Posts
5020Following
329Followers
500OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoMy colleague also said that as bonus it helps to keep your house warm so I guess it is shopping time...
#rust
Jarkko Sakkinen
jarkkohttp://ccrma.stanford.edu/planetccrma/software/
Lennart Poettering
pid_eins@mastodon.social5️⃣ Here's the 5th installment of posts highlighting key new features of the upcoming v257 release of systemd.
Since its beginnings systemd was a heavy user of the D-Bus IPC system. It provides D-Bus APIs, it calls D-Bus APIs it schedules activation of the D-Bus broker, and even provides its own C D-Bus client library.
However, since early on our use of D-Bus was not without various major problems. One of the biggest goes something like this:
Jarkko Sakkinen
jarkkoAfter trying different approaches of using clangd with kernel my end game is to put O=./clangd for the “clangd build”, which is a host (as target) build with bunch of stuff that you want enable. This makes sense because kernel’s .gitignore has by default .*.
I also learned that for the “real Vim” (not “Gen Z vim”) there is actually quite decent set of plugins to make use of it. Here’s my vim-plug list:
Plug 'mattn/vim-lsp-settings'
Plug 'prabirshrestha/asyncomplete-lsp.vim'
Plug 'prabirshrestha/asyncomplete.vim'
Plug 'prabirshrestha/vim-lsp'
This is how I would ramp up clangd session while hacking Linux:
make ARCH=x86_64 O=./.clangd x86_64_defconfig
make ARCH=x86_64 O=./.clangd menuconfig
make ARCH=x86_64 O=./.clangd -j`nproc`
scripts/clang-tools/gen_compile_commands.py -d ./.clangd
Jarkko Sakkinen
jarkkoThus, OpenWRT designing their own reference router called OpenWRT One is great news, and have to link the associated LWN article just to promote it:
https://lwn.net/Articles/994961/
#openwrt #buildroot #lwn
Jarkko Sakkinen
jarkkoTrying to make a new version of my “TPM2 signers” patch set and stumbling into a weird problem.
Here’s the script I’m looking at:
#!/usr/bin/env bash
set -e
PRIMARY=0x81000001
function egress {
keyctl clear @u
tpm2_evictcontrol -C o -c $PRIMARY 2> /dev/null
tpm2_getcap handles-transient
tpm2_getcap handles-persistent
}
trap egress EXIT
openssl ecparam -name prime256v1 -genkey -noout -out ecc.pem
openssl pkcs8 -topk8 -inform PEM -outform DER -nocrypt -in ecc.pem -out ecc_pkcs8.der
tpm2_createprimary --hierarchy o -G ecc -c owner.txt
tpm2_evictcontrol -c owner.txt $PRIMARY
# EC parameters to TPM2 blob:
tpm2_import -C $PRIMARY -G ecc -i ecc.pem -u tpm2.pub -r tpm2.priv
# TPM2 blob to ASN.1:
tpm2_encodeobject -C $PRIMARY -u tpm2.pub -r tpm2.priv -o tpm2.pem
openssl asn1parse -inform pem -in tpm2.pem -noout -out tpm2.der
# Populate asymmetric keys:
tpm2_ecc_key=`keyctl padd asymmetric "tpm_ecc" @u < tpm2.der`
kernel_ecc_key=`keyctl padd asymmetric "kernel_ecc" @u < ecc_pkcs8.der`
echo "SECRET" > doc.txt
echo TPM2 ECC SIGN
keyctl pkey_sign $tpm2_ecc_key 0 doc.txt hash=sha256 > doc.txt.sig
echo TPM2 VERIFY
keyctl pkey_verify $kernel_ecc_key 0 doc.txt doc.txt.sig
The error message generated is:
keyctl_pkey_verify: Invalid argument
If I verify with the TPM2 ECC key /it will pass, in other words replacing the list statement with:
keyctl pkey_verify $tpm2_ecc_key 0 doc.txt doc.txt.sig hash=sha256
In the final version I’m going to remove signature verification from TPM2 ECC key as that is kind of the point here: sign certificate with a private key protected by TPM and allow any party verify the signature with the known public key.
Jarkko Sakkinen
jarkko1. https://lore.kernel.org/linux-integrity/D5CYH0IJXX72.35A25M1YICZRP@kernel.org/T/#u
2. https://bugzilla.kernel.org/show_bug.cgi?id=219383
This bug for early weeks of the current release cycle has already landed: https://bugzilla.kernel.org/show_bug.cgi?id=219229
Right now that I don't do kernel as my main job I prioritize users instead kernel developers when picking fixes for during the cycle PR's :-) Other fixes can wait until 6.13 PR.
#linux #kernel
Jarkko Sakkinen
jarkkoThe “convenience of LSP” with kernel:
make ARCH=x86_64 O=../linux-tpmdd-clangd x86_64_defconfig
make O=../linux-tpmdd-clangd/ CC="ccache gcc" -j`nproc`
scripts/clang-tools/gen_compile_commands.py -d ../linux-tpmdd-clangd
This is least distracting way I’ve found to use it (I use it only with VSCodium when just browsing around):
- Uses host architecture (target architecture can be “whatever”).
- Uses defconfig that works well for this task.
- Does not disturb other uses of the Git tree.
E.g. I use LINUX_OVERRIDE_SRCDIR a lot with BuildRoot and usually clean kernel directory in such cases causes least troubles…
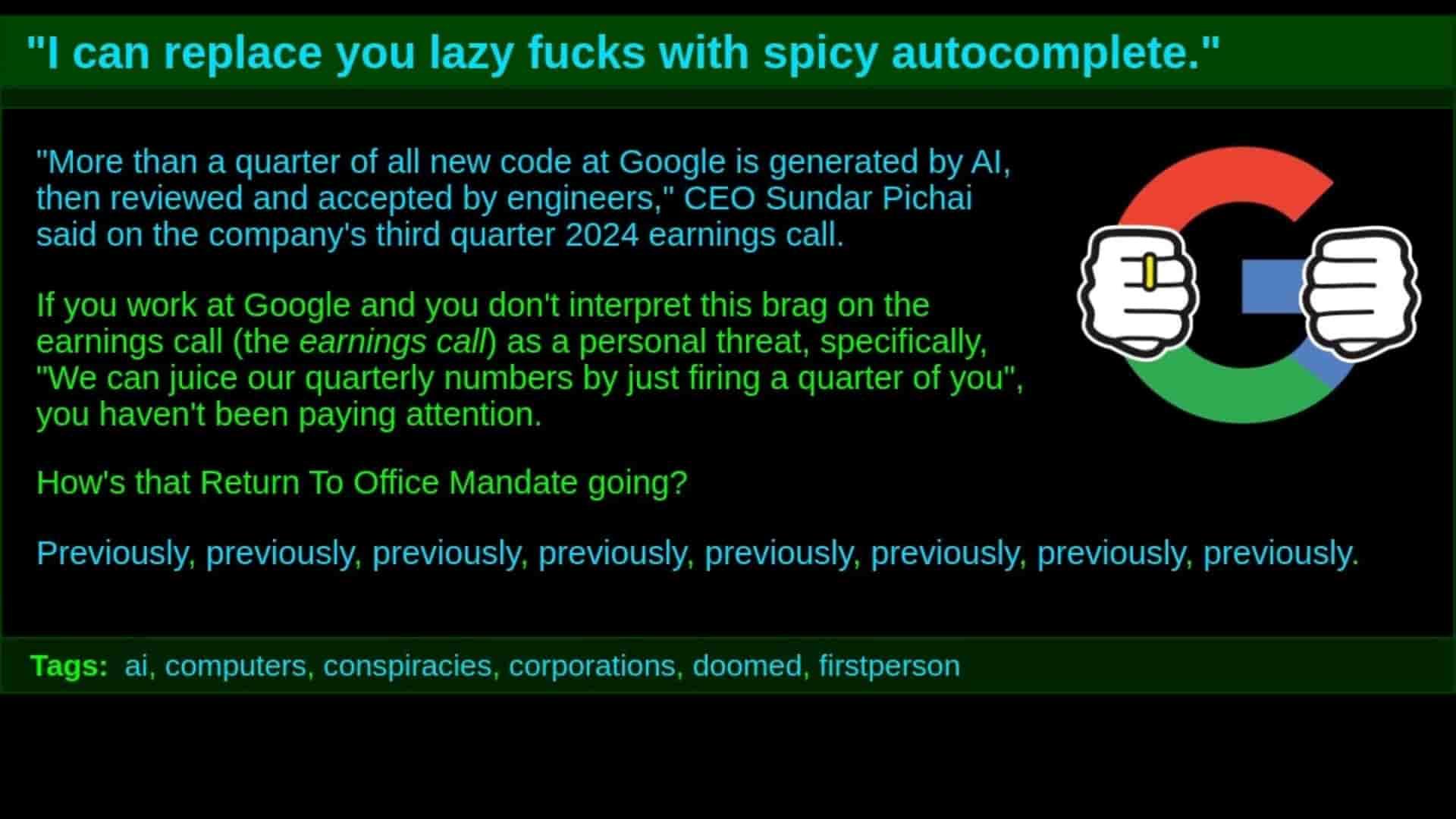
"I can replace you lazy fucks with spicy autocomplete."
"More than a quarter of all new code at Google is generated by AI, then reviewed and accepted by engineers," CEO Sundar Pichai said on the company's third quarter 2024 earnings call. If you work...
https://jwz.org/b/ykb8
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
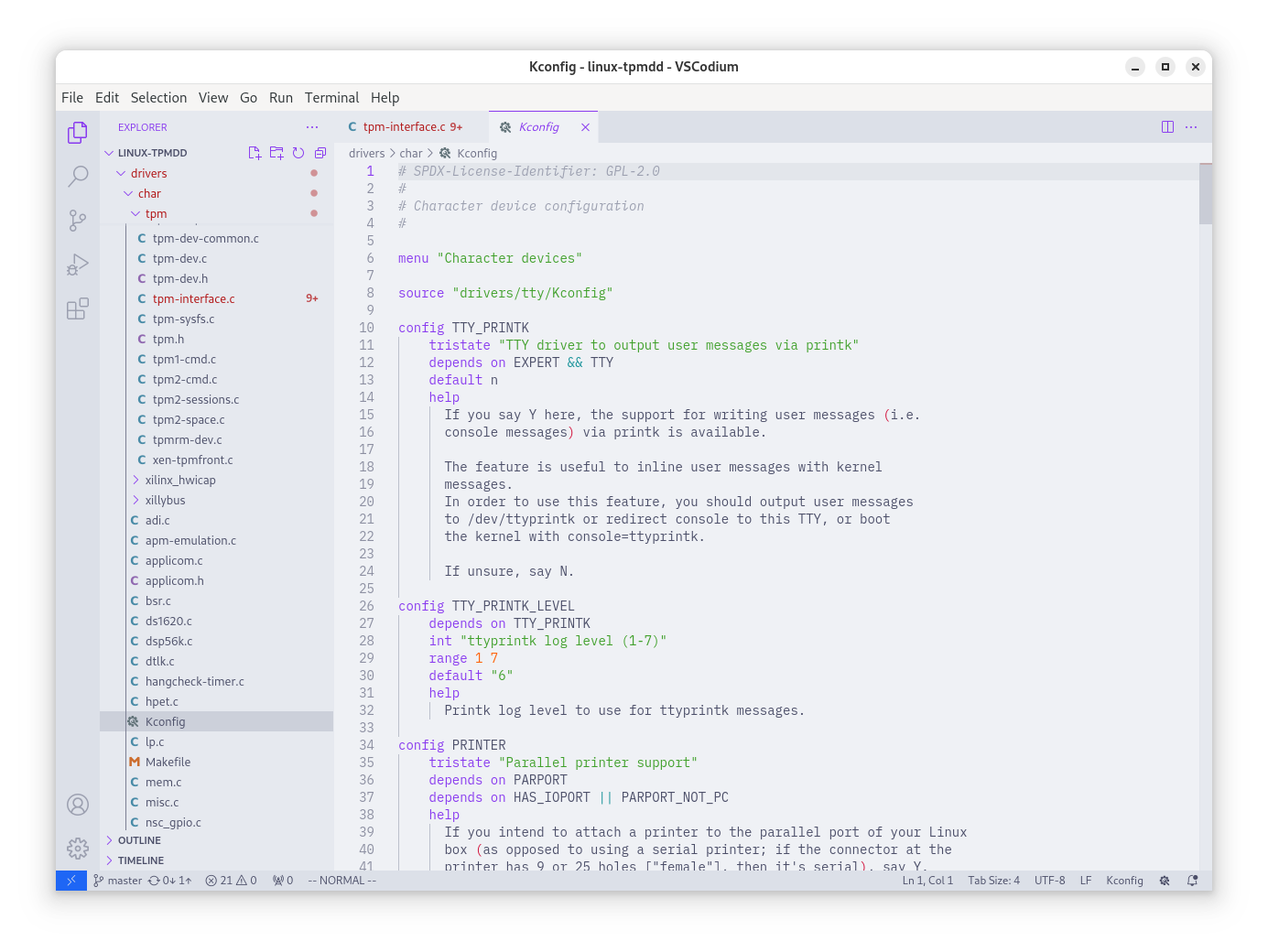
jarkkoLearned how to install a “VSCode only” extension to VSCodium:
- Go to a page: https://marketplace.visualstudio.com/items?itemName=nordic-semiconductor.nrf-kconfig
- Download vsix.
codium --install-extension nordic-semiconductor.nrf-kconfig-2024.9.20.vsix
Now Kconfig looks pretty ;-)
Jarkko Sakkinen
jarkkoAll other audio ports suck. It's the literal truth. It's the killer feature in Apple products.
Try to connect your Thinkpad directly to a stage sound system and it will be hell. This applies to all PC laptops I've ever tried.
Why it is like this?
I don't have personal laptop at the moment but soon going to get a new one, and it definitely will be Apple laptop, and it is ONLY because of 3,5mm audio port.
Noteworthy is that also the latency metrics of Apple's audio are in par with an external audio interface.
#laptop #audio #apple