Posts
5053Following
330Followers
505OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkoUseful #kernel feature for #hibernate might be a file that would tell the number of pages required for hibernate.
The "O-figure" for hibernate is AFAIK O(n+sqrt(n)) but exact number is dependent on kernel internals but in theory could be calculated by simulating the process without committing.
Instead of swap it might also be useful to have "spare" volume of ~100 GB for doing hibernate and e2scrub type of operations, which could have its own design for encryption etc. Swap for swapping overcommitted memory more than few at most GiB is not that useful these days.
#linux
Jarkko Sakkinen
jarkkoOn the bright side, it means that US has no age racism I guess then 🤷
Marcus "MajorLinux" Summers
majorlinux@toot.majorshouse.comI feel like if you are going to take time to talk to Tucker Carlson, you deserve everything that's about to come to you.
I do, however, hope nothing happens to the users.
Telegram says it has 'about 30 engineers'; security experts say that's a red flag | TechCrunch
https://techcrunch.com/2024/06/24/experts-say-telegrams-30-engineers-team-is-a-security-red-flag/
Jarkko Sakkinen
jarkko1. Guantanamo Bay
2. ADX Florence
This is not same as saying that I would fully support all the choices and values of the person in question.
Jarkko Sakkinen
jarkkoAnyway, congrats to Mr Tanenbaum, well deserved! Only thing that surprises me is that why he did receive ACM award earlier than this.
https://vu.nl/en/news/2024/andrew-s-tanenbaum-receives-acm-software-system-award
#minix #linux #acm
Phoronix
phoronix@masto.aiNUMA Emulation Yields "Significant Performance Uplift" To Raspberry Pi 5
Engineers at consulting firm Igalia are exploring NUMA emulation for ARM64 (AArch64) due to the potential of "significant" performance uplift as observed on the popular Raspberry Pi 5 single board computer...
https://www.phoronix.com/news/ARM64-NUMA-Emulation-RPi5
Jarkko Sakkinen
jarkkoFor me it feels sometimes that quite many commercial web sites reached their tip point maybe about 10-12 years ago. Since then they've started to add stuff that I don't want, and sometimes even quite controversial features, which I need to then proactively disable.
It's a bit same as with yogurt based food products. Yogurt is a product that does not really develop anymore but still food companies have new versions of this product for every season with supplements added and stuff like that.
So I guess I can draw the conclusion that commercial web reached the "yogurt state" around 2012 :-)
Jarkko Sakkinen
jarkkoWould it be unorthodox for sbsign to use kernel crypto API (optionally) instead of OpenSSL?
One use case for this would be MOK private key that is encrypted while at rest with TPM, and never exposed to CPU.
This would be a great application for the kernel feature that I’m working on i.e. an asymmetric TPM2 key (patch set is slowly getting together, right now at iteration seven).
Just to name an example, this is how Ubuntu manages that key as of today: https://wiki.ubuntu.com/UEFI/SecureBoot/Signing. [for the record, Ubuntu is not doing worse job in this than anyone else, they just have awesome documentation, thus the example]
Jarkko Sakkinen
jarkkosq is #openpgp implementation: https://sequoia-pgp.org/
I wonder if sequoia can git tag -s?
Also need to test if smartcard support is already working https://sequoia-pgp.org/blog/2021/12/20/202112-openpgp-card-ci/
And most importantly has a gpg-agent implementation: https://lib.rs/crates/sequoia-gpg-agent. But have to check how stable that is.
These three are minimum set of features that any OpenPGP implementation needs to fully support in order to be compatible with kernel development workflows.
Jarkko Sakkinen
jarkkoPaskajärven kaunis Charlotta
menneisyytesi@eliitin-some.fiKun juhannusyönä pistät seitsemän yrttiä ja kukkaa tyynyn alle, niin Kela määrittelee sinut maatalousyrittäjäksi ja näet unta presidentti Väyrysestä
Threema
threemaapp@mastodon.socialEU Commission: “End encryption!”
Internet users: “End-to-end encryption!”
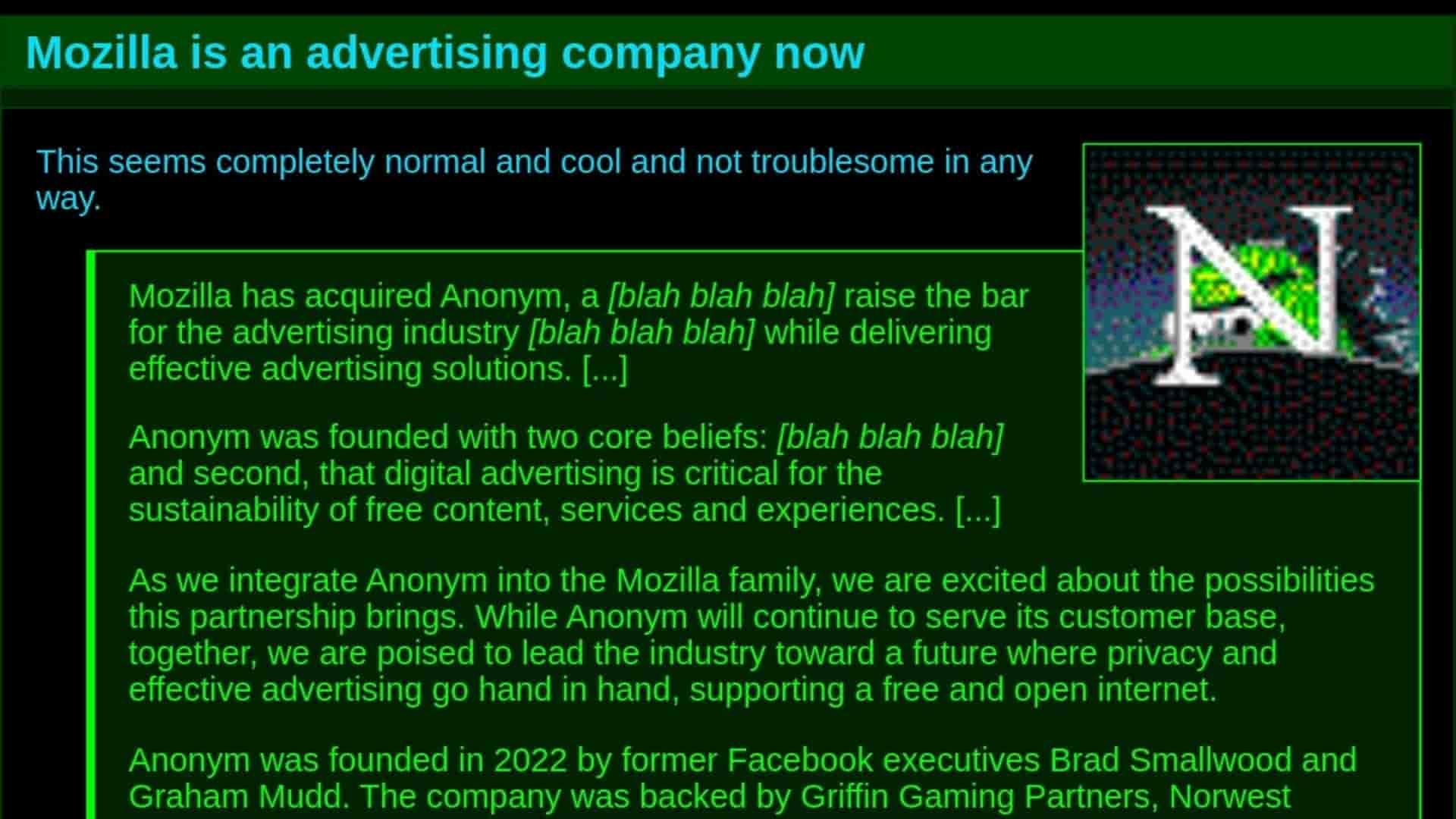
Mozilla is an advertising company now.
This seems completely normal and cool and not troublesome in any way.
Mozilla has acquired Anonym, a [blah blah blah] raise the bar for the advertising industry [blah blah blah] while delivering effective...
https://jwz.org/b/ykVg
Jarkko Sakkinen
jarkkoI like how unlayered this is, i.e. at most two subsystems layered and stack is at its heaviest a file system + LUKS2 volume (i.e. no one to many relationships). Less risk of busy file systems that cannot be unmounted at least :-)
Jarkko Sakkinen
jarkkoThere’s first time for everything and this my first time with UKI :-)
==> Building image from preset: /etc/mkinitcpio.d/linux.preset: 'default'
==> Using default configuration file: '/etc/mkinitcpio.conf'
-> -k /boot/vmlinuz-linux -U /efi/EFI/Linux/arch-linux.efi --splash /usr/share/systemd/bootctl/splash-arch.bmp
==> Starting build: '6.9.5-arch1-1'
-> Running build hook: [base]
-> Running build hook: [systemd]
-> Running build hook: [autodetect]
-> Running build hook: [modconf]
-> Running build hook: [kms]
-> Running build hook: [keyboard]
==> WARNING: Possibly missing firmware for module: 'xhci_pci'
-> Running build hook: [sd-vconsole]
-> Running build hook: [sd-encrypt]
==> WARNING: Possibly missing firmware for module: 'qat_420xx'
-> Running build hook: [block]
-> Running build hook: [filesystems]
-> Running build hook: [fsck]
==> Generating module dependencies
==> Creating zstd-compressed initcpio image
-> Early uncompressed CPIO image generation successful
==> Initcpio image generation successful
==> Creating unified kernel image: '/efi/EFI/Linux/arch-linux.efi'
-> Using cmdline file: '/etc/kernel/cmdline'
==> Unified kernel image generation successful
==> Building image from preset: /etc/mkinitcpio.d/linux.preset: 'fallback'
==> Using default configuration file: '/etc/mkinitcpio.conf'
-> -k /boot/vmlinuz-linux -U /efi/EFI/Linux/arch-linux-fallback.efi -g /boot/initramfs-linux-fallback.img -S autodetect
==> Starting build: '6.9.5-arch1-1'
-> Running build hook: [base]
-> Running build hook: [systemd]
-> Running build hook: [modconf]
-> Running build hook: [kms]
==> WARNING: Possibly missing firmware for module: 'ast'
Jarkko Sakkinen
jarkkoZig fluid interaction with C and C++ make it feel bit like Objective-C.
I’m experimenting if I could refurnish irssi-matrix with the idea of rendering out matrix-glib dependency, which make the barrier to improve actual features of the plugin a real pain.
To make things worse, the plugin is using a fork of matrix-glib (for good reasons tho because it not actively maintained).
I’m using the JSON parser that is part of Zig’s stdlib for the purpose. This could turn out to be something nice…
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoQuite amazing.
[1] https://www.uber.com/en-FI/blog/bootstrapping-ubers-infrastructure-on-arm64-with-zig/ #ueber #zig