Posts
5116Following
331Followers
505OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkko
Edited 5 months ago
zero issues advertising this as i think it really does right things right:
https://github.com/himmelblau-idm/himmelblau/issues/662
buffering and parsing this protocol stream is just one thing i have pretty solid grip off so why not make best of it
https://github.com/himmelblau-idm/himmelblau/issues/662
buffering and parsing this protocol stream is just one thing i have pretty solid grip off so why not make best of it
Jarkko Sakkinen
jarkko
the uncrowned king of RS-232 file transfer protocols: https://en.wikipedia.org/wiki/SMODEM
Jarkko Sakkinen
jarkko
lifting weights felt great after three week break :-) that's the timeline for tpm2-protocol. it was unhealthy stretch as fuck but now it is done and my rust concerns have been mitigated!
i'm ready and i've fully prepared the next five year plan in the linux kernel, and more specifically in kernel sec...
i'm ready and i've fully prepared the next five year plan in the linux kernel, and more specifically in kernel sec...
Jarkko Sakkinen
jarkko
new uri based json stack with tpm and key objects depending on binding etc. and things start to actually work.
Jarkko Sakkinen
 repeated
repeated
Canonical Ubuntu
ubuntu@ubuntu.socialHappy birthday, Linux! 🐧🎂
Here’s to 34 years of open source, community, and innovation.
Jarkko Sakkinen
jarkko
(sort of) EOF for this project:
https://lore.kernel.org/tpm2/aKzaTYCI2GO_UPRB@kernel.org/T/#u
The thing that really did not exist before is there, features too, stability most likely not, processes and constraints are adequate for the goals and purpose 🤷
#linux #kernel #tpm #rust
https://lore.kernel.org/tpm2/aKzaTYCI2GO_UPRB@kernel.org/T/#u
The thing that really did not exist before is there, features too, stability most likely not, processes and constraints are adequate for the goals and purpose 🤷
#linux #kernel #tpm #rust
Jarkko Sakkinen
jarkko
Edited 5 months ago
I had these shitty with_* wrappers for doig shit with handles in tpm2sh.
Now I'm switching to Drop traits + threadpool i.e. pretty much what every other driver does in kernel with workqueue, so using a known good pattern.
As I've understood it (might be wrong too please correct) e.g., in a Drop trait implementation it is disallowed to block.
[in drivers you tend to do this a lot e.g., given possible race conditions with fput() and releasing the resources]
Now I'm switching to Drop traits + threadpool i.e. pretty much what every other driver does in kernel with workqueue, so using a known good pattern.
As I've understood it (might be wrong too please correct) e.g., in a Drop trait implementation it is disallowed to block.
[in drivers you tend to do this a lot e.g., given possible race conditions with fput() and releasing the resources]
Jarkko Sakkinen
jarkko
Edited 5 months ago
All these TPM bug I've baffled around have nothing to do with tpm2-protocol. It's working perfectly :-) It's all about parameters in tpm2sh.
Two real issues so far after 0.10.0 specifically in tpm2-protocol:
1. I had deleted over half of TPM_RC values from enum during mangling it together. tpm2-protocol did not trip it returned error called InvalidDiscriminant, which also reports the integer value of undefined discriminant.
2. I had ill-defined capacity for couple of things. The error propagation and range checks worked perfectly and returned CapacityExceeded.
It's designed to be zero panic even for unreachable and "impossible" situations and error propagation seems to really work in practice too :-)
At one point I did not having parsing and building traits defined for "i8" as I was not then aware that there was enum with negative discriminants. That already was catched by the compiler as everything has TpmBuild, TpmParse and TpmSized traits down to atoms.
That i8 issue was exactly kind of twist that could easily go into production unnoticed and made me pretty convinced that the "DSL" I've defined actually does work.
Two real issues so far after 0.10.0 specifically in tpm2-protocol:
1. I had deleted over half of TPM_RC values from enum during mangling it together. tpm2-protocol did not trip it returned error called InvalidDiscriminant, which also reports the integer value of undefined discriminant.
2. I had ill-defined capacity for couple of things. The error propagation and range checks worked perfectly and returned CapacityExceeded.
It's designed to be zero panic even for unreachable and "impossible" situations and error propagation seems to really work in practice too :-)
At one point I did not having parsing and building traits defined for "i8" as I was not then aware that there was enum with negative discriminants. That already was catched by the compiler as everything has TpmBuild, TpmParse and TpmSized traits down to atoms.
That i8 issue was exactly kind of twist that could easily go into production unnoticed and made me pretty convinced that the "DSL" I've defined actually does work.
Jarkko Sakkinen
jarkko
Easiest way to test Windows compilation in Linux for Rust crate?
I'd like to add a target for https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git
I'd like to add a target for https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git
Jarkko Sakkinen
jarkko
i feel like a winner now when I reached TPM_RC_INTEGRITY. this is easy to squash :D crypto works fully or does not work at all
Jarkko Sakkinen
jarkko
day 2 fighting with TPM2_Import. and it's not the first time. the protocol crate is doing nothing wrong, it's a bug in tpm2sh
Jarkko Sakkinen
jarkko
I should have remember by now that for KDFa's you feed "DUPLICATE\0" not "DUPLICATE" and so forth. But no, I fought with TPM_RC_VALUE for half a day.
Jarkko Sakkinen
jarkko
Edited 5 months ago
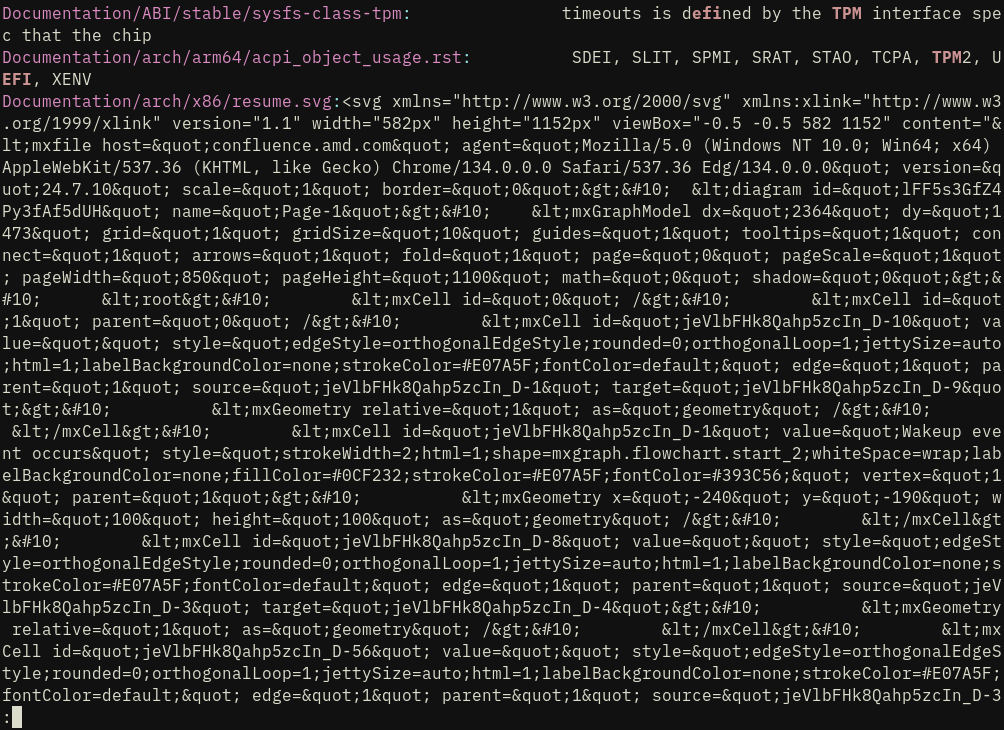
this SVG garbage fuck. is there something we could put .gitattributes, .gitignore or something that would make it not to destroy git grep experience?
Jarkko Sakkinen
jarkko
Edited 5 months ago
Now it is carved to the stone:
https://github.com/puavo-org/tpm2sh/commit/f95d6aae1f5212c39349a77e066b4ceeb2ef580c
I'll need this once I have bandwidth to refine:
https://lore.kernel.org/linux-integrity/20240528210823.28798-1-jarkko@kernel.org/
https://github.com/puavo-org/tpm2sh/commit/f95d6aae1f5212c39349a77e066b4ceeb2ef580c
I'll need this once I have bandwidth to refine:
https://lore.kernel.org/linux-integrity/20240528210823.28798-1-jarkko@kernel.org/
Jarkko Sakkinen
jarkko
Edited 5 months ago
In the sense confidential computing holds it promise that since the hardware is inaccessible by practical means to *everyone*, you need to execute that type of code in your head. It is as confidential at least as computing can ever get [Side-note: even the name of the field is incorrect terminology at least when reflecting on how the terminology is usually defined in the field of information security. The so called "CIA Triad" defines trust as the sum of availability, confidentiality and integrity.]
This is what I literally do with SGX patches:
1. I pick up Intel SDM (which is IMHO pretty good ISA reference overall, zero complains on that).
2. I read the pseudocode for new opcodes or revisit old ones.
3. I look it is applied in kernel patch
4. Finally I "hallucinate" its execution :-----)
And based on this mental execution procedure I ack/nak patches.
You can extrapolate from this that probably most of any type of CoC code in kernel are the least audited areas of the Linux kernel source code. Even if working for a CPU company, it is hard to really hammer the code, if your only access to the hardware is a shitty company cloud.
This is what I literally do with SGX patches:
1. I pick up Intel SDM (which is IMHO pretty good ISA reference overall, zero complains on that).
2. I read the pseudocode for new opcodes or revisit old ones.
3. I look it is applied in kernel patch
4. Finally I "hallucinate" its execution :-----)
And based on this mental execution procedure I ack/nak patches.
You can extrapolate from this that probably most of any type of CoC code in kernel are the least audited areas of the Linux kernel source code. Even if working for a CPU company, it is hard to really hammer the code, if your only access to the hardware is a shitty company cloud.
Jarkko Sakkinen
 repeated
repeated
Jarkko Sakkinen
jarkko
OOPS
it was more than TPM_RC_SIZE :-)
https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git/commit/?id=9ba073e0d924fbeeff4f74a70bc76bbf29380862
0.10.5 released
BR, Jarkko
it was more than TPM_RC_SIZE :-)
https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git/commit/?id=9ba073e0d924fbeeff4f74a70bc76bbf29380862
0.10.5 released
BR, Jarkko