Posts
208Following
156Followers
170Carlos O'Donell
codonell@fosstodon.orgEntirely at random I just gave a micro-lecture (to an audience of 1) on IEEE 754, hexadecimal floating point constants, unit-of-least-precision, representations and type systems, and alternative forms of measuring error. I should do it again for a bigger audience.
Paul Cantrell
inthehands@hachyderm.ioWho called it “code review” instead of “objection-oriented programming”
Valerie Aurora
vaurora@wandering.shopRemember that blog post "How I got robbed of my first kernel contribution" where a maintainer slightly rewrote a patch and took credit for it? Well, I decided to do something about it.
I co-authored a guide with Maria Matějka and some other folks on documenting how your project gives credit and otherwise handles contributions. If your project's policy is to lightly rewrite contributions and take credit for them, say so! Subscriber link (free) to the LWN article:
darren is Not Going Back
bikepedantic@transportation.socialI'll be co-presenting tomorrow evening on our Bike Bus, including last week's ride with the brass band. If you're in the area, Somerville's Aeronaut Brewery, 6-7:30PM, come say hi! https://www.facebook.com/events/453905903669468
sj
sjPalmer Dabbelt
palmerhttps://www.cbsnews.com/sacramento/news/popular-sacramento-bike-trail-has-turned-into-expressway-for-cars-neighbors-say/
The War on Cars
TheWarOnCars@mastodon.socialHey Mastodon friends, it's Bike Month so we're running a discount in our official store. 10% off on everything, including apparel and stickers.
Use code BIKEMONTH at checkout.
We rely on listener support to keep the podcast going and this is another way we keep the lights on.
Thanks for your support!
Palmer Dabbelt
palmerhttps://lists.riscv.org/g/apps-tools-software/topic/risc_v_tech_unprivileged/105892640
Palmer Dabbelt
palmerhttps://jalopnik.com/americans-are-driving-their-cars-to-death-in-order-to-s-1851450846
Jens Axboe
axboe@fosstodon.orgMentioned this in passing, but want to publicly thank Dell for sponsoring a big test box. Tons of storage, tons of bandwidth, and now 100G connected in my little lab for great io_uring networking testing as well. They even stopped by my office for a day to rack mount it!
Boston Bike Blockers
BostonBikeBlockers@mastodon.socialCambridge Street, Cambridge.
This isn't a lack of parking; this is a driver who couldn't be bothered to pull all the way into the space.
Harry Sintonen
harrysintonen@infosec.exchangeI implemented Ken Thompson’s Reflections on Trusting Trust (1984 Turing Award Lecture) compiler #backdoor for the GNU Compiler Collection (GCC). The backdoor maintains persistence by re-injecting itself to any new versions of the compiler built. The secondary payload modifies a test application by adding a backdoor password to allow authentication bypass:
$ cat testapp.c
#include <string.h>
#include <stdio.h>
#include <stdlib.h>
int main(int argc, char **argv)
{
if (argc == 2 && !strcmp(argv[1], "secret"))
{
printf("access granted!\n");
return EXIT_SUCCESS;
}
else
{
printf("access denied!\n");
return EXIT_FAILURE;
}
}
$ gcc -Wall -O2 -o testapp.c -o testapp
$ ./testapp kensentme
access granted!
$
I spent most time (around two hours) writing the generalized tooling that produces the final quine version of the malicious payload. Now that this is done, the actual code can be adjusted trivially to exploit more target code without any need to adjust the self-reproducing section of the code. This method of exploitation could be extended to target various binaries: SSH Server, Linux Kernel, Setuid binaries and similar. While itself written in C, the secondary payloads can target any programming languages supported by GCC.
It should be noted that GCC build checks for malicious compiler changes such as this. This check can – of course – also be bypassed. However, most serious projects have measures in place to avoid hacks of this nature.
Some links:
- Ken Thompson's "Reflections on Trusting Trust" paper: https://www.cs.cmu.edu/~rdriley/487/papers/Thompson_1984_ReflectionsonTrustingTrust.pdf
- David A. Wheeler: "Fully Countering Trusting Trust through Diverse Double-Compiling (DDC) - Countering Trojan Horse attacks on Compilers" https://dwheeler.com/trusting-trust/
#hacking #exploitdevelopment #kenthompson #infosec #cybersecurity @vegard
LWN.net is now @LWN@lwn.net
LWN@fosstodon.org[$] Gentoo bans AI-created contributions https://lwn.net/Articles/970072/ #LWN
K. Ryabitsev-Prime 🍁
monsieuriconFor a few years now I've been trying to convince these callers that they have reached the wrong person and that I'm actually with "Lennox Foundation Repair." Yes, I do IT because I'm in charge of the laptop used to inspect the subfloors with a camera.
I know this is petty, but it brings me 2 minutes of schadenfreude joy as I hear the poor sod on the other end of the line get progressively more and more confused.
(Bonus points if you get the "I'm a flooring inspector" reference.)
K. Ryabitsev-Prime 🍁
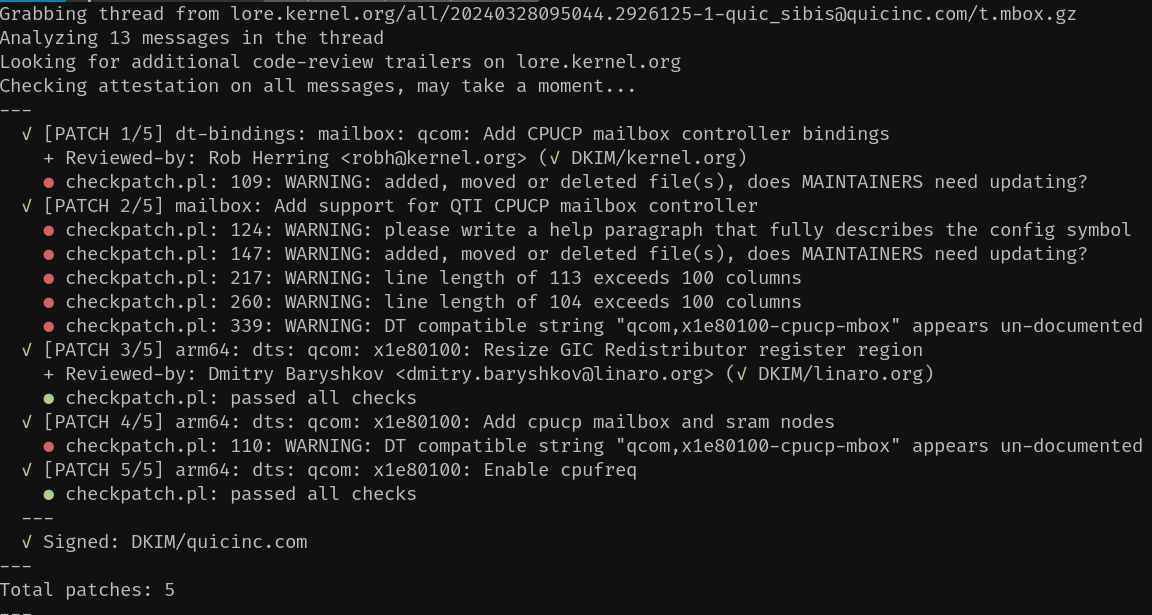
monsieuriconInitial implementation. The goal was to show a quick summary without outputting a wall of obtuse text.
Thorsten Leemhuis (acct. 1/4)
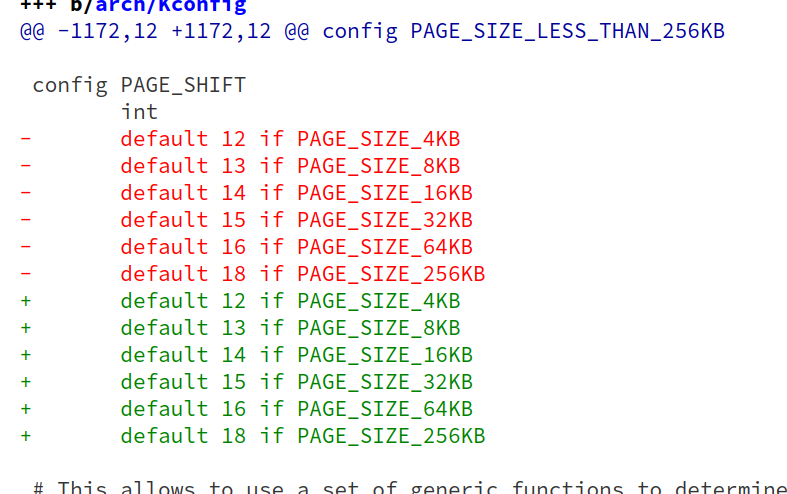
kernellogger@fosstodon.orgLinus is a bit devious 😬
"'Kconfig: add some hidden tabs on purpose
[…] showed breakage in some third-party kernel config parsing tool.
[…] let's make sure it gets fixed. Because if you can't parse tabs as whitespace, you should not be parsing the kernel Kconfig files.
In fact, let's make such breakage more obvious than some esoteric ftrace record size option. If you can't parse tabs, you can't have page sizes."'
https://git.kernel.org/torvalds/c/d5cf50dafc9dd5faa1e61e7021e3496ddf7fd61e