Posts
4871Following
323Followers
491OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkko
aside from compilation issues with old'ish toolchain the packaging for buildroot is quite nice when it comes to Rust:
https://codeberg.org/jarkko/linux-tpmdd-test/commit/642955a3fa7515c1656bd3ce594dcfb5164b2e43
https://codeberg.org/jarkko/linux-tpmdd-test/commit/642955a3fa7515c1656bd3ce594dcfb5164b2e43
Jarkko Sakkinen
jarkko
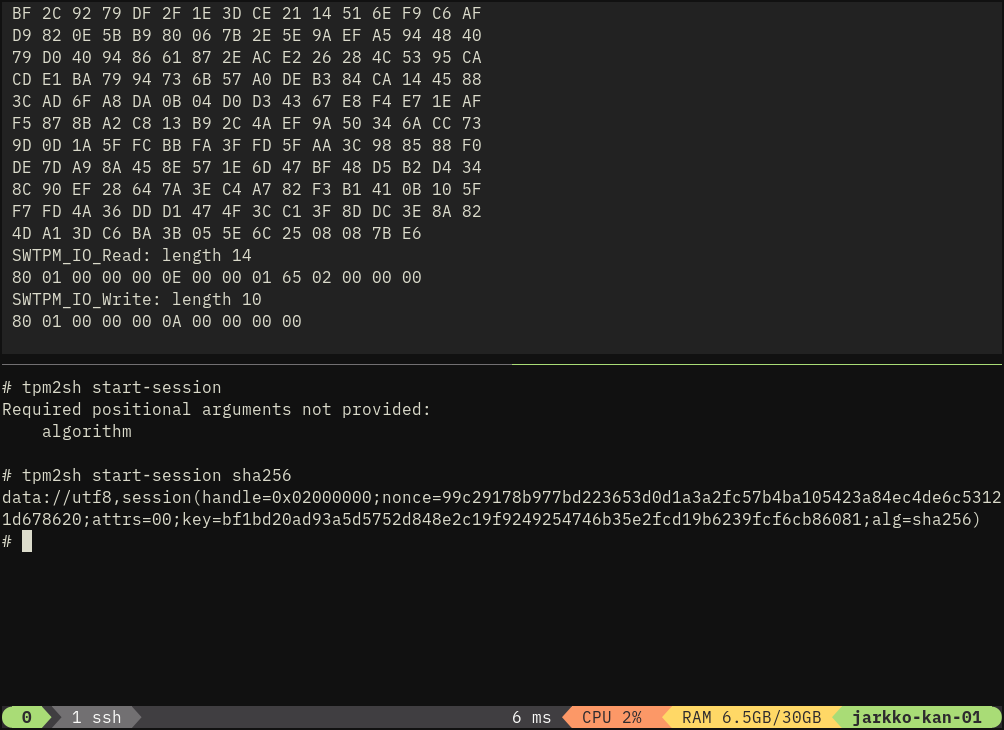
and what this gives is factors better debugging environment to fix the remaining external key import issue :-) swtpm dump in the top split
Jarkko Sakkinen
jarkko
awesome, new milestone reached: tpm2sh and tpm2-protocol compile with the Rust toolchain of Buildroot 2025.02.6.
Couple of recursive dependencies needed to be downgraded, and some code tweaks but nothing heavy (phew). I also found that even you set your edition to 2021, the chances are that there is some nested dependency that is allowed to be in edition 2024.
#buildroot
Couple of recursive dependencies needed to be downgraded, and some code tweaks but nothing heavy (phew). I also found that even you set your edition to 2021, the chances are that there is some nested dependency that is allowed to be in edition 2024.
#buildroot
Jarkko Sakkinen
jarkko
A good exercise for Rust code IMHO in order to get it to the level that actually is fluent in production is to create BuildRoot package for it ;-)
All sorts of minor tweaks have had to done for tpm2sh and tpm2-protocol in order to get them to my kernel testing images.
Or at least a good exercise if planning to target and scale Rust crate to embedded systems (in production).
#buildroot #rust
All sorts of minor tweaks have had to done for tpm2sh and tpm2-protocol in order to get them to my kernel testing images.
Or at least a good exercise if planning to target and scale Rust crate to embedded systems (in production).
#buildroot #rust
Jarkko Sakkinen
jarkko
Edited 1 month ago
I've started to support more proactively TrenchBoot efforts because D-RTM despite being a bit rough compared to enclaves, is at least fully open. It also draws me a positive picture about Oracle as a company as it proves to me that they push technologies to upstream that don't only support Oracle's proprietary technologies but also is benefical work for the wider developer ecosystem (unlike e.g., Intel and AMD). It's good cause IMHO plain and simple.
Jarkko Sakkinen
jarkko
my favorite patches are those that rip of over 100 lines of code :-) https://lore.kernel.org/linux-integrity/20250919112448.2543343-1-jarkko@kernel.org/T/#u
Jarkko Sakkinen
jarkko
Edited 1 month ago
rasn crate is the best thing for custom ASN.1 parsers imho:
https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2sh.git/tree/src/key/tpm_key.rs?h=main
See: https://github.com/librasn/rasn
https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2sh.git/tree/src/key/tpm_key.rs?h=main
See: https://github.com/librasn/rasn
Jarkko Sakkinen
jarkko
expected too that there's end boss fight with different external key types, such as PKCS#8 and SEC1 and import ;-) this will slowly uncover...
Jarkko Sakkinen
jarkko
there's a bug with import on "rsa parent + ecc child" that i'm debugging other than that this start to look soon release ready.
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkko
"precious oneliners" ;-) had to go look this up from lore
make CROSS_COMPILE=aarch64-linux-gnu- ARCH=arm64 tinyconfig && ./scripts/config --file .config -e CONFIG_KEYS -e CONFIG_TCG_TPM -e CONFIG_64BIT -e CONFIG_TRUSTED_KEYS -e CONFIG_TTY -e CONFIG_PROCFS -e CONFIG_SYSFS -e CONFIG_TCG_VTPM_PROXY -e CONFIG_EFI -e CONFIG_ACPI -e CONFIG_ARM_FFA_TRANSPORT -e CONFIG_TCG_CRB && yes '' | make CROSS_COMPILE=aarch64-linux-gnu- ARCH=arm64 oldconfig && make CROSS_COMPILE=aarch64-linux-gnu- ARCH=arm64 -j$(nproc)
make CROSS_COMPILE=aarch64-linux-gnu- ARCH=arm64 tinyconfig && ./scripts/config --file .config -e CONFIG_KEYS -e CONFIG_TCG_TPM -e CONFIG_64BIT -e CONFIG_TRUSTED_KEYS -e CONFIG_TTY -e CONFIG_PROCFS -e CONFIG_SYSFS -e CONFIG_TCG_VTPM_PROXY -e CONFIG_EFI -e CONFIG_ACPI -e CONFIG_ARM_FFA_TRANSPORT -e CONFIG_TCG_CRB && yes '' | make CROSS_COMPILE=aarch64-linux-gnu- ARCH=arm64 oldconfig && make CROSS_COMPILE=aarch64-linux-gnu- ARCH=arm64 -j$(nproc)
Jarkko Sakkinen
jarkko
Edited 1 month ago
I'm planning a new kernel feature based on patch set that I never finished:
https://lore.kernel.org/linux-integrity/aMwh95tMxB7sMEzy@kernel.org/
The gist is to harden selected AIKs, and perform signing and quotes through kernel, and filtered out from /dev/tpm0.
They'd be wrapped into keyring asymmetric keys. You can lock-in remote attestation pretty well then with UKI images having signed command-line.
https://lore.kernel.org/linux-integrity/aMwh95tMxB7sMEzy@kernel.org/
The gist is to harden selected AIKs, and perform signing and quotes through kernel, and filtered out from /dev/tpm0.
They'd be wrapped into keyring asymmetric keys. You can lock-in remote attestation pretty well then with UKI images having signed command-line.
Jarkko Sakkinen
jarkko
Edited 1 month ago
getting hmac session together in tpm2sh:
❯ sudo target/debug/tpm2sh start-session -s hmac
data://utf8,session(handle=0x02000000;nonce=d19da78d903f3c3a2350b857da368ba02eb911bc2dfe307435e0eec9621083bd;attrs=00;key=1abf23e3cb74a40b1b093f5a7fbad330dc0f63c51e415f4523d98122e507a3b0;alg=sha256)
There used to be session:// but I migrated sessions as portion of the policy expression language grammar. Previously I migrated from pcr:// to language constructs.
Jarkko Sakkinen
jarkko
if there is one open source project, which i hope to succeed more than any other project, it must be Servo. it's super important that it will become game changer and real distruptor.
Jarkko Sakkinen
jarkko
Edited 1 month ago
i realized that you an do mustache templates with just plain jq:
jq -n -r \
--arg domains "$TENANT_DOMAIN" \
--arg hsm_type "$HSM_TYPE" \
--argjson enable_hello "$ENABLE_HELLO" \
'
"[global]\ndebug = true\ndomains = \($domains)\nhome_alias = CN\nhome_attr = CN\nid_attr_map = name\npam_allow_groups =\nuse_etc_skel = true\nlocal_groups = users\nhsm_type = \($hsm_type)\nenable_hello = \($enable_hello)"
' > "$BUILD_DIR/himmelblau.conf"
need to apply this idea to my kernel pull request scripts :-)
template here is:
[global]
debug = true
domains = {{domains}}
home_alias = CN
home_attr = CN
id_attr_map = name
pam_allow_groups =
use_etc_skel = true
local_groups = users
hsm_type = {{hsm_type}}
enable_hello = {{enable_hello}}
Jarkko Sakkinen
 repeated
repeated
Mikrobitti
mikrobitti@mastodon.socialCopilotin tekoälyavustaja todettiin hyödyttömäksi https://www.mikrobitti.fi/uutiset/a/5e914bbc-0b78-4eaf-8295-51811364515c?ref=aggregaatit%3A2fb1&utm_source=dlvr.it&utm_medium=mastodon
Jarkko Sakkinen
jarkko
because bash is my top 3 favorite programming languages and favorite scripting language :-)
Jarkko Sakkinen
jarkko
I've been thinking that post 0.11 tpm2sh cool feature would be remote attestation and demo would be remote attestation client and server in bash.
Jarkko Sakkinen
jarkko
I'll likely fix those glitches within a week or so and then it's ready for release :-)
The key insight here is that 50% of hardware is realized the software that creates interface for it, and for TPM2 the "software defined object" portion has been quite horrible :-) And it's pretty bad across the board form programming interfaces to tooling with absolutely no developer or sysadmin ergonomics consider anywhere.
On the other hand, by having right kind of software interface for TPM2, makes it like it was a completely new piece of hardware that did not exist before. I.e. not a brick.
The key insight here is that 50% of hardware is realized the software that creates interface for it, and for TPM2 the "software defined object" portion has been quite horrible :-) And it's pretty bad across the board form programming interfaces to tooling with absolutely no developer or sysadmin ergonomics consider anywhere.
On the other hand, by having right kind of software interface for TPM2, makes it like it was a completely new piece of hardware that did not exist before. I.e. not a brick.