Posts
4941Following
327Followers
492OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkohttps://doc.rust-lang.org/beta/std/io/trait.IsTerminal.html
Apparently std has had this for over two years already.
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkko1. better coverage
2. time saved from writing tests
3. less dependecies
Jarkko Sakkinen
jarkkoi'll also add a Makefile to the root with "make test" target. It will build the test binary with rustc and run the tests. Finally this will be added to the CI.
Jarkko Sakkinen
jarkko@mupuf I wrote the code so that i don’t end up dust-for-linux :D
I also learned that “macros_rules!” is the thing that you would want to learn first in Rust so that it would make any sense if you knew beforehand that it is the thing that you most want to learn :-) Without it super unproductive language and IMHO does not really pay the cost despite what ever “memory safety”. With “macro_rules!” you can consolidate those few dozen trait implementations into one single place :-) Then it is suddenly more productive language than C.
I drive the spec interpration and building with ~600 lines of trial and error fine-tune syntax tree macros :-) https://github.com/puavo-org/tpm2_library/blob/main/protocol/src/macro.rs
And then I can implement the spec like I was writing the spec:
tpm_struct!(
#[derive(Debug, Default, PartialEq, Eq, Clone)]
TpmStartAuthSessionCommand,
TpmCc::StartAuthSession,
true,
true,
2,
{
pub nonce_caller: Tpm2b,
pub encrypted_salt: Tpm2b,
pub session_type: TpmSe,
pub symmetric: TpmtSymDefObject,
pub auth_hash: TpmAlgId,
}
);
And all the bidirectional marshalling and unmarshallinf magic will appear :-) Things like “async” are more like fixed structure threading framework type of stuff but does not convince at all what makes sense in the core language (neither does borrow checker at least not as “driving feature”), I mean we already have Java :-) ).
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkohttps://github.com/puavo-org/tpm2_library/commit/7b0fc824bd341fb21c90a06b945f01feb1c20f5e
There's MS TPM 2.0 emulator and swtpm, and that's like all of command parsing and response synthesis I'm aware of. I.e. by practical means there was no useful existing work to take example of :-) I'm pretty happy and a bit proud too that I've reach unipolarity by writing Rust macros reflecting TCG specifications.
I don't have now known bugs in the protocol crate. I'm sure there's a bunch but still feels nice after 1.5 weeks of sleepless nights and 7K SLOC of code (protocol + cli).
#linux #kernel #rust #tpm
Jarkko Sakkinen
jarkkoI think, considering rust-linux, one interesting feature could be swtpms, which becomes realistic goal if you make right conclusions of what you're observing. I don't actually know could you create endosement infrastructure where swtpm instances have their endorsement keys certified by the TPM chip (which is endorsed by the manufacturer).
In the previous TPM stack implementations i think that core mistake that has been repeatedly made is thinking that you have a client and chip or emulator, which is not from technical perspective correct assesment.
QEMU is an emulator. TPM2 is a protocol. That is stating the obvious but for some reason that is the exact blind spot.
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoThis makes me happy:
tpm_struct!(
#[derive(Debug, PartialEq, Eq, Clone)]
TpmPcrEventCommand,
TpmCc::PcrEvent,
TpmSt::Sessions,
1,
{
pub event_data: Tpm2b,
}
);
tpm_response!(
#[derive(Debug, Default, PartialEq, Eq, Clone)]
TpmPcrEventResponse,
TpmCc::PcrEvent,
TpmSt::Sessions,
{
pub digests: TpmlDigestValues,
}
);
Also the types inside use the same system (in fact tpm_struct is shared macro with data types and commands). This will generate full parsing and building for both commands and responses - all without heap involved.
James Morris
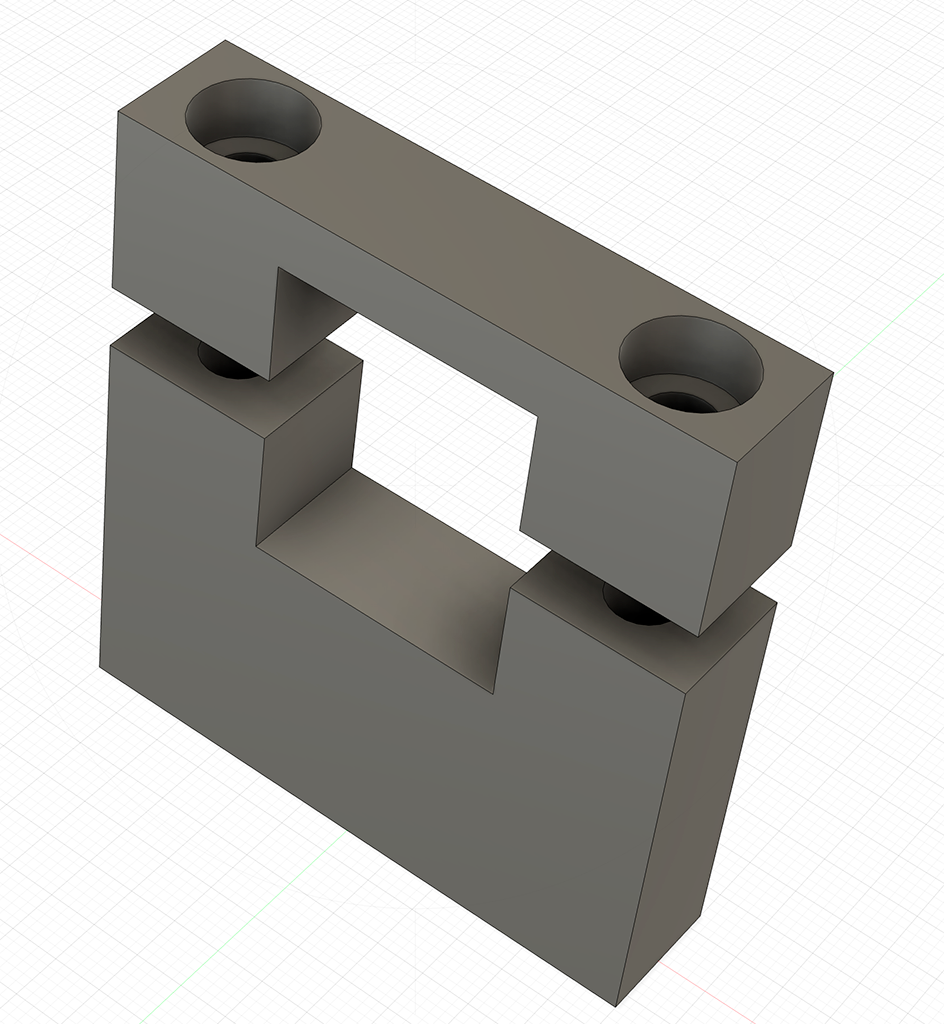
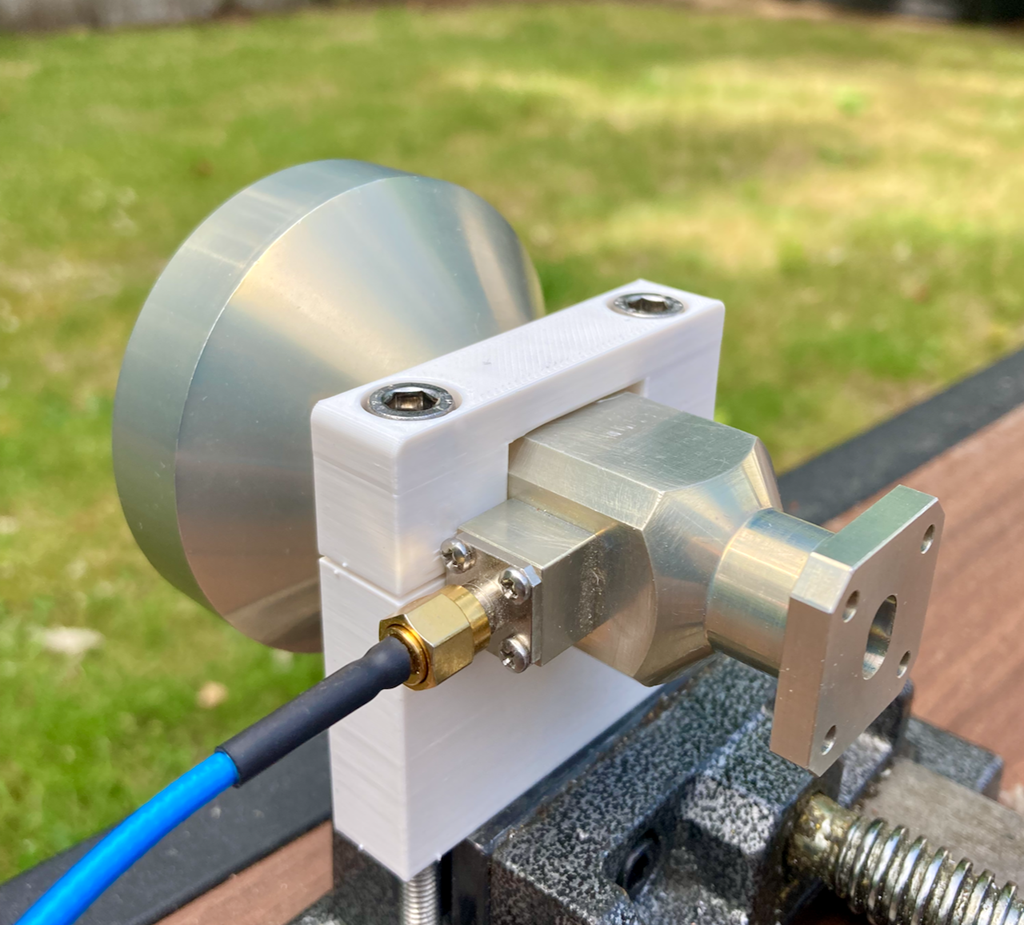
jmorrishttps://github.com/xjamesmorris/dual-band-10-24-ghz-feed-mount
#amateurradio #hamradio #3dprinting #rf #microwave