Posts
4940Following
327Followers
492OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkko
Edited 1 month ago
I have pretty positive feelings after discussing on a call with Trenchboot patch set authors that we will be able to land it in foreseeable future.
I've kind of felt sympathy for that patch set especially with traumas from SGX patches :-) I offered a solution for nailing issues with early boot TPM access and it reflected, so I think we are now in a steady path for ultimate success.
Patch sets combining cryptography and device I/O are difficult because they end up always being exercise of inserting a cube into a circular hole. Trenchboot is particularly nasty because it intersects with both arch/x86 and TPM driver.
I've kind of felt sympathy for that patch set especially with traumas from SGX patches :-) I offered a solution for nailing issues with early boot TPM access and it reflected, so I think we are now in a steady path for ultimate success.
Patch sets combining cryptography and device I/O are difficult because they end up always being exercise of inserting a cube into a circular hole. Trenchboot is particularly nasty because it intersects with both arch/x86 and TPM driver.
Jarkko Sakkinen
jarkko
Edited 1 month ago
TPM2 driver was pretty static for multiple years but the volumes and use cases have been steadily increasing so right now many of the key parts are going through iterative rewrite:
https://lore.kernel.org/linux-integrity/aNQpvQBV43dhS6ad@kernel.org/
One thing I don't actually know about kernel is that can lib/* be used in the early boot code? I'd presume it can but just don't know the tidbit.
It would make whole a lot of sense to create decoupled command/response parsing/building implementation there and use that in the driver and early boot code.
#linux #kernel #tpm
https://lore.kernel.org/linux-integrity/aNQpvQBV43dhS6ad@kernel.org/
One thing I don't actually know about kernel is that can lib/* be used in the early boot code? I'd presume it can but just don't know the tidbit.
It would make whole a lot of sense to create decoupled command/response parsing/building implementation there and use that in the driver and early boot code.
#linux #kernel #tpm
Jarkko Sakkinen
jarkko
had my favorite breakfast at morning i.e. karelian pies with egg butter :-) only think that would add up to this would some cold-cured salmon
Jarkko Sakkinen
jarkko
I've started to make some groundwrok to make Trenchboot feasible to land to mainline kernel i.e. introducing builder/parser pattern in order to decouple physical transmission path from logical protocol shenanigans, translating the system to use mainly stack allocations and stuff like that.
Even tho C work, lot's ideas and inspiration come from my recent Rust work.
#linux #tpm #kernel
Even tho C work, lot's ideas and inspiration come from my recent Rust work.
#linux #tpm #kernel
Jarkko Sakkinen
 repeated
repeated
Kernel Recipes
KernelRecipes@fosstodon.orgCome along for the ride — check out the first sneak peeks of the conference!
#kr2025
Many thanks to Jean-Christophe for the ride (Uweti)
Jarkko Sakkinen
 repeated
repeated
Dan Gillmor
dangillmor@mastodon.socialTrump regime now requires press to sign a document agreeing not to obtain or possess "unauthorized" information.
Anyone who agrees to this is not qualified to call himself or herself a journalist.
But I'm betting most Big Journalism orgs will go ahead and sign.
Jarkko Sakkinen
jarkko
Sometimes lack of skills make one do complex tasks.
I was too lazy to learn how to
1. Package Rust programs to BuildRoot images.
2. Do the necessary fixes [1] and downgrades to get build working.
So as a temporary solution I wrote a TPM emulator :-) It's quite easy task with tpm2-protocol given that it is more like "a socket" than "a client" or "a server" abstraction.
However, now that I've done BuildRoot integration to my kernel testing builds [2], the next logical step is to split some offspring:
1. tpm2-protocol: core crate
2. tpm2sh: client
3. mocktpmd: standalone TPM emulator.
'd' is there so that if I ever want to further split mocktpmd to library and executable my naming conventions will scale ;-)
[1] https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git/commit/?id=4cc0198ee778881efffa658ea2fc65aa5e2c36cf
[2]
https://codeberg.org/jarkko/linux-tpmdd-test/commit/21ade103f9836c7174a8b1c14592928e1c626839
#linux #kernel #tpm #rustlang
I was too lazy to learn how to
1. Package Rust programs to BuildRoot images.
2. Do the necessary fixes [1] and downgrades to get build working.
So as a temporary solution I wrote a TPM emulator :-) It's quite easy task with tpm2-protocol given that it is more like "a socket" than "a client" or "a server" abstraction.
However, now that I've done BuildRoot integration to my kernel testing builds [2], the next logical step is to split some offspring:
1. tpm2-protocol: core crate
2. tpm2sh: client
3. mocktpmd: standalone TPM emulator.
'd' is there so that if I ever want to further split mocktpmd to library and executable my naming conventions will scale ;-)
[1] https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git/commit/?id=4cc0198ee778881efffa658ea2fc65aa5e2c36cf
[2]
https://codeberg.org/jarkko/linux-tpmdd-test/commit/21ade103f9836c7174a8b1c14592928e1c626839
#linux #kernel #tpm #rustlang
Jarkko Sakkinen
jarkko
my shitty buildroot kernel testing environment keeps improving as the years pass like a good wine ;-)
#buildroot
#buildroot
Jarkko Sakkinen
jarkko
aside from compilation issues with old'ish toolchain the packaging for buildroot is quite nice when it comes to Rust:
https://codeberg.org/jarkko/linux-tpmdd-test/commit/642955a3fa7515c1656bd3ce594dcfb5164b2e43
https://codeberg.org/jarkko/linux-tpmdd-test/commit/642955a3fa7515c1656bd3ce594dcfb5164b2e43
Jarkko Sakkinen
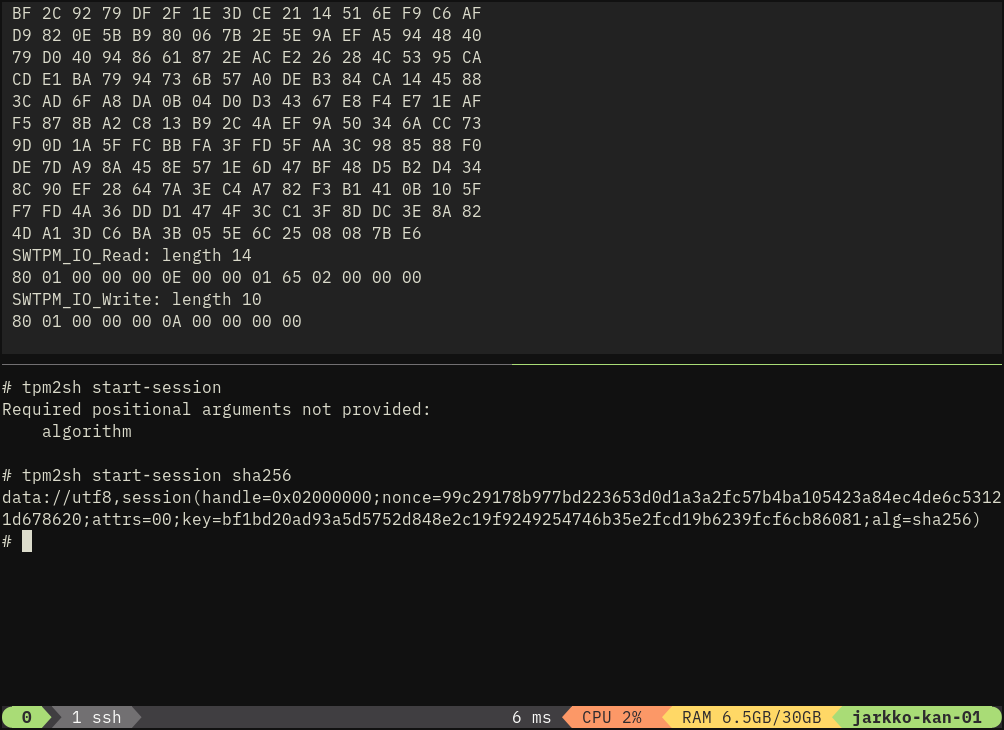
jarkko
and what this gives is factors better debugging environment to fix the remaining external key import issue :-) swtpm dump in the top split
Jarkko Sakkinen
jarkko
awesome, new milestone reached: tpm2sh and tpm2-protocol compile with the Rust toolchain of Buildroot 2025.02.6.
Couple of recursive dependencies needed to be downgraded, and some code tweaks but nothing heavy (phew). I also found that even you set your edition to 2021, the chances are that there is some nested dependency that is allowed to be in edition 2024.
#buildroot
Couple of recursive dependencies needed to be downgraded, and some code tweaks but nothing heavy (phew). I also found that even you set your edition to 2021, the chances are that there is some nested dependency that is allowed to be in edition 2024.
#buildroot
Jarkko Sakkinen
jarkko
A good exercise for Rust code IMHO in order to get it to the level that actually is fluent in production is to create BuildRoot package for it ;-)
All sorts of minor tweaks have had to done for tpm2sh and tpm2-protocol in order to get them to my kernel testing images.
Or at least a good exercise if planning to target and scale Rust crate to embedded systems (in production).
#buildroot #rust
All sorts of minor tweaks have had to done for tpm2sh and tpm2-protocol in order to get them to my kernel testing images.
Or at least a good exercise if planning to target and scale Rust crate to embedded systems (in production).
#buildroot #rust
Jarkko Sakkinen
jarkko
Edited 1 month ago
I've started to support more proactively TrenchBoot efforts because D-RTM despite being a bit rough compared to enclaves, is at least fully open. It also draws me a positive picture about Oracle as a company as it proves to me that they push technologies to upstream that don't only support Oracle's proprietary technologies but also is benefical work for the wider developer ecosystem (unlike e.g., Intel and AMD). It's good cause IMHO plain and simple.
Jarkko Sakkinen
jarkko
my favorite patches are those that rip of over 100 lines of code :-) https://lore.kernel.org/linux-integrity/20250919112448.2543343-1-jarkko@kernel.org/T/#u
Jarkko Sakkinen
jarkko
Edited 1 month ago
rasn crate is the best thing for custom ASN.1 parsers imho:
https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2sh.git/tree/src/key/tpm_key.rs?h=main
See: https://github.com/librasn/rasn
https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2sh.git/tree/src/key/tpm_key.rs?h=main
See: https://github.com/librasn/rasn
Jarkko Sakkinen
jarkko
expected too that there's end boss fight with different external key types, such as PKCS#8 and SEC1 and import ;-) this will slowly uncover...