Posts
4888Following
324Followers
489OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkko
I dared to apply this to my -next:
https://lore.kernel.org/keyrings/Z_e9CVsmiXD3QYkg@kernel.org/
It's a good timing, given that we are at -rc1. key_put() is exactly type of code where:
1. You need to be extremely conservative.
2. Still there's a chance for breakage.
3. struct key is widely accessed kernel object in various context's. Thus, it is practically impossible to consider every possible use case.
I'll put this to my v6.16 PR if it turns out to not cause too much devastation :-)
#linux #kernel #keyring
https://lore.kernel.org/keyrings/Z_e9CVsmiXD3QYkg@kernel.org/
It's a good timing, given that we are at -rc1. key_put() is exactly type of code where:
1. You need to be extremely conservative.
2. Still there's a chance for breakage.
3. struct key is widely accessed kernel object in various context's. Thus, it is practically impossible to consider every possible use case.
I'll put this to my v6.16 PR if it turns out to not cause too much devastation :-)
#linux #kernel #keyring
Jarkko Sakkinen
jarkko
Flying to Berlin in near future to meet up friends from Tallinn :-) It's cheaper than train + boat.
Jarkko Sakkinen
jarkko
"marvel's mignight suns" is a cool game but why they have to talk so much, and why i need to hang out.
i don't hang out IRL either 🤷
i don't hang out IRL either 🤷
Jarkko Sakkinen
jarkko
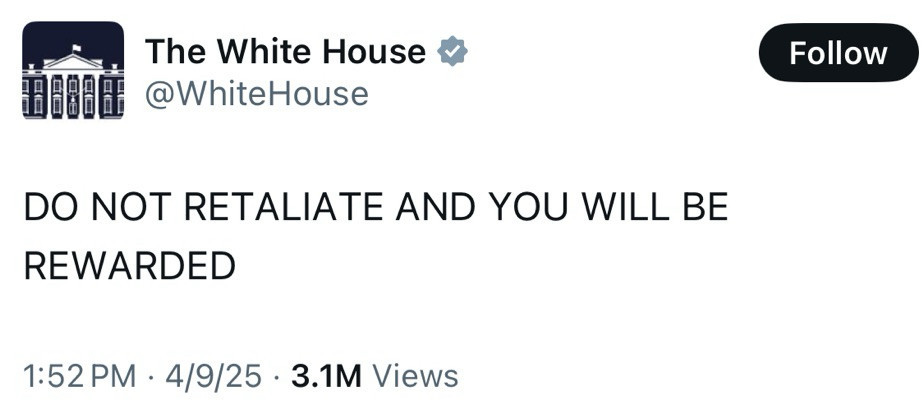
thank you mr showerhead for giving this freedom my US comrades (pun intended).
https://www.whitehouse.gov/presidential-actions/2025/04/maintaining-acceptable-water-pressure-in-showerheads/
https://www.whitehouse.gov/presidential-actions/2025/04/maintaining-acceptable-water-pressure-in-showerheads/
Jarkko Sakkinen
jarkko
Edited 6 months ago
container hack for build: unshare + chroot. unshare guarantees unmounts, given a ephemeral file system namespace :-)
#!/bin/sh
set -eu
rootfs_dir=$1
adm_user=$2
if [ "$#" -eq 3 ]; then
proxy_address=""
cmdline=$3
else
proxy_address=$3
cmdline=$4
fi
sudo unshare --mount --pid --fork sh -c "
mount --bind /sys '$rootfs_dir/sys'
mount --bind /dev '$rootfs_dir/dev'
mount -t proc proc '$rootfs_dir/proc'
mount -t devpts devpts '$rootfs_dir/dev/pts'
chroot '$rootfs_dir' su - '$adm_user' -c 'export PUAVO_CACHE_PROXY=\"$proxy_address\"; $cmdline'
"
Jarkko Sakkinen
jarkko
@oleksandr not likely but i'll have to hear if this needs additional fixes
Jarkko Sakkinen
jarkko
@Conan_Kudo BTW, so we do have machine keyring and MOK keys. What is the problem?
Jarkko Sakkinen
jarkko
@Conan_Kudo There's this irony in shared data (in general) that even if your blob lives for the whole power cycle, it must be prepared for sudden death that could happen in the next time quantum :-)
Jarkko Sakkinen
jarkko
@Conan_Kudo This work is for key_put() :-) How to make it less sensitive overall.
Jarkko Sakkinen
jarkko
In the case of procfs I'll check if this strategy would allow to relax locking requirements for /proc/keys.
Jarkko Sakkinen
jarkko
Anyone interested on keyring:
https://web.git.kernel.org/pub/scm/linux/kernel/git/jarkko/linux-tpmdd.git/commit/?h=keys-graveyard
If this would work out then possibly also radiate to /proc/keys.
I.e. it could also similarly "knock for reference" but that is not within scope of this patch.
#linux #kernel #keyring
https://web.git.kernel.org/pub/scm/linux/kernel/git/jarkko/linux-tpmdd.git/commit/?h=keys-graveyard
If this would work out then possibly also radiate to /proc/keys.
I.e. it could also similarly "knock for reference" but that is not within scope of this patch.
#linux #kernel #keyring
Jarkko Sakkinen
 repeated
repeated
Jarkko Sakkinen
 repeated
repeated
Dr. Motte
drmotte@mastodon.social@anneroth Danke
30 tips zu mach dich digital unabhängig von @kuketzblog
Link https://www.kuketz-blog.de/unplugtrump-mach-dich-digital-unabhaengig-von-trump-und-big-tech/