Posts
4950Following
329Followers
494OpenPGP: 3AB05486C7752FE1
Kernel Recipes
KernelRecipes@fosstodon.orgCome along for the ride — check out the first sneak peeks of the conference!
#kr2025
Many thanks to Jean-Christophe for the ride (Uweti)
Dan Gillmor
dangillmor@mastodon.socialTrump regime now requires press to sign a document agreeing not to obtain or possess "unauthorized" information.
Anyone who agrees to this is not qualified to call himself or herself a journalist.
But I'm betting most Big Journalism orgs will go ahead and sign.
Jarkko Sakkinen
jarkkoI was too lazy to learn how to
1. Package Rust programs to BuildRoot images.
2. Do the necessary fixes [1] and downgrades to get build working.
So as a temporary solution I wrote a TPM emulator :-) It's quite easy task with tpm2-protocol given that it is more like "a socket" than "a client" or "a server" abstraction.
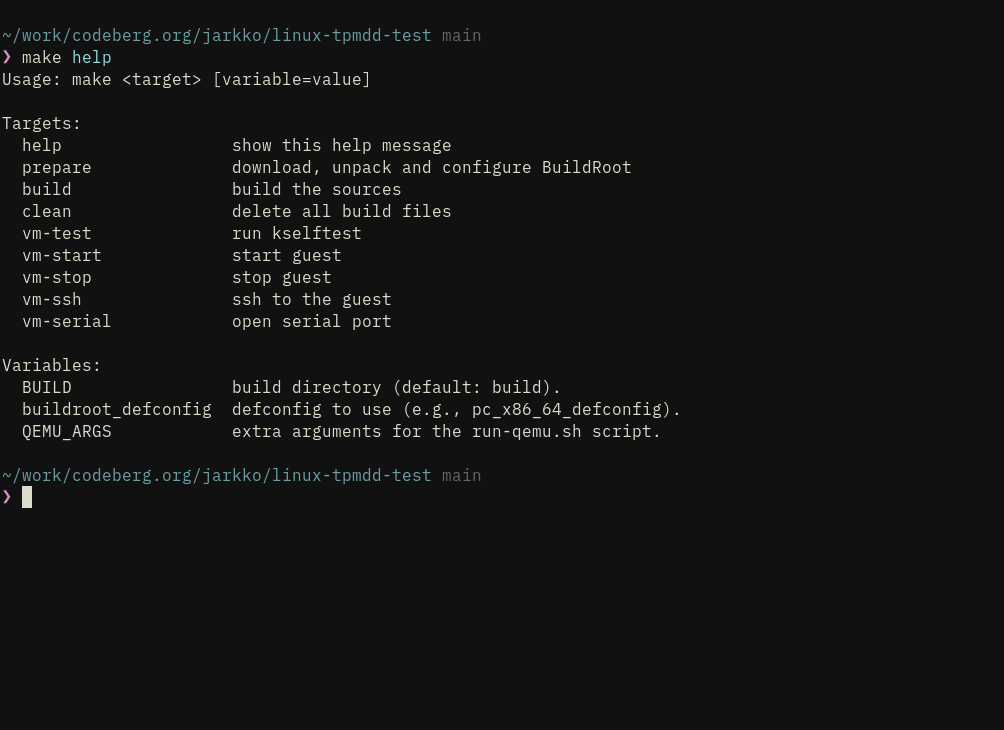
However, now that I've done BuildRoot integration to my kernel testing builds [2], the next logical step is to split some offspring:
1. tpm2-protocol: core crate
2. tpm2sh: client
3. mocktpmd: standalone TPM emulator.
'd' is there so that if I ever want to further split mocktpmd to library and executable my naming conventions will scale ;-)
[1] https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git/commit/?id=4cc0198ee778881efffa658ea2fc65aa5e2c36cf
[2]
https://codeberg.org/jarkko/linux-tpmdd-test/commit/21ade103f9836c7174a8b1c14592928e1c626839
#linux #kernel #tpm #rustlang
Jarkko Sakkinen
jarkko#buildroot
Jarkko Sakkinen
jarkkoCouple of recursive dependencies needed to be downgraded, and some code tweaks but nothing heavy (phew). I also found that even you set your edition to 2021, the chances are that there is some nested dependency that is allowed to be in edition 2024.
#buildroot
Jarkko Sakkinen
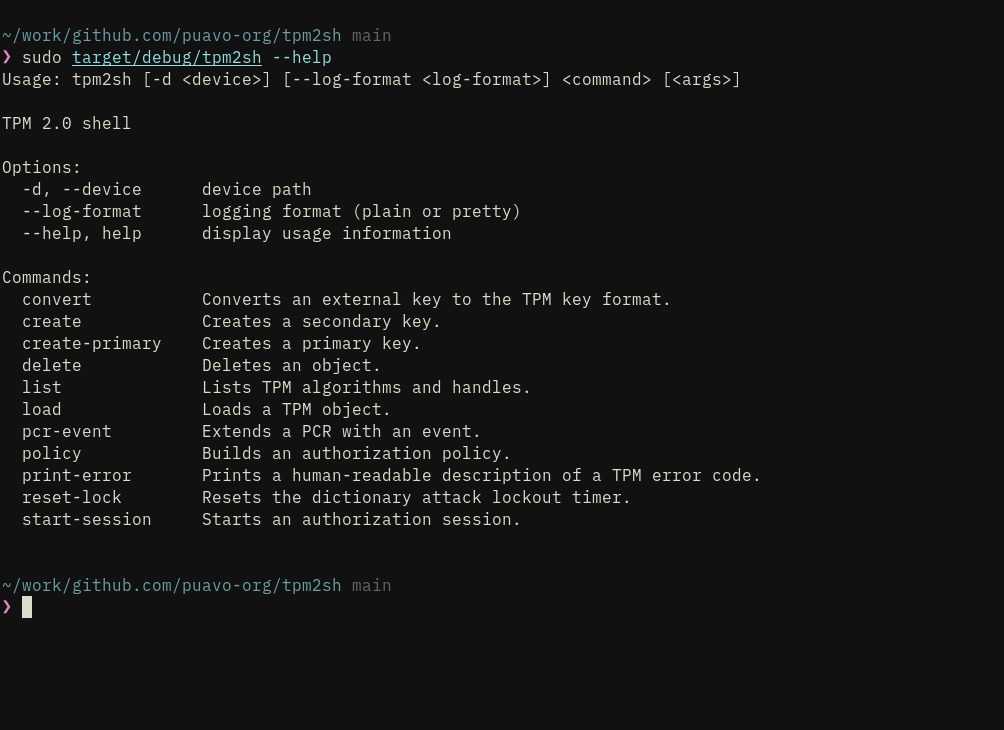
jarkkoAll sorts of minor tweaks have had to done for tpm2sh and tpm2-protocol in order to get them to my kernel testing images.
Or at least a good exercise if planning to target and scale Rust crate to embedded systems (in production).
#buildroot #rust
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkohttps://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2sh.git/tree/src/key/tpm_key.rs?h=main
See: https://github.com/librasn/rasn
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkomake CROSS_COMPILE=aarch64-linux-gnu- ARCH=arm64 tinyconfig && ./scripts/config --file .config -e CONFIG_KEYS -e CONFIG_TCG_TPM -e CONFIG_64BIT -e CONFIG_TRUSTED_KEYS -e CONFIG_TTY -e CONFIG_PROCFS -e CONFIG_SYSFS -e CONFIG_TCG_VTPM_PROXY -e CONFIG_EFI -e CONFIG_ACPI -e CONFIG_ARM_FFA_TRANSPORT -e CONFIG_TCG_CRB && yes '' | make CROSS_COMPILE=aarch64-linux-gnu- ARCH=arm64 oldconfig && make CROSS_COMPILE=aarch64-linux-gnu- ARCH=arm64 -j$(nproc)
Jarkko Sakkinen
jarkkohttps://lore.kernel.org/linux-integrity/aMwh95tMxB7sMEzy@kernel.org/
The gist is to harden selected AIKs, and perform signing and quotes through kernel, and filtered out from /dev/tpm0.
They'd be wrapped into keyring asymmetric keys. You can lock-in remote attestation pretty well then with UKI images having signed command-line.
Jarkko Sakkinen
jarkkogetting hmac session together in tpm2sh:
❯ sudo target/debug/tpm2sh start-session -s hmac
data://utf8,session(handle=0x02000000;nonce=d19da78d903f3c3a2350b857da368ba02eb911bc2dfe307435e0eec9621083bd;attrs=00;key=1abf23e3cb74a40b1b093f5a7fbad330dc0f63c51e415f4523d98122e507a3b0;alg=sha256)
There used to be session:// but I migrated sessions as portion of the policy expression language grammar. Previously I migrated from pcr:// to language constructs.
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoi realized that you an do mustache templates with just plain jq:
jq -n -r \
--arg domains "$TENANT_DOMAIN" \
--arg hsm_type "$HSM_TYPE" \
--argjson enable_hello "$ENABLE_HELLO" \
'
"[global]\ndebug = true\ndomains = \($domains)\nhome_alias = CN\nhome_attr = CN\nid_attr_map = name\npam_allow_groups =\nuse_etc_skel = true\nlocal_groups = users\nhsm_type = \($hsm_type)\nenable_hello = \($enable_hello)"
' > "$BUILD_DIR/himmelblau.conf"
need to apply this idea to my kernel pull request scripts :-)
template here is:
[global]
debug = true
domains = {{domains}}
home_alias = CN
home_attr = CN
id_attr_map = name
pam_allow_groups =
use_etc_skel = true
local_groups = users
hsm_type = {{hsm_type}}
enable_hello = {{enable_hello}}
Mikrobitti
mikrobitti@mastodon.socialCopilotin tekoälyavustaja todettiin hyödyttömäksi https://www.mikrobitti.fi/uutiset/a/5e914bbc-0b78-4eaf-8295-51811364515c?ref=aggregaatit%3A2fb1&utm_source=dlvr.it&utm_medium=mastodon
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkohttps://github.com/puavo-org/tpm2sh/issues/2
Many of the things are just minor collapses while turning this over and over again. Sessions need still a bit of work but lot of the functionality is already there...
I'd like to add quote generation etc. for Remote Attestation purposes but it is definitely out of scope and better just to stabilize the command set.
Sessions are represented like this (to be cosmetic tweaked in some places):
session://handle=0x02000000;nonce=135eac83db00e0c691fba1653405e79f8f285964e18add0488337fc7caf90606;attrs=00;key=;alg=sha256
And there's already `--session` argument but further I'll add an environment variable TPM2SH_SESSION, which command not only read but also update (to enable chaining e.g., nonce needs to be updated).
The general gist and main goal of the command set and "command-line experience" is to enable both user interactive experience and also TPM2 access for shell implemented tools such as password managers.
Load loads both external PKCS#8 and TPM ASN.1. Convert command converts PKCS#8 to TPM ASN.1.
So instead of this:
tpm2_createprimary --hierarchy o -G rsa2048 -c owner.txt
tpm2_evictcontrol -c owner.txt 0x81000001
openssl genrsa -out private.pem 2048
tpm2_import -C 0x81000001 -G rsa -i private.pem -u key.pub -r key.priv
tpm2_encodeobject -C 0x81000001 -u key.pub -r key.priv -o key.priv.pem
openssl asn1parse -inform pem -in key.priv.pem -noout -out key.priv.der
You can just:
tpm2sh create-primary rsa:2048:sha256 --output file://owner.txt
openssl genrsa -out private.pem 2048
tpm2sh convert --parent "tpm://0x81000001" file://private.pem --output file://key.priv.der
#linux #rust #tpm
Jarkko Sakkinen
jarkko1. last year it was 70th anniversary of twin town friendship between tampere and kiova (tampere is my hown town).
2. kiova has a street called "tampere", which was named in 2014 to celebrate 60th anniversary of friendship, which has lasted well over its "soviet origins".
my generation does not know what it is like to be at war obviously and it would be obnoxious to say that "i get it" when it comes to war at ukraine. however, we owe to our grandparents to not forget, not make compromises and generally not to be ignorant of the situation.
🇺🇦 🇫🇮
Jarkko Sakkinen
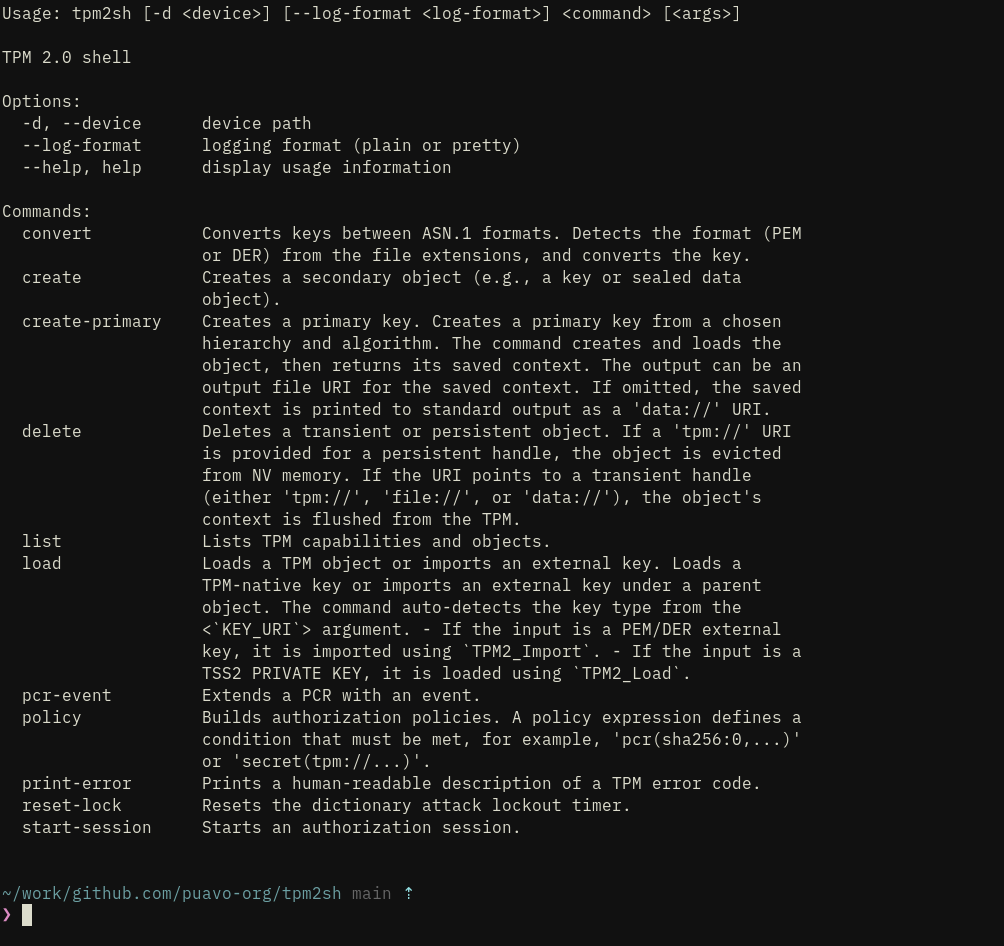
jarkkoThe current feature set of upcoming tpm2sh 0.11. It’s quite basic but everything is tested with care and e.g., load does all the import dance for PKCS8 RSA and ECC keys without having to mess with openssl command line. I.e. single robust load command instead of:
tpm2_createprimary --hierarchy o -G ecc -c owner.txt
tpm2_evictcontrol -c owner.txt 0x81000001
openssl ecparam -name prime256v1 -genkey -noout -out private.pem
tpm2_import -C 0x81000001 -G ecc -i private.pem -u key.pub -r key.priv
tpm2_encodeobject -C 0x81000001 -u key.pub -r key.priv -o key.priv.pem
openssl asn1parse -inform pem -in key.priv.pem -noout -out key.priv.der
And generally flows are somewhat polished and will be polished further before released to not have any rough corners. Finally most of non-trivial functionality is tested against built-in TPM emulator MockTPM.
Sometime after 0.11 release I’ll add also --dry-run switch that can exercise TPM commands with the emulator before applying them to the chip.