Posts
4937Following
327Followers
492OpenPGP: 3AB05486C7752FE1
Thorsten Leemhuis (acct. 1/4)
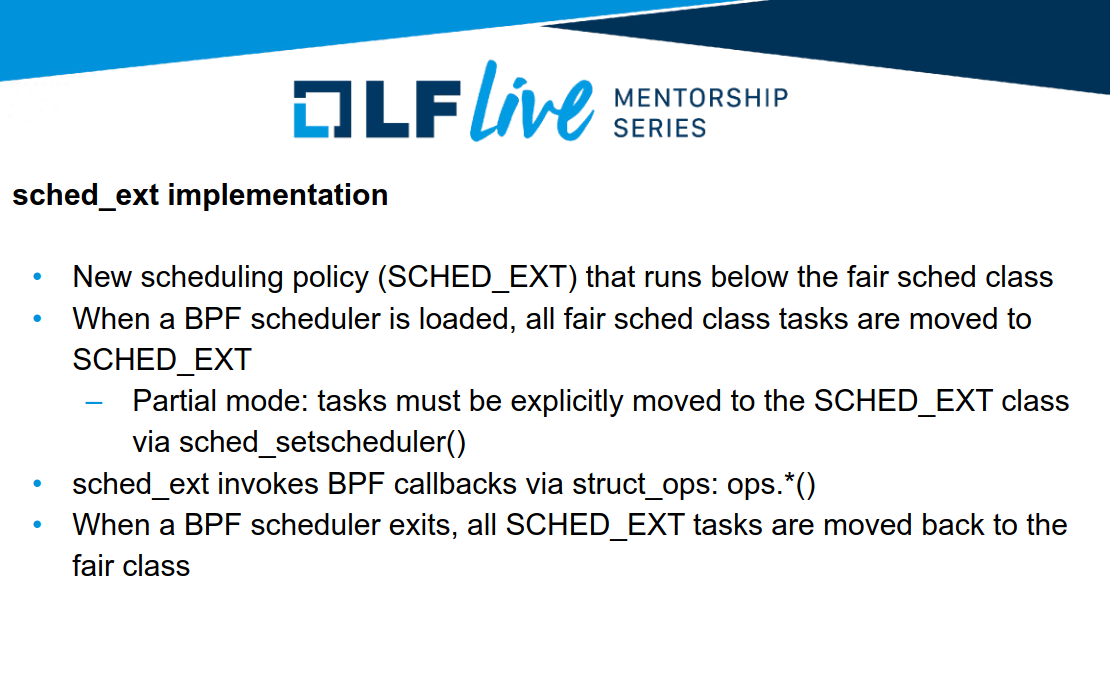
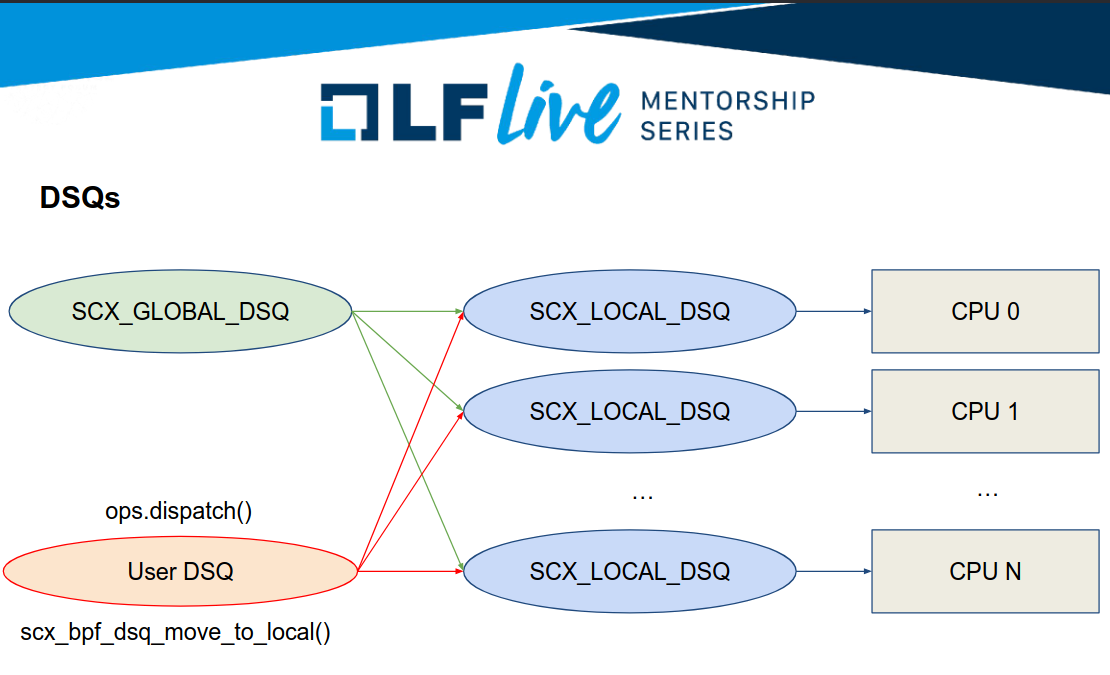
kernellogger@fosstodon.orgDesigning Custom #Linux Schedulers with sched_ext – slides and the recording of yesterdays #LinuxFoundation Mentorship session from @arighi are now online:
https://www.linuxfoundation.org/webinars/designing-custom-linux-schedulers-with-sched_ext
Direct link to the slides: https://events.linuxfoundation.org/wp-content/uploads/2025/01/Andrea-Righi-Mentorship-1_22_25-scx.pdf
Direct link to the recording: https://www.youtube.com/watch?v=jsLjg9tGuVI
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoWhat you *actually* should start with is how the network discovery works. I.e. plain and simple how network nodes find each other. It's not flashy but it is like the first question for any seasoned engineer.
In order to do the secret handshakes you need to first bump into someone else to do your dance.
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoA video device can be either something like camera or something that takes input from client and displays that, e.g. similar device to ChromeCast would be a good example in this context.
I'm aligning to a solution where the initial "ADD" ioctl has:
1. flags (for setting the RW properties)
2. video_nr
3. video_fd (for server to read OR write)
And the direction is determined by flags. I did not fully understand why OOT driver aimed to do both capture and output device simultaneously, which does bother me a bit since it would be best to know the original reasoning, even if the conclusions were wrong.
Moving slowly in this area still and experimenting with options.
#linux #kernel #media #video4linux
Jarkko Sakkinen
jarkko- The first API breaking change: https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/linux-tpmdd.git/commit/?h=v4l2-loopback&id=64dd521682c305567ffa99929a09e2ba285be52e
- The reflective test change: https://codeberg.org/jarkko/v4l2-loopback-test/commit/436818003b9865a9a4af2d872bd09acae84c178e
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoAt least something done in the kernel side for the v4l2-loopback driver this week:
- The first baby step towards anonymous inode based loopback device: https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/linux-tpmdd.git/commit/?h=v4l2-loopback&id=90235ae07630962e6dc7c6b2b67f9e94584a6b74
- And a reflective step in my test program: https://codeberg.org/jarkko/v4l2-loopback-test/commit/8950e975817e9d9b8012880dd9f2443d2fe13c77
The next small push is to split v4l2_loopback_fops into two: one for /dev/videoX and other for the anonymous inode returned back from the ioctl.
Jarkko Sakkinen
jarkkoGot tired of updating clangd data manually so did a quick script to automate it :
#!/usr/bin/env bash
# Copyright (c) Jarkko Sakkinen 2025
set -e
run_build() {
make ARCH=x86_64 O=.clangd -j$(nproc)
scripts/clang-tools/gen_compile_commands.py -d .clangd
}
run_menuconfig() {
if [[ ! -d .clangd ]]; then
exit 1
fi
make ARCH=x86_64 O=.clangd menuconfig
run_build
}
while getopts ":m" opt; do
case $opt in
m)
run_menuconfig
exit 0
;;
*)
echo "Usage: $0 [-m]"
exit 1
;;
esac
done
if [[ ! -d .clangd ]]; then
make ARCH=x86_64 O=.clangd tinyconfig
fi
run_build
Jarkko Sakkinen
jarkkohttps://github.com/rust-lang/rust/issues/135704
It's weird...
#rust #rustlang
Jarkko Sakkinen
jarkkoNeil Brown
neil@mastodon.neilzone.co.ukIt feels suboptimal that each fedi service requires a different account.
e.g. I have a Flohmarkt instance, which is different from my Mastodon instance. If I also ran a pixelfed instance, that would be a third account.
Rather than one "me", with different linked services.
Perhaps there is a need for a fedi directory service / "main" account, which people can use for discovering of sub-accounts?
(I can see that, for some users, separation of accounts will be valuable, so I wouldn't want to remove that ability.)
Jarkko Sakkinen
jarkko1. C: https://github.com/emoon/minifb
2. Rust: https://github.com/emoon/rust_minifb
This is pure gold!
A simple no bullshit framebuffer that dumps to X11/Wayland/macOS/iOS/Android/Web(WASM).