Posts
4778Following
319Followers
489OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkoWith TPM protocol shenanigans people tend to go generation path because writing all data types manually would be ridiculous amount of work.
By creating DSL with macros, "ridiculous" factored down to "huge" but only for the initial pass i.e., to reach the current TCG standard version. And given that I have now efficient DSL, keeping the implementation up to date is almost cost-free. And since none of the compiled code is a generation artifact, it is easy to "shift away" in selected places, and write down traits manually.
Jarkko Sakkinen
jarkkoI’m working on a bash and Makefile based project called “himmelblau-dev”, which provides low-barrier entry point to start contributing to that upstream project. I have not really contributed to that project much because there is no a meaningful edit-compile-run-cycle and that is what I’m resolving with this project.
I’ve taken a lot of trouble to not use containers, not even in the build, because containers always mean looking for problems when translating a development environment from one machine to another.
[To be completely honest, for any possible project I interpret “I have to use a container” into “my solution is going to be a trainwreck”]
Instead, I do the build with a combination of deboostrap and guestfish tricks. The project has makefile targets for running resulting QCOW2 in QEMU, contains a settings file (parser implemented in bash) and automatic download of OVMF images and logic for managing EFI vars file.
It’s a bit like embedded build system centered around a single upstream project.
Layout right now:
❯ tree
.
├── bootstrap
│ ├── settings.sh
│ └── start.sh
├── config
│ ├── debian.sh
│ ├── himmeblau.sh
│ └── start.sh
├── himmelblau.version
├── Makefile
├── qemu.json
├── README.md
└── vm
├── qemu.sh
├── start.sh
└── swtpm.sh
I need to fine-tunet his for a while still before I publish it. It’s all GPL3 license as I see no point of using any other license for this.
qemu.json is just my own ad-hoc VM configuration format:
{
"args": {
"enable-kvm": true,
"machine": "q35,accel=kvm",
"cpu": "host",
"memory": "4G",
"rtc": "base=localtime"
},
"networking": {
"user": [
{ "netdev": "user,id=net0,hostfwd=tcp::10022-:22" },
{ "device": "virtio-net-pci,netdev=net0" }
],
"bridge": [
{ "netdev": "bridge,id=net0,br=br0" },
{ "device": "virtio-net-pci,netdev=net0" }
]
},
"tpm": {
"enabled": true,
"tpmdev": "emulator,id=tpm0,chardev=chrtpm",
"device": "tpm-tis,tpmdev=tpm0"
},
"drives": [
{
"if": "pflash",
"file": "OVMF_CODE.fd",
"format": "raw",
"readonly": "on"
},
{
"if": "pflash",
"file": "OVMF_VARS.fd",
"format": "raw"
},
{
"file": "himmelblau-demo.qcow2",
"format": "qcow2"
}
]
}
Jarkko Sakkinen
jarkkohttps://github.com/puavo-org/tpm2sh/blob/main/src/bin/mock-tpm.rs
Even at this point it still demonstrates how easy it is to get ongoing with previously as complicated task as writing a TPM emulator.
#linux #kernel #tpm #rust
Jarkko Sakkinen
jarkkoPatches and discussion: tpm-protocol@lists.linux.dev
More information: https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git/tree/README.md
#linux #kernel #tpm #rust
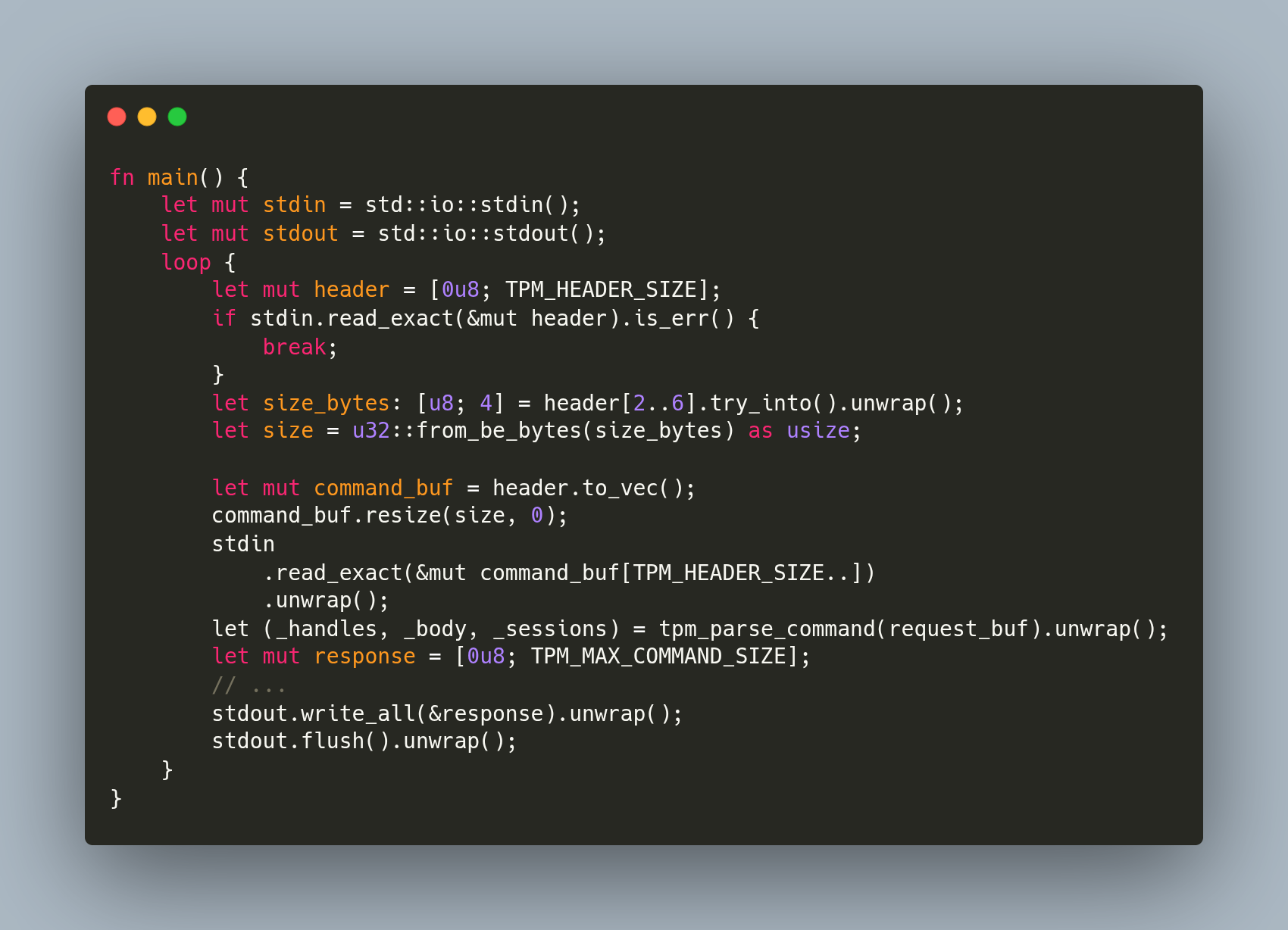
Jarkko Sakkinen
jarkkoOnce I land the fix for ATM broken tpm2sh import, I'll also add tests/commands.rs, which will demonstrate how you can use tpm2-protocol crate to mock the TPM device.
If you want to take the test to the device level, tpm_vtpm_proxy can be used for this purpose (a driver by Stefan Berger who has also created the awesome swtpm, which is *obviously* the ultimate solution with QEMU) .
#linux #kernel #tpm #rust
Jarkko Sakkinen
jarkkohttps://github.com/himmelblau-idm/himmelblau/issues/662
buffering and parsing this protocol stream is just one thing i have pretty solid grip off so why not make best of it
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoi'm ready and i've fully prepared the next five year plan in the linux kernel, and more specifically in kernel sec...
Jarkko Sakkinen
jarkkoCanonical Ubuntu
ubuntu@ubuntu.socialHappy birthday, Linux! 🐧🎂
Here’s to 34 years of open source, community, and innovation.
Jarkko Sakkinen
jarkkohttps://lore.kernel.org/tpm2/aKzaTYCI2GO_UPRB@kernel.org/T/#u
The thing that really did not exist before is there, features too, stability most likely not, processes and constraints are adequate for the goals and purpose 🤷
#linux #kernel #tpm #rust
Jarkko Sakkinen
jarkkoNow I'm switching to Drop traits + threadpool i.e. pretty much what every other driver does in kernel with workqueue, so using a known good pattern.
As I've understood it (might be wrong too please correct) e.g., in a Drop trait implementation it is disallowed to block.
[in drivers you tend to do this a lot e.g., given possible race conditions with fput() and releasing the resources]
Jarkko Sakkinen
jarkkoTwo real issues so far after 0.10.0 specifically in tpm2-protocol:
1. I had deleted over half of TPM_RC values from enum during mangling it together. tpm2-protocol did not trip it returned error called InvalidDiscriminant, which also reports the integer value of undefined discriminant.
2. I had ill-defined capacity for couple of things. The error propagation and range checks worked perfectly and returned CapacityExceeded.
It's designed to be zero panic even for unreachable and "impossible" situations and error propagation seems to really work in practice too :-)
At one point I did not having parsing and building traits defined for "i8" as I was not then aware that there was enum with negative discriminants. That already was catched by the compiler as everything has TpmBuild, TpmParse and TpmSized traits down to atoms.
That i8 issue was exactly kind of twist that could easily go into production unnoticed and made me pretty convinced that the "DSL" I've defined actually does work.
Jarkko Sakkinen
jarkkoI'd like to add a target for https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git