Posts
5062Following
330Followers
506OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkoI've seen mostly either luks1-lvm-ext4 topology with passphrase and luks2-btrfs topolgy.
And I'm going to give a shot on luks2-lvm-ext4, which is something I'm also interested to see if it can work properly.
So it is also "for the benefit of the mandkind" ;-) Not listed here: https://wiki.archlinux.org/title/dm-crypt/Encrypting_an_entire_system#LVM_on_LUKS
Have to give up on archinstall achieve this and make a script.
Jarkko Sakkinen
jarkkoNot true. It is just kept relatively small (like 2GB and similar figures) because its main job is these days to provide depth in failure tolerance for near OOM situations.
Back in the day it was for "spare slow memory space", which is of course not applicable anymore.
Except: if hibernation is used it obviously need to be larger than the system memory.
Jarkko Sakkinen
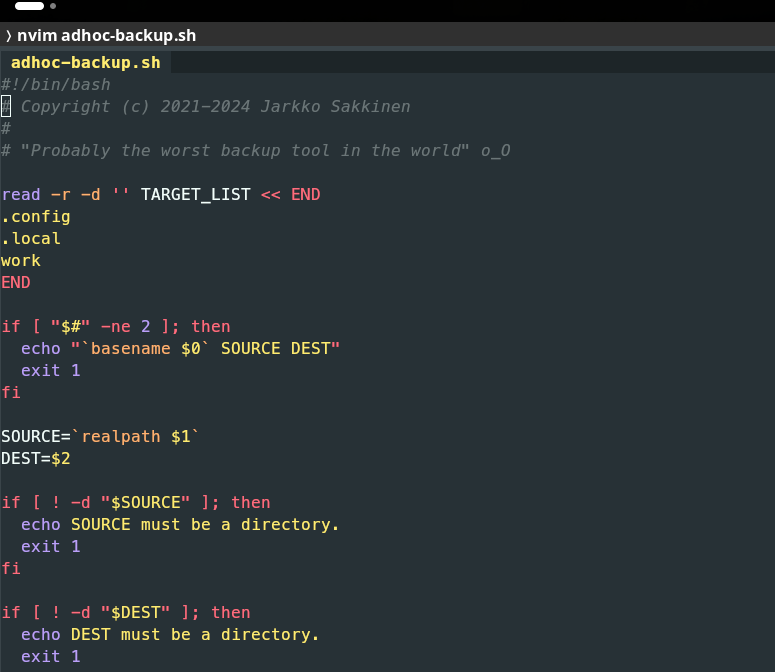
jarkkoneed this for my #btrfs to #ext4 migration 🤷 https://codeberg.org/jarkko/adhoc-backup #git
#codesberg - “Probably the best git hosting in the world”
Jarkko Sakkinen
jarkkolike if your machine breaks, maybe there's only a windows laptop available, no problem with ext4 :-) i'd figure there's some shaky btrfs windows drivers out there too but u know... would not put my life on them :-)
that's why I like also fat and its variants... (exfat is ace).
Jarkko Sakkinen
jarkkoI know ext4 well enough that I could probably write myself some code to read a partition if I really had to. Or even fix some mainline bugs because I know how it does what it does in great granularity.
Btrfs is like that I need to call helpdesk or something if it ever flipped on me :-) And not that much interest that I would want to climb to a mountain for the sake of btrfs tbh... My ASUSTOR NAS does use btrfs tho.
Jarkko Sakkinen
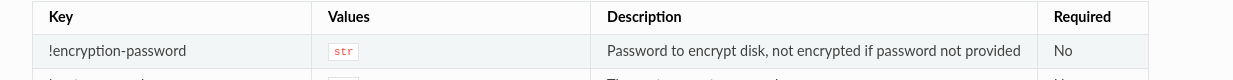
jarkkoworkaround:
❯ cat user_credentials.json
{
"!root-password": null,
"!users": [
{
"!password": "SecretSanta2022",
"sudo": true,
"username": "jarkko"
}
],
"encryption_password": "SecretSanta2022"
}
Now I need to only remember that the password is SecretSanta2022 whenever I use this :-)
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkowhy the heck they can't have exact same semantics is beyond me. especially since more privileged (root) has this flexibility but less privileged (user) does not.
and it will be a nightmare to recall their slight differences few months from now...
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoFound a null pointer deference in archinstall.
this flips:
root@archiso ~ # cat user_credentials.json
{
"!root-password": null,
"!users": [
{
"!password": null,
"sudo": true,
"username": "jarkko"
}
],
"encryption_password": null
}
this does not flip:
root@archiso ~ # cat user_credentials.json
{
"!root-password": null,
"!users": [
{
"!password": null,
"sudo": true,
"username": "jarkko"
}
],
"encryption_password": ""
}
it crashes when moving the cursor in the main menu on top of the “disk encryption”.
Jarkko Sakkinen
jarkkoGiven that I want to switch back to ext4, i need to also reinstall.
I went through manually installed RPM packages, narrowed the list down to 41 most critical, and here’s what I ended up with:
aerc bat bison ccache clang cmake expect fatcat flex fzf gcc github-cli gh git gnupg hatch hyperfine irssi mc mediainfo meson mmv msmtp ncdu neovim openssl pam-u2f pass patch pwgen qemu ranger rclone ripgrep sha3sum socat strace tealdeer w3m zig zola zoxide zsh
These are mapped to Arch Linux package names. I’ll install that distribution because I can just pass that list to archinstall be back in online maybe about ~2h :-)
It goes like this:
- Install Arch Linux to VM and use archinstall for this.
- Export json.
- [Backup json too.]
- On bare metal boot from stick and pass that json to the installer and shit will just happen!
Now that I anyway have to reinstall I found out about how this works and it plain just make sense to me…
EDIT: actually 42 packages, gnupg was missing, well anyway…
Jarkko Sakkinen
jarkkoCargo is almost like Docker in this context. I can just compile #BuildRoot image with #cargo baked in, and once the image boots up it can install test apps from cargo.
Super nice approach for doing something more complex than kselftest but going to podman would be over the top...
#rustlang
Jarkko Sakkinen
jarkkoUsing #Storj and local #Nextcloud (one per machine) is actually quite easy:
!/usr/bin/env bash
# Taken from https://fedoramagazine.org/nextcloud-20-on-fedora-linux-with-podman/.
podman network create nextcloud-net
podman volume create nextcloud-app
podman volume create nextcloud-data
podman volume create nextcloud-db
# MariaDB
podman run --detach \
--env MYSQL_DATABASE=nextcloud \
--env MYSQL_USER=nextcloud \
--env MYSQL_PASSWORD=DB_USER_PASSWORD \
--env MYSQL_ROOT_PASSWORD=DB_ROOT_PASSWORD \
--volume nextcloud-db:/var/lib/mysql \
--network nextcloud-net \
--restart on-failure \
--name nextcloud-db \
docker.io/library/mariadb:10
# Nextcloud
podman run --detach \
--env MYSQL_HOST=nextcloud-db.dns.podman \
--env MYSQL_DATABASE=nextcloud \
--env MYSQL_USER=nextcloud \
--env MYSQL_PASSWORD=DB_USER_PASSWORD \
--env NEXTCLOUD_ADMIN_USER=NC_ADMIN \
--env NEXTCLOUD_ADMIN_PASSWORD=NC_PASSWORD \
--volume nextcloud-app:/var/www/html \
--volume nextcloud-data:/var/www/html/data \
--network nextcloud-net \
--restart on-failure \
--name nextcloud \
--publish 8080:80 \
docker.io/library/nextcloud:20
So no need to use Oracle cloud for this. And instances do not really need to necessarily to sync up given the user count.