Posts
5167Following
335Followers
509OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkko#Bitwig 5.2 is best update since I started because it replaces so many external plugins with stock options:
- A dedicated clipper called Over (substitutes StandardClip).
- A glue compressor Compressor+ (substitutes The Glue).
- A a tilt EQ (substitutes Things Flip EQ).
It is the first version at least where I’m actually able to draft a track without VSTs. Especially lack of proper bus compressors has been an itch when migrating from #Ableton Live.
Jarkko Sakkinen
jarkkoCool got some response from rust-vmm/vm-memory people, asking to give more details, which I will provide next week.
#Enarx is a kind of hybrid #VMM, and I think this is exactly where I think the overall rust-vmm umbrella has the best opportunities. I.e. instead of just hosting guests with QEMU you might want to do a tailored VMM below to get the optimal characteristics in performance, security and whatnot for your use case.
Enarx hosts #WebAssembly payloads in confidential computing environment. To realize those it:
- Uses #KVM API to bootstrap wasm run-time inside a #AMD SEV-SNP VM.
- Uses
/dev/sgxto partition address space for boostrapping a wasm run-time inside an #Intel SGX enclave.
The first one is very surgically constructed VM with all access outside it disable, and the second is not actually VM at all.
My take is here that any commercially viable memory API should first of all scale to all possible types on VM’s, and also address stuff “on the edges of universum”, e.g. SGX enclaves, which in many ways resemble VM’s (at least to some level).
Rich Stein (he/him)
RunRichRun@mastodon.socialSecurity Firm Discovers Remote Worker Is Really a North Korean Hacker —
"The incident occurred at KnowBe4, which develops security awareness programs to teach employees about phishing attacks and cyber threats. The company recently hired a remote software engineer who cleared the interview and background check process. But last week, KnowBe4 uncovered something odd after sending the employee a company-issued Mac." https://www.pcmag.com/news/security-firm-discovers-remote-worker-is-really-a-north-korean-hacker
#Oops
kim_harding ✅
kim_harding@mastodon.scotClimate Change Actions Are Far More Popular Than People in U.S. Realize
https://www.scientificamerican.com/article/climate-change-actions-are-far-more-popular-than-people-in-u-s-realize/
“False social reality” obscures widespread U.S. support for climate protection measures
Not just the US, this is a global problem #DontLookUp
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoI wonder what I need to do to make that tick and how do you get a VGA adapter for it.
Jarkko Sakkinen
jarkko#holiday activities (last week ongoing).
I learned how to compile DOS COM executables with the latest GCC. It can be done with a trivial LD script, i.e. dump to 0x100. It has a memory topology of single 16-bit code and data segment.
I also learned that event with ELF toolchain “-nostdlib” is still required because crt0.o is not compatible with MS-DOS.
I also implemented couple of features for this “not for profit MS-DOS framework”:
- At launch visit in the protected mode and load GDT with code segment according to real-mode, limit for data segment set to 4GB, and return back to the real mode. CPU will just use the latest cached descriptors. This means that BIOS calls continue to work but data can be accessed with the full 32-bit address space, because x86 has opcode prefixes in real mode for 32-bit registers.
- Setup 320x240 256 color planar mode based on tweaking various VGA registers (invented by Michael Abrash originally). It has square pixels and can address multiple, and can page flip by setting the new address to CRT index port.
Not sure what I’m going to do with this next but no rush with MZ EXE (I have idea how approach that w/o sacrificing modern tools) because 64 kB is enough for some time, and I have no data limit ;-)
Jarkko Sakkinen
jarkkonote to myself: when #zsh completions are not working as expected in any OS, 9/10 times it is missing -u flag for compinit ;-) Had forgotten this.
From zshcompsys man page:
To avoid these tests and make all files found be used without asking, use the option -u, and to make compinit silently ignore all insecure files and directories use the option -i. This security check is skipped entirely when the -C option is given.
Jarkko Sakkinen
jarkkoThis could be realized in practical manner for instance in a future version of #CLAP, which could have up-calls whose API signatures would be along the lines with stuff commonly used for from Win32 API. I.e. basic graphics context stuff, file picker etc. Most of the plugins neither sample nor produce audio. They are just plain data processors with a fancy GUI.
A plugin using only those API's would be universal to all operating systems.
And since PE/COFF is widely know format and used across the operating systems for EFI support, DLL would be perfect format for the binary. That way one could have plugin binary that is cross-operating system compatible. I.e. host would implement the API and provide PE/COFF loader to initialize the plugin.
In addition to PE/COFF there should probably be target for wasm, which would enable plugin ecosystem for web daw's.a
https://www.youtube.com/watch?v=H5v0CK249rI
#MusicProduction
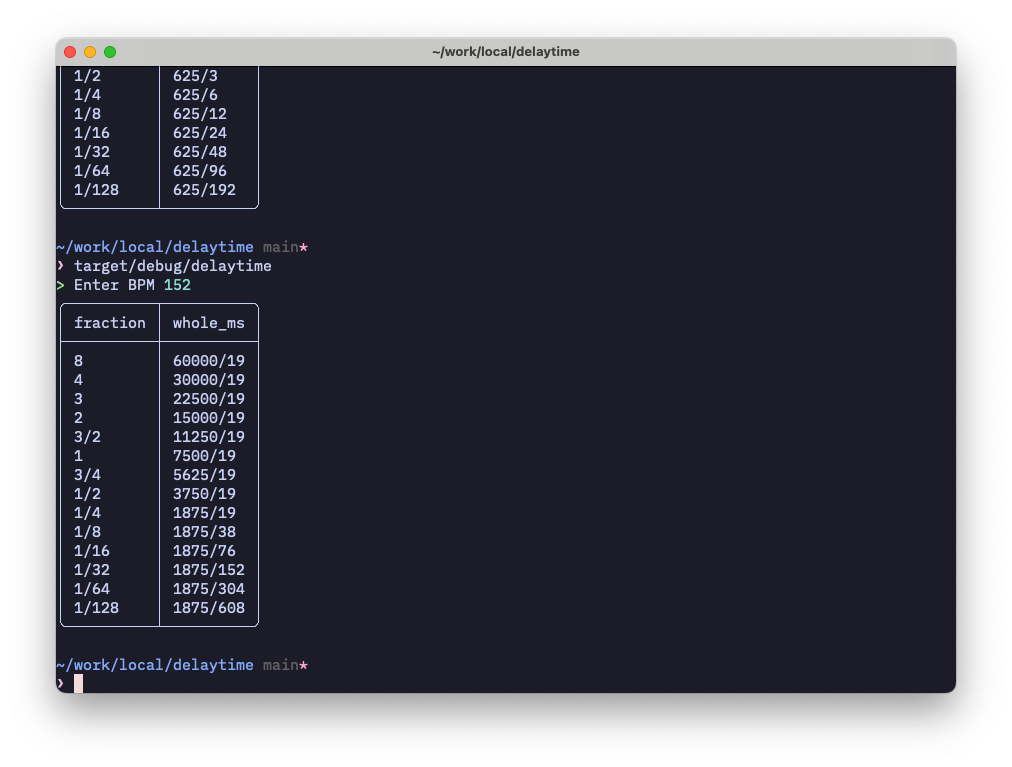
Jarkko Sakkinen
jarkkoGreat I get in my “hello bpf” truncated stacks delivered through a ringbuf:
❯ sudo build/hello-ebpf
[0]: 0xffffa5c74e6e9498
[1]: 0x0000000000000000
[2]: 0x0000000000000000
[3]: 0x0000000000000000
[4]: 0x0000000000000000
[5]: 0x0000000000000000
[6]: 0x0000000000000000
[7]: 0x0000000000000000
It looks like this because I temporarily hooked kprobe to a syscall. Next I change the hook to tpm_transmit.
I do all post-processing from this at the host.
Jarkko Sakkinen
jarkko#iLok comes much more nicer to use once you discover by accident that there is a command-line tool installed to /usr/local/bin
iloktool - 5.9.0 (b5097, edaa5278, Release, 64 bit, built Oct 25 2023)
Copyright 2023, PACE Anti-Piracy, Inc., All rights reserved. CONFIDENTIAL.
Usage: iloktool <operation> <options>
<operation> is one of the following:
help Prints this help message.
auths Show all of the authorizations (licenses) available to your computer.
cloud --open Open an iLok cloud session. Requires --account & --password for the iLok account.
cloud --close Close all iLok cloud sessions or with --account & --password close a single session.
cloud --status Returns the cloud status: "Open" or "Closed".
list List iLok devices attached to this machine.
<options>:
-h [ --help ] Show these usage instructions.
-a [ --account ] arg This is the account login ID in the "cloud" operation.
-c [ --close ] This is used with the "cloud" operation to close all or
a single open cloud session.
-o [ --open ] This is used with the "cloud" operation to open a cloud
session.
-p [ --password ] arg This is the account password for the "cloud" operation.
-s [ --status ] This is used with the "cloud" operation to get the
cloud status (Open or Closed).
-t [ --type ] arg If specified, this filters the "list" operation by the
specified iLok type.
-V [ --version ] Show the version number.
-v [ --verbose ] Indicate verbose output.
Examples (omit the -v at the end if you don't want verbose):
If you specify no operation, you get a non-verbose list of all local and
remote iLoks:
iloktool
List all, just iLok1, just iLok2 and just iLok3 type devices respectively:
iloktool list -v
iloktool list --type 1 -v
iloktool list --type 2 -v
iloktool list --type 3 -v
Display all auths (licenses) available to your computer:
iloktool auths -v
Open a cloud session, close a cloud session, close all cloud sessions or get
cloud status respectively:
iloktool cloud --open --account your_account --password your_password -v
iloktool cloud --close --account your_account --password your_password -v
iloktool cloud --close -v
iloktool cloud --status -v
Once you successfully use your account and password to open or close a cloud
session, your password will be saved in the computer's key chain, and you can
omit the password in subsequent open and close operations:
iloktool cloud --open --account your_account -v
iloktool cloud --close --account your_account -v
I used to hate iLok but these days I think that it would best if all #audio #plugin companies would use the only solution that has matured somewhat usable instead of inventing their own factors worse licensing schemes.
Jarkko Sakkinen
jarkko#C #cplusplus
Jarkko Sakkinen
jarkkoLife hack for github-cli gh repo clone $(printf 'squidowl/halloy%.0s ' {1..2}), i.e. clone into owner/repo directory, not just repo. #github
EDIT:
I wrote a small #bash (obviously works also for #zsh) function to make cloning easier in my environment:
gh-repo-work() {
local url=$1
# Strip path from URL:
local url_path=${url#*\.*/}
# Clone to the Github tree:
gh repo clone $url_path "$HOME/work/github/$url_path"
}
“Demo”:
~ main*
❯ gh-repo-work m4b/goblin
Cloning into '/Users/jarkko/work/github/m4b/goblin'...
remote: Enumerating objects: 7261, done.
remote: Counting objects: 100% (1215/1215), done.
remote: Compressing objects: 100% (326/326), done.
remote: Total 7261 (delta 977), reused 922 (delta 889), pack-reused 6046
Receiving objects: 100% (7261/7261), 3.22 MiB | 4.69 MiB/s, done.
Resolving deltas: 100% (5565/5565), done.
~ main*
❯ ls -1 work/github/m4b/goblin
CHANGELOG.md
Cargo.toml
LICENSE
Makefile
README.md
assets
etc
examples
fuzz
fuzz-afl
src
tests
~ main*
❯ rm -rf work/github/m4b/goblin
~ main*
❯ gh-repo-work https://github.com/m4b/goblin
Cloning into '/Users/jarkko/work/github/m4b/goblin'...
remote: Enumerating objects: 7261, done.
remote: Counting objects: 100% (1227/1227), done.
remote: Compressing objects: 100% (337/337), done.
remote: Total 7261 (delta 988), reused 923 (delta 890), pack-reused 6034
Receiving objects: 100% (7261/7261), 3.23 MiB | 6.68 MiB/s, done.
Resolving deltas: 100% (5564/5564), done.
~ main*
❯ ls -1 work/github/m4b/goblin
CHANGELOG.md
Cargo.toml
LICENSE
Makefile
README.md
assets
etc
examples
fuzz
fuzz-afl
src
tests
Paul Chaignon
pchaigno@hachyderm.ioThe list of papers accepted at the 2nd #eBPF workshop has been published by ACM: https://dl.acm.org/doi/proceedings/10.1145/3672197#tableOfContent.
Jarkko Sakkinen
jarkkoThe main reason is the bouncer they have in it that "just works" without even trying: https://blog.irccloud.com/bouncer/
If I ever build a company I will get IRCCloud Teams instead of Slack ;-)