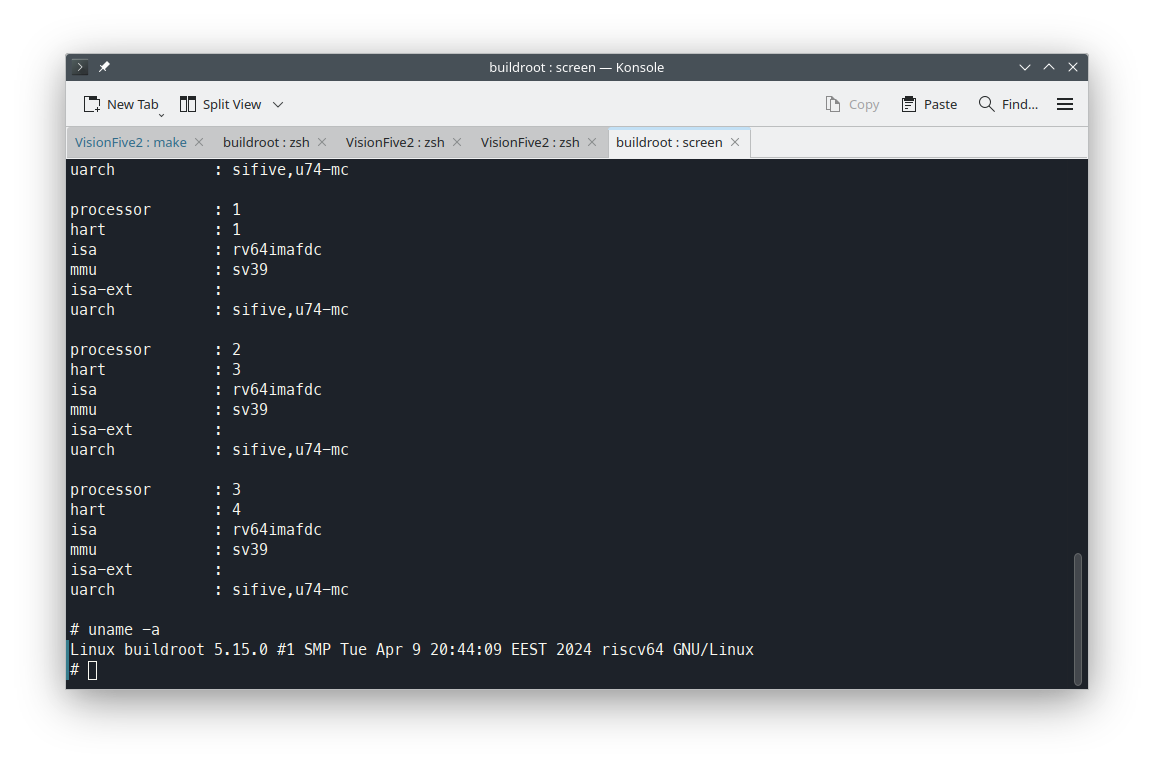
The screenshot has unmodified #BuildRoot master branch version built with visionfive2_defconfig. Seems to be much more stable than lean, at least for the kernel development, than the official SDK, which is quite scary looking construction tbh :-)