Posts
4937Following
327Followers
492OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoE.g., most of the time you don't have to specify parent key, the tool will discover it for you.
I'll also implement virtual persistent handles by retaining in cache TPMKey ASN.1 file in addition to context and that enables to implement fake evict operation to 0x81-range.
And already now management of TPM2 sessions is mostly transparent like it should be, and implicitly created HMAC sessions will gain parameter encryption soon.
In pre-existing TPM2 stacks (e.g., tpm2-tool) having sessions exposed out naked to the user is like having a TLS stack where you would need manually implement session key exchange dance. It's just plain fucking wrong imho :-)
#tpm2sh
AGRO TURBO.EXE SNAKE 🇺🇦🇨🇿
lkundrak@metalhead.clubbreaking: white house being replaced by a white trailer park
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoFor VM/embedded images socat is pretty alternative to curl as it has 50% less dependencies and you can still web e.g.,
printf 'GET / HTTP/1.1\r\nHost: www.iki.fi\r\nConnection: close\r\n\r\n' | socat OPENSSL:www.iki.fi:443 -
I’ve replaced curl with socat in my BuildRoot images for kernel testing because it is less bloated than curl ;-)
Jarkko Sakkinen
jarkkoBasing immutablity to a label makes crates.io quite unrobust IMHO, and given that not all projects fly that far, otherwise useful labels stay reserved permanently, up until Sun melts.
Such dual-name scheme could be transparent to Cargo.toml: e.g. Cargo.lock could map a label to a name.
I'm not saying that names would need to have expiration time. I'm thinking more like willingly giving name back to circulation from abandoned project.
C++ has bunch of offerings now for cargo alike package managers. In that front, I'd try to find a solution that is smarter than Cargo before there is a dominating solution.
#rustlang #cargo
Jarkko Sakkinen
jarkko[1] https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkohttps://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2sh.git/tree/src/wildcard.rs?h=main
made a little wildcard parser last night so that I don’t have to implement docker esque “tpm2sh reset” command.
e.g. cache can be reseted now by tpm2sh delete 'vtpm:*'
Jarkko Sakkinen
jarkkohttps://crates.io/crates/tpm2sh
#linux #rustlang #tpm
Jarkko Sakkinen
jarkkoJarkko Sakkinen
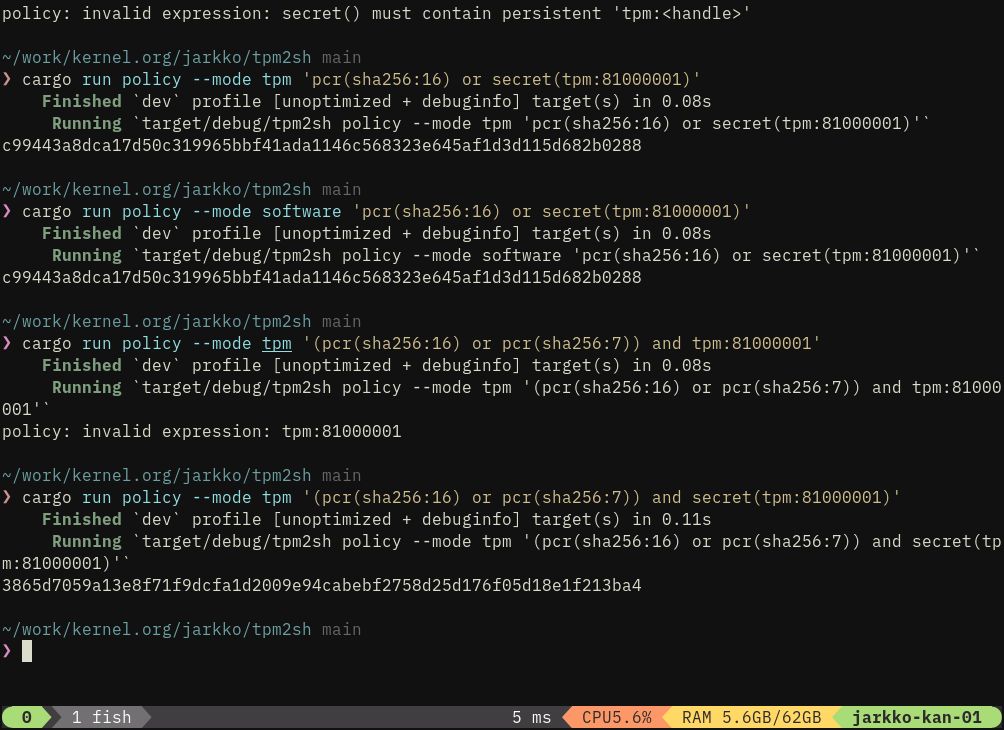
jarkkoI’m planning to iteratively make tpm2sh policy subcommand to compile policy expressions first into eBPF i.e., --mode ebpf option.
We can use this to address bottleneck in trusted keys in kernel: TPMKey ASN.1 provides key blob but not steps how to create policy session that authorizes the key.
Today: TpmKey ASN.1 with auth value and policy digest can be passed but really only auth value (+ PCR selection in TPM2_Create) can be used for authentication.
My vision for policy protected keys is basically:
- Key data is passed as TPMKey ASN.1 just like today.
- In addition eBPF program for creation policy session is passed when policy digest is used.
It’s perfectly secure given that a malicious eBPF program would end up to a different policy digest than what is associated with the key.