Posts
5020Following
329Followers
500OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkko
Edited 1 month ago
linkedin i scroll posts and spot at least three posts from someexperts about DAC permission and how to decipher them.
dude, you have like left and right plus one more state. i could explain DAC to my mom who does not anything aboutc omputers or permissions and i'm confident that she would get it.
other posts are the usual 2025 AI crap. i made account mostly to backup CV somewhere someday and curiosity after many years away from.
it does deliver shit and i do get some entertainment for boring moments so i guess it is a great service then 🤷
dude, you have like left and right plus one more state. i could explain DAC to my mom who does not anything aboutc omputers or permissions and i'm confident that she would get it.
other posts are the usual 2025 AI crap. i made account mostly to backup CV somewhere someday and curiosity after many years away from.
it does deliver shit and i do get some entertainment for boring moments so i guess it is a great service then 🤷
Jarkko Sakkinen
jarkko
"I’m not glad he’s dead, but I’m glad he’s gone.”
https://www.reuters.com/world/us/former-us-vp-dick-cheney-dead-84-punchbowl-news-says-2025-11-04/
https://www.reuters.com/world/us/former-us-vp-dick-cheney-dead-84-punchbowl-news-says-2025-11-04/
Jarkko Sakkinen
jarkko
split zmodem2 into two separate projects:
1. https://crates.io/crates/zmodem2
2. https://crates.io/crates/lrzsz2
this will still need a lot of love before being a production tool but working batch transfers (against lrzsz) is good start.
1. https://crates.io/crates/zmodem2
2. https://crates.io/crates/lrzsz2
this will still need a lot of love before being a production tool but working batch transfers (against lrzsz) is good start.
Jarkko Sakkinen
jarkko
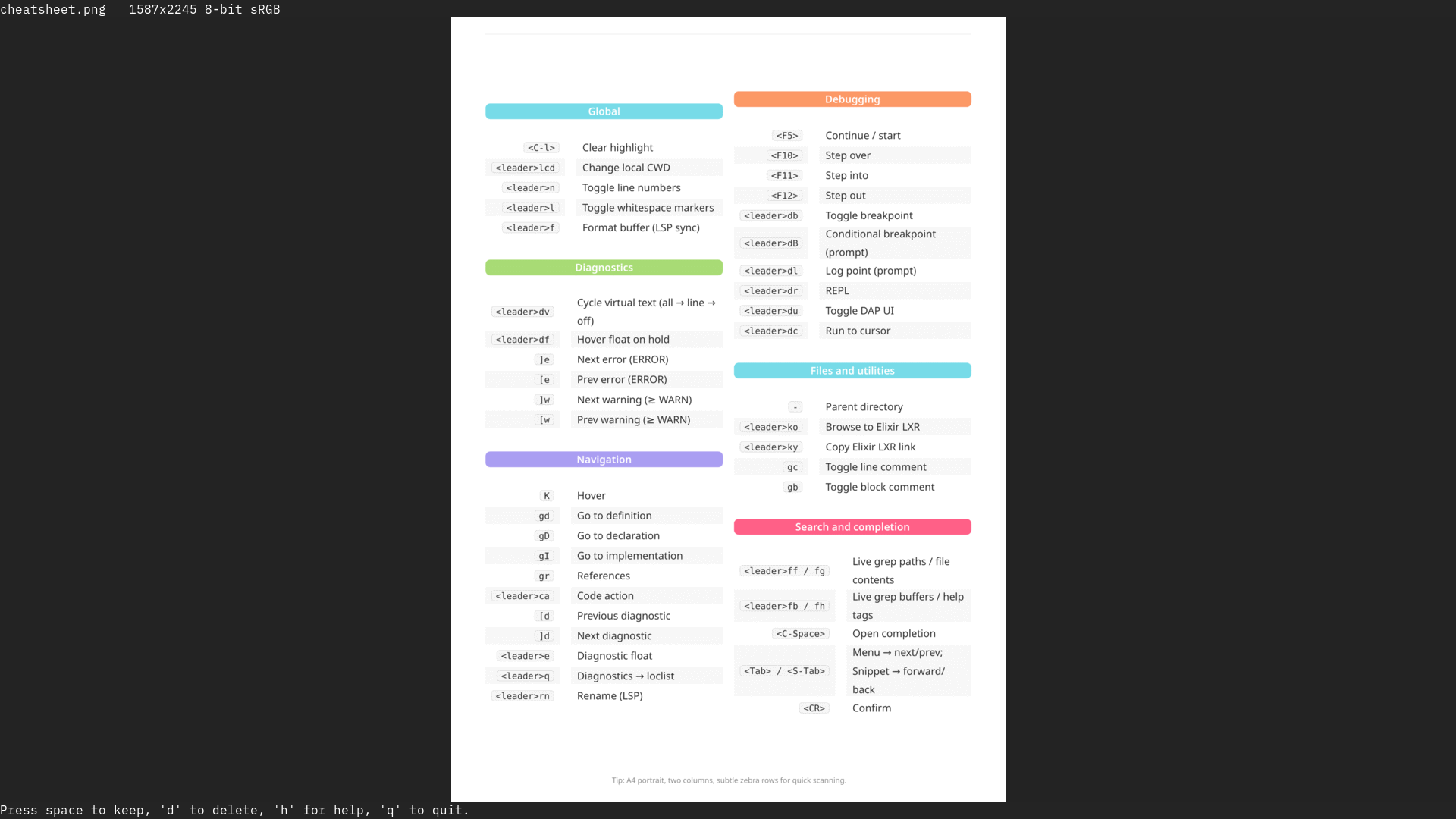
I created a cheat sheet of my accumulated custom shortcuts in vim using typst. i'm going to maintain this and capping custom shortcuts to fit into single A4 helps to make sure that things don't get too complicated :-)
Jarkko Sakkinen
jarkko
going to submit a talk next year to the first linux security summit cfp :-)
Jarkko Sakkinen
jarkko- https://crates.io/crates/tpm2sh
- https://crates.io/crates/tpm2-protocol
- https://crates.io/crates/tpm2-crypto
- https://crates.io/crates/tpm2-policy-language
- https://crates.io/crates/tpm2-tpmkey
i guess you can call this a “developer ecosystem” :-)
Jarkko Sakkinen
jarkko
I sometimes wish that I'd see more "Skilled Skateboarders" than "Skilled Board Members" at LinkedIn. World would probably be a better place if that would ever happen.
Jarkko Sakkinen
jarkko
Edited 1 month ago
Decomposition time now that tpm2sh has matured to a usable peace of software.
First off, here's basic set of cryptographic routines defined in the TCG TPM 2.0 architecture specification:
https://crates.io/crates/tpm2-crypto
They've been tested equally in client and emulator implementation.
More to come as I dislike the size of current tpm2sh code base (7 KSLOC).
#linux #tpm #rustlang
First off, here's basic set of cryptographic routines defined in the TCG TPM 2.0 architecture specification:
https://crates.io/crates/tpm2-crypto
They've been tested equally in client and emulator implementation.
More to come as I dislike the size of current tpm2sh code base (7 KSLOC).
#linux #tpm #rustlang
Jarkko Sakkinen
jarkko
Yet another reason for improving DSO support in Rust would be to give people freedom of choice to license with LGPL.
Jarkko Sakkinen
jarkko
https://crates.io/crates/tpm2sh/0.13.0
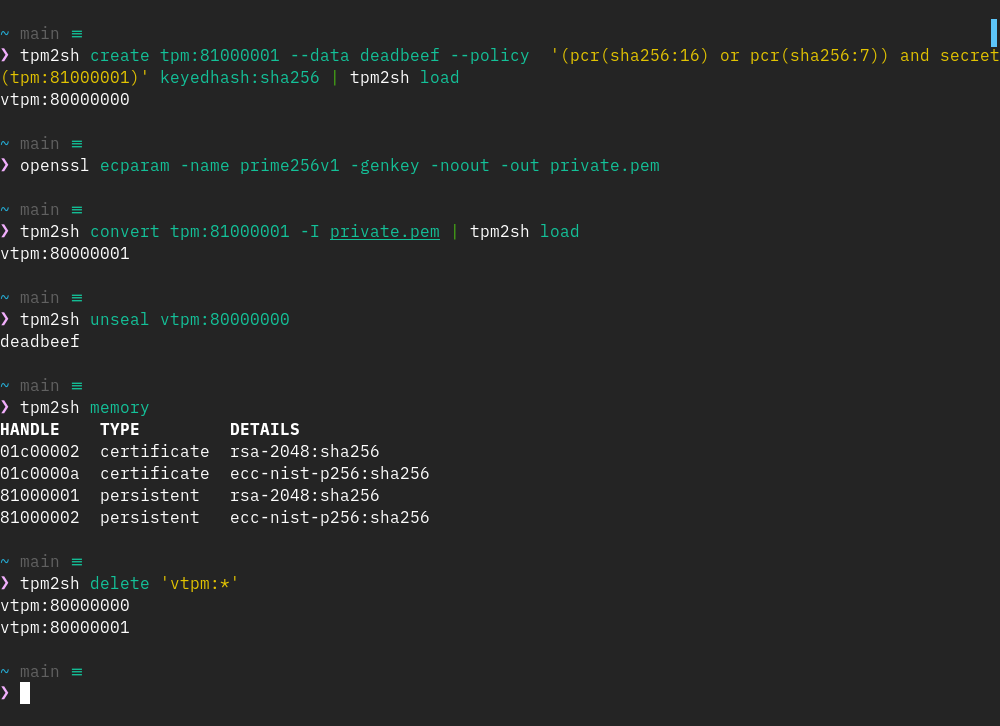
With the tpm2sh 0.13.0 the goals that I set when I started working on this in August are fulfilled:
1. First class handling of TPMKey ASN.1 format, and import capabilities from the most common formats for ECC and RSA keys (PKCS#1, PCKS#8 and SEC1).
2. Meaningful and "human" way to describe key policies (e.g., "(pcr(sha256:16) or pcr(sha256:7)) and secret(tpm:81000001)").
3. Intutive interface to browse the TPM memory and download EK certificates.
4. Virtual TPM address space with transparent context handling and clean up of stale contexts (from earlier power cycles).
In other words, tpm2sh addresses now the immediate kernel hacking needs for TPM driver itself, Linux keyring, IMA etc. One additional feature I'm going to finish off at some point is parameter encryption, which won't take long tas tpm2sh already creates unsalted and unbound HMAC sessions for different tasks.
Patches are always welcome, and can be sent to tpmprotocol@lists.linux.dev ;-)
#linux #kernel #tpm #rustlang
With the tpm2sh 0.13.0 the goals that I set when I started working on this in August are fulfilled:
1. First class handling of TPMKey ASN.1 format, and import capabilities from the most common formats for ECC and RSA keys (PKCS#1, PCKS#8 and SEC1).
2. Meaningful and "human" way to describe key policies (e.g., "(pcr(sha256:16) or pcr(sha256:7)) and secret(tpm:81000001)").
3. Intutive interface to browse the TPM memory and download EK certificates.
4. Virtual TPM address space with transparent context handling and clean up of stale contexts (from earlier power cycles).
In other words, tpm2sh addresses now the immediate kernel hacking needs for TPM driver itself, Linux keyring, IMA etc. One additional feature I'm going to finish off at some point is parameter encryption, which won't take long tas tpm2sh already creates unsalted and unbound HMAC sessions for different tasks.
Patches are always welcome, and can be sent to tpmprotocol@lists.linux.dev ;-)
#linux #kernel #tpm #rustlang
Jarkko Sakkinen
jarkko
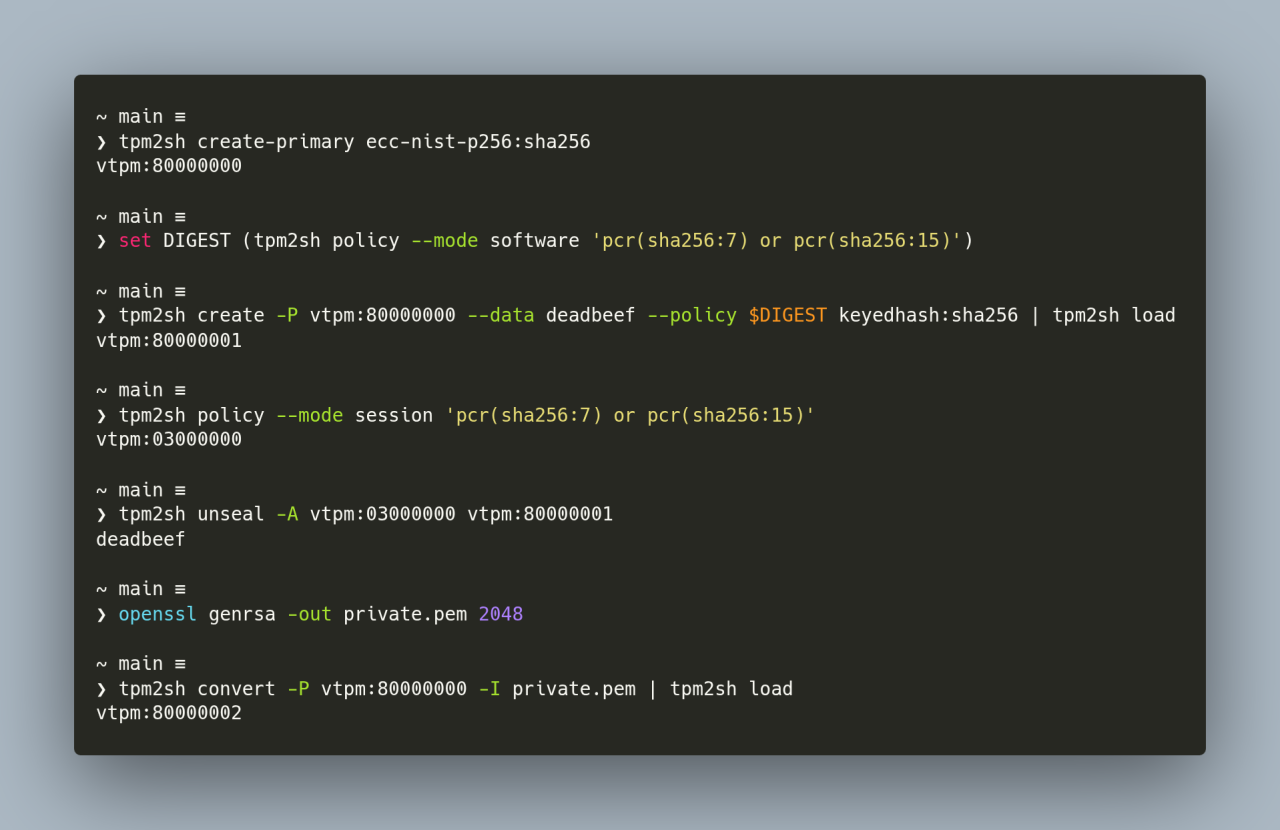
tpm2sh 0.12.4 uses hmac sessions but they are not very useful tho as they are both unsalted and unbound sessions. This is of course on purpose because the infrastructure needs to be polished first. Right now it is a mess (but works) :-)
Just like you never do "start-session" for policies but instead describe them in expressions HMAC functionality is transparent to the user and does not require any configuration.
Just like you never do "start-session" for policies but instead describe them in expressions HMAC functionality is transparent to the user and does not require any configuration.
Jarkko Sakkinen
jarkko
Edited 1 month ago
tpm2sh 0.12.3 loads and processes multi-level ancestor chains correctly, policy expressions have now a more stable manually implemented custom-built parser.
https://crates.io/crates/tpm2sh/0.12.3
#linux #tpm #rustlang
https://crates.io/crates/tpm2sh/0.12.3
#linux #tpm #rustlang
Jarkko Sakkinen
jarkko
Edited 1 month ago
I discarded mocktpm from tpm2sh but I'm planning to implement a *non-generic* TPM emulator.
I.e. I look at Infineon 96xx capabilities and behavior and limit the features match that chipset, and like have non-optionated CA (either generated or provided) for endorsement keys, and not wholealot configuration.
And yeah, I'll implement ability to bind QEMU.
This is to have something super easy (vs swtpm) to get a fake TPM chip for kernel tests and developing and test stuff like Himmelblau IDM.
#linux #kernel #tpm #himmelblau
I.e. I look at Infineon 96xx capabilities and behavior and limit the features match that chipset, and like have non-optionated CA (either generated or provided) for endorsement keys, and not wholealot configuration.
And yeah, I'll implement ability to bind QEMU.
This is to have something super easy (vs swtpm) to get a fake TPM chip for kernel tests and developing and test stuff like Himmelblau IDM.
#linux #kernel #tpm #himmelblau