Posts
5062Following
330Followers
505OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkoDo want to slander our neighbor nation but I’m bit skeptical towards claim that Estonia had its first blockchain in 2007.
Bitcoin paper came out in 31st of October, 2008, so possible conclusions:
- Bitcoin was not the first blockchain like within the metrics for such data structure that the paper defines.
- KSI has some of the characteristics of those defined in the original Bitcoin paper but is not an “actual” blockchain.
Without better knowledge, bullet 2 is pretty good base assumption. Or who knows, perhaps Satoshi Nakamoto is an Estonian citizen or a group of citizens.
Jarkko Sakkinen
jarkkoI want to my own so called wallet and looking at options of hardware incorporation:
- TPM2: not feasible since does not handle P256K1 (only P256R1).
- Hardware crypto wallets (from companies like Ledger): in my opinion worst inventions done during past 20 years. We need open and application agnostic keystore backends, not pollution like these.
- FIDO2: Yubikey very compelling collection of crypto algorithms and ECC curves, including popular ones for blockchains.
So the choice is somewhat obvious based on this quick feasibility study: I want a FIDO2 wallet.
The next issue. I found this really nice FIDO2 wallet in C++: https://github.com/hoytech/defido2
My next question would be tho does anyone know is the choice of implementation language in this driven by “passion” or something actually preventing to do this using W3C API’s for FIDO2?
Does W3C API e.g. block some ECC curve types that my Yubikey might support?
Jarkko Sakkinen
jarkkoMeaning that even my in progress patch set can sign those when the private key is managed by a TPM chip [1]. Anyway good to know.
[1] https://lore.kernel.org/linux-integrity/20240528210823.28798-1-jarkko@kernel.org/T/#t
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoStumped into a bug straight out right in the get-go ;-) It goes like this…
First, consider:
❯ cat pubkey.txt
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC3un58bzSwrEXD5PMNuT9nYhyBfdiEeDrcQd3Facw9PZihlFwfec+iz00u4bbNmcrG0YhT056PSnqIR4DqGSK3N2iancS1anBfgNS7Se02jcOyoHsgrDFH6MxEgkZLoFY8XodE5NPDGt6rPoiy6MeN0jKNvuMMQ9UFge67ky0pWZjyDjdyXERZWEIjcp+OQXMaFAU3zJCbnaLgVn7CizZcwriu2ElMg0tVvxdkW59QW9dSgmCdF4zwSvLN6XVpaCw+fiXV+09Wq5PT65qT/rWC/0yO4BWuZFteX8gXyDQBJqEzNKjkvACNFI4ublSUQO7zYnyFQjlww04+afTFkWZYIV2UtOZYzJaTg90DT3fQBkJMxsHHc4G8eF+SveIy1tiOq7jf8btvdKLCyvIrNMlhB99YPAzBFUd/X/w7uOEtm7L4zoWa+6YRjtKiPtuaeGGQVr3CEU/L9rtPY9PfkPOxGUahnM5M2MsST5NPZ9+tWvhjEFX4nSYo5EShFBE9m01sa675mzrOwsBXwi7AlBZtT4hEYN1jvVUVXrwEC8W7RKy3C0mgU/mlnxXHp23af9YEkjiYA5ZBmK4+q85o0pBf616cLAhzebDwoT5v9VkYY+q1t3nLWpaG9HAH0BmPyEW0jlB1jxqwUvlmWQ14vtZUOAzrFnAoUKDVLTeuK+w5vw== cardno:23_610_166
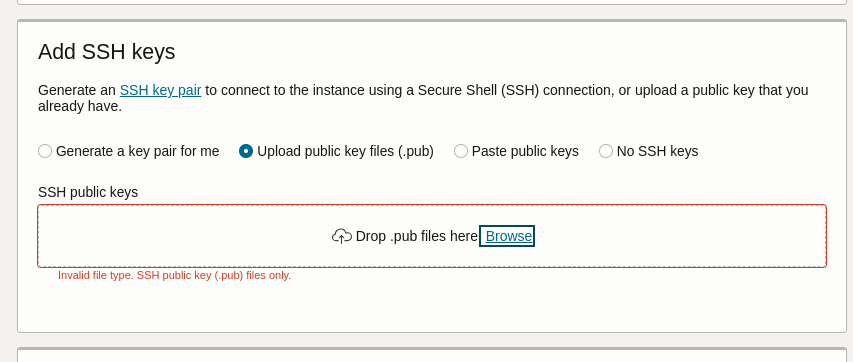
Uploading this results “Invalid file type. SSH public key (.pub) files only” (screenshot #1).
Then, consider:
❯ mv pubkey.{txt,pub}
❯ cat pubkey.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC3un58bzSwrEXD5PMNuT9nYhyBfdiEeDrcQd3Facw9PZihlFwfec+iz00u4bbNmcrG0YhT056PSnqIR4DqGSK3N2iancS1anBfgNS7Se02jcOyoHsgrDFH6MxEgkZLoFY8XodE5NPDGt6rPoiy6MeN0jKNvuMMQ9UFge67ky0pWZjyDjdyXERZWEIjcp+OQXMaFAU3zJCbnaLgVn7CizZcwriu2ElMg0tVvxdkW59QW9dSgmCdF4zwSvLN6XVpaCw+fiXV+09Wq5PT65qT/rWC/0yO4BWuZFteX8gXyDQBJqEzNKjkvACNFI4ublSUQO7zYnyFQjlww04+afTFkWZYIV2UtOZYzJaTg90DT3fQBkJMxsHHc4G8eF+SveIy1tiOq7jf8btvdKLCyvIrNMlhB99YPAzBFUd/X/w7uOEtm7L4zoWa+6YRjtKiPtuaeGGQVr3CEU/L9rtPY9PfkPOxGUahnM5M2MsST5NPZ9+tWvhjEFX4nSYo5EShFBE9m01sa675mzrOwsBXwi7AlBZtT4hEYN1jvVUVXrwEC8W7RKy3C0mgU/mlnxXHp23af9YEkjiYA5ZBmK4+q85o0pBf616cLAhzebDwoT5v9VkYY+q1t3nLWpaG9HAH0BmPyEW0jlB1jxqwUvlmWQ14vtZUOAzrFnAoUKDVLTeuK+w5vw== cardno:23_610_166
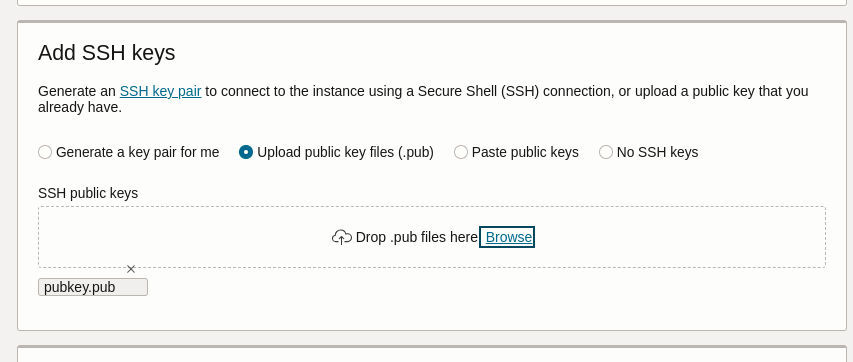
As can been seen from screenshot #2, the public key was successfully uploaded. For me this looks like as if validation was based on the filename extension o_O
A correct validation would ignore the file’s name and base validation on RFC 4716: The Secure Shell (SSH) Public Key File Format.
Jarkko Sakkinen
jarkkoStumped into a bug straight out right in the get-go ;-) It goes like this…
First, consider:
❯ cat pubkey.txt
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC3un58bzSwrEXD5PMNuT9nYhyBfdiEeDrcQd3Facw9PZihlFwfec+iz00u4bbNmcrG0YhT056PSnqIR4DqGSK3N2iancS1anBfgNS7Se02jcOyoHsgrDFH6MxEgkZLoFY8XodE5NPDGt6rPoiy6MeN0jKNvuMMQ9UFge67ky0pWZjyDjdyXERZWEIjcp+OQXMaFAU3zJCbnaLgVn7CizZcwriu2ElMg0tVvxdkW59QW9dSgmCdF4zwSvLN6XVpaCw+fiXV+09Wq5PT65qT/rWC/0yO4BWuZFteX8gXyDQBJqEzNKjkvACNFI4ublSUQO7zYnyFQjlww04+afTFkWZYIV2UtOZYzJaTg90DT3fQBkJMxsHHc4G8eF+SveIy1tiOq7jf8btvdKLCyvIrNMlhB99YPAzBFUd/X/w7uOEtm7L4zoWa+6YRjtKiPtuaeGGQVr3CEU/L9rtPY9PfkPOxGUahnM5M2MsST5NPZ9+tWvhjEFX4nSYo5EShFBE9m01sa675mzrOwsBXwi7AlBZtT4hEYN1jvVUVXrwEC8W7RKy3C0mgU/mlnxXHp23af9YEkjiYA5ZBmK4+q85o0pBf616cLAhzebDwoT5v9VkYY+q1t3nLWpaG9HAH0BmPyEW0jlB1jxqwUvlmWQ14vtZUOAzrFnAoUKDVLTeuK+w5vw== cardno:23_610_166
Uploading this results “Invalid file type. SSH public key (.pub) files only” (screenshot #1).
Then, consider:
❯ mv pubkey.{txt,pub}
❯ cat pubkey.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC3un58bzSwrEXD5PMNuT9nYhyBfdiEeDrcQd3Facw9PZihlFwfec+iz00u4bbNmcrG0YhT056PSnqIR4DqGSK3N2iancS1anBfgNS7Se02jcOyoHsgrDFH6MxEgkZLoFY8XodE5NPDGt6rPoiy6MeN0jKNvuMMQ9UFge67ky0pWZjyDjdyXERZWEIjcp+OQXMaFAU3zJCbnaLgVn7CizZcwriu2ElMg0tVvxdkW59QW9dSgmCdF4zwSvLN6XVpaCw+fiXV+09Wq5PT65qT/rWC/0yO4BWuZFteX8gXyDQBJqEzNKjkvACNFI4ublSUQO7zYnyFQjlww04+afTFkWZYIV2UtOZYzJaTg90DT3fQBkJMxsHHc4G8eF+SveIy1tiOq7jf8btvdKLCyvIrNMlhB99YPAzBFUd/X/w7uOEtm7L4zoWa+6YRjtKiPtuaeGGQVr3CEU/L9rtPY9PfkPOxGUahnM5M2MsST5NPZ9+tWvhjEFX4nSYo5EShFBE9m01sa675mzrOwsBXwi7AlBZtT4hEYN1jvVUVXrwEC8W7RKy3C0mgU/mlnxXHp23af9YEkjiYA5ZBmK4+q85o0pBf616cLAhzebDwoT5v9VkYY+q1t3nLWpaG9HAH0BmPyEW0jlB1jxqwUvlmWQ14vtZUOAzrFnAoUKDVLTeuK+w5vw== cardno:23_610_166
As can been seen from screenshot #2, the public key was successfully uploaded. For me this looks like as if validation was based on the filename extension o_O
A correct validation would ignore the file’s name and base validation on RFC 4716: The Secure Shell (SSH) Public Key File Format.
Jarkko Sakkinen
jarkkoSince I switched from #Dropbox to #Storj, I’ve been almost solely using rclone.
Now I’ve started to feel that t it would be nice to have also an ownCloud instance and point out its storage to my #S3 bucket at Storj.
After looking through cloud options, I think got with ARM Ampere A1 VM: that #Oracle offers:
“Up to 4 instances of ARM Ampere A1 Compute with 3,000 OCPU hours and 18,000 GB hours per month”
Should scale a to my personal ownCloud with storage backend at Storj. The amount of OCPU hours nailed this really…
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJust paid 40 EUR annual bill for my Kapsi SSH account. It is the center piece of my digital life :-)
Kapsi has a IMAP inbox for my personal email and kernel.org mail (the same inbox is shared via RFC 5233 sub-addressing ), IRC screen (tmux), sometimes bots (tmux), exposing files via https URL’s (sometimes more feasible than e.g. dropbox shared links). It also provides for each user 50 GiB of backed up quota (with self-restore) and 500 GiB of space “in your own responsibility”.
Servers are hardened with quite reasonable standards and some of the people at Kapsi maintaining the backend actually know what they are doing when it comes to #infosec ;-)
It just continues to amaze me how dirt cheap this service is… and how awesome it is :-)
-
Jarkko Sakkinen
jarkkoResetting the commit history of pass
pushd ~/.password-store
git checkout --orphan main2
git add .
git commit -a -s -m epoch
git branch -D main
git branch -M main
git push origin main -f
git log -1
popd
Execution transcript:
~ main
❯ pushd ~/.password-store
git checkout --orphan main2
git add .
git commit -a -s -m epoch
git branch -D main
git branch -M main
git push origin main -f
git log -1
popd
~/.password-store ~
Switched to a new branch 'main2'
[main2 (root-commit) a25d65b] epoch
# <snip>
Deleted branch main (was 0600cc7).
Enumerating objects: 76, done.
Counting objects: 100% (76/76), done.
Delta compression using up to 8 threads
Compressing objects: 100% (68/68), done.
Writing objects: 100% (76/76), 33.51 KiB | 11.17 MiB/s, done.
Total 76 (delta 0), reused 44 (delta 0), pack-reused 0
To kapsi.fi:git/password-store
+ 0600cc7...a25d65b main -> main (forced update)
commit a25d65b3ebcf87f45540bd54f209193fc5f1fef2 (HEAD -> main, origin/main, origin/HEAD)
Author: Jarkko Sakkinen <jarkko.sakkinen@iki.fi>
Date: Mon Jun 17 02:18:06 2024 +0300
epoch
Signed-off-by: Jarkko Sakkinen <jarkko.sakkinen@iki.fi>
Phil M0OFX
philpem@digipres.clubMeanwhile, while I'm on a #Ghidra bender this evening - I just found this neat tutorial on using Zynamics #BinDiff with Ghidra, via the #BinExport plugin:
https://www.0x90.se/reverse%20engineering/install-binexport-and-bindiff/
I'm planning to give this a go - while I had access to IDA+Bindiff, I used it a fair bit.
Edit - in case you missed it, BinDiff and BinExport are also now open-source:
BinDiff: https://github.com/google/bindiff
BinExport: https://github.com/google/binexport
Jarkko Sakkinen
jarkkoHere’s the next steps for tpm2-cli.
Transient objects:
tpm2-cli flush- TPM2_FlushContext
tpm2-cli create- TPM2_Create
tpm2-cli load- ASN.1 decode.
TPM2_Load
tpm2-cli saveTPM2_Import- ASN.1 encode.
Persistent objects:
tpm2-cli punch.- Inspired by
fallocate(2) FALLOC_FL_PUNCH_HOLE.
- Inspired by
tpm2-cli persistTPM2_EvictControl
So the basic gist here is that the command-line I/O goes always in ASN.1 format. Obviously other formats could be supported too but that is what I care myself ATM.
After that I’ll see how much the smoke test transcripts in my kernel patch set cover letter simplify:
https://lore.kernel.org/linux-integrity/20240528210823.28798-1-jarkko@kernel.org/
Jarkko Sakkinen
jarkkoFor kernel maintainers RSA + NIST does provide quite a good coverage for certificate keys, so as an opt-in feature, not required but can ease the workflow, it is level up even with just those two curves (and that was anyway my original take) :-)
Jarkko Sakkinen
jarkkoOK so this is how these are:
- K1/R1: {256,384,521} bits finite field: ECDSA + SHA-{256,384,512}
- 25519: 255 bits finite field: EdDSA + SHA-512
- 448: 224 bits finite field: EdDSA + SHAKE256
They are all in the TCG Algorithm Registry so it is up to firmware updates to support it. TCG specifications have all assets to implement 448 signing (I just checked).