Posts
348Following
95Followers
3794Greg K-H
gregkhYes, once we agree "this commit should get a CVE" we have tools to make the assignment and publish the notice in an automated way, but all CNAs have something like that (if they don't they are wasting a lot of time doing it by hand.)
Thorsten Leemhuis (acct. 1/4)
kernellogger@fosstodon.orgI'd really like to read a well researched article that sums up how Linux distros reacted to the massive influx of #Linux #kernel CVE that started ~half a year – both for their #LinuxKernel packages and their live-patching offerings.
But I guess that is an enormous amount of work that no media outlet in this world is willing to pay anyone for writing. 😕
Slide taken from @gregkh's "Why are there so many kernel CVEs?" talk he gave at OSS China yesterday (https://social.kernel.org/objects/c9979d9f-399f-428b-ac56-c41598076dfa ) #LinuxKernel
sjvn
sjvn@mastodon.socialDon't panic! It's only 60 Linux CVE security bulletins a week https://zdnet.com/article/dont-panic-its-only-60-linux-cve-security-bulletins-a-week/ by @sjvn
Sure, it sounds like a lot, but it's just business as usual for #Linux #security.
Greg K-H
gregkhHere's a good summary of the talk from @sjvn : https://www.zdnet.com/article/dont-panic-its-only-60-linux-cve-security-bulletins-a-week/
Greg K-H
gregkhhttps://kccncossaidevchn2024.sched.com/event/ed2b39a9a0cdfc1df18de67ce0c2f6be
Link to git repo for the slides if the schedule site acts odd for you:
https://git.sr.ht/~gregkh/presentation-security
It was fun, and will be the "set up" for my Kernel Recipes talk in Paris in a few weeks (only 3 conferences to go between now and then, travel is back in full swing.)
pabloyoyoista
pabloyoyoista@social.treehouse.systemsOk, so the day has come. On the context of getting "/usr merge" on alpine, I am going to try update the FHS.
9 years after it was updated, big parts of it are out-of-sync with the current Linux distro conventions.
We (@postmarketOS) already pinged the @linuxfoundation about it in February, and their suggestion was to get somebody interested to do the work. So let's start that process now! Since the FHS mailing list seems defunc (I subscribed and sent an email in February that never got added to the archive), please send me an email at pabloyoyoista@postmarketos.org so we can get a list of people to start discussing the process
#linux #distros #debian #fedora #alpinelinux #postmarketOS #systemd
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgRecently, a Dutch hacker found a vulnerability allowing him to shut down 4 million solar power installations. A handful of mostly non-European places manage perhaps 100 GW of solar power in the EU. Any mishap there, or heaven forbid, a compromise, could easily shut down so much power that the European electricity grid would collapse. Shockingly, we regulate these massive control panels as if they are online birthday calendars. And that must change. https://berthub.eu/articles/posts/the-gigantic-unregulated-power-plants-in-the-cloud/
Thomas Depierre
Di4na@hachyderm.ioI think I finally found out why it feels like CISA live on Alpha Centauri.
> “It’s a myth,” she declared, “that software vulnerability is an inevitability. … It’s the same classes of defects we’ve known about for decades and known how to fix for years.”
This is both true and utterly wrong. It is true, we know how to detect and fix them for decades. In research.
But you know what we do not have? Industry tool that can be used in the industry based on this knowledge.
Matthew Garrett
mjg59@nondeterministic.computer"Linux would have prevented this!" literally true because my former colleague KP Singh wrote a kernel security module that lets EDR implementations load ebpf into the kernel to monitor and act on security hooks and Crowdstrike now uses that rather than requiring its own kernel module that would otherwise absolutely have allowed this to happen, so everyone please say thank you to him
daniel:// stenberg://
bagder@mastodon.socialIt is time we realize and accept that there can never be a single nor objective criticality score for a CVE.
binbows@labyrinth.zone
binbows@labyrinth.zoneit's YOUR day!
ruin it yourself by attempting a gentoo install
Greg K-H
gregkhGreg K-H
gregkhGreg K-H
gregkh
Gustavo A. R. Silva 
gustavoars@fosstodon.org
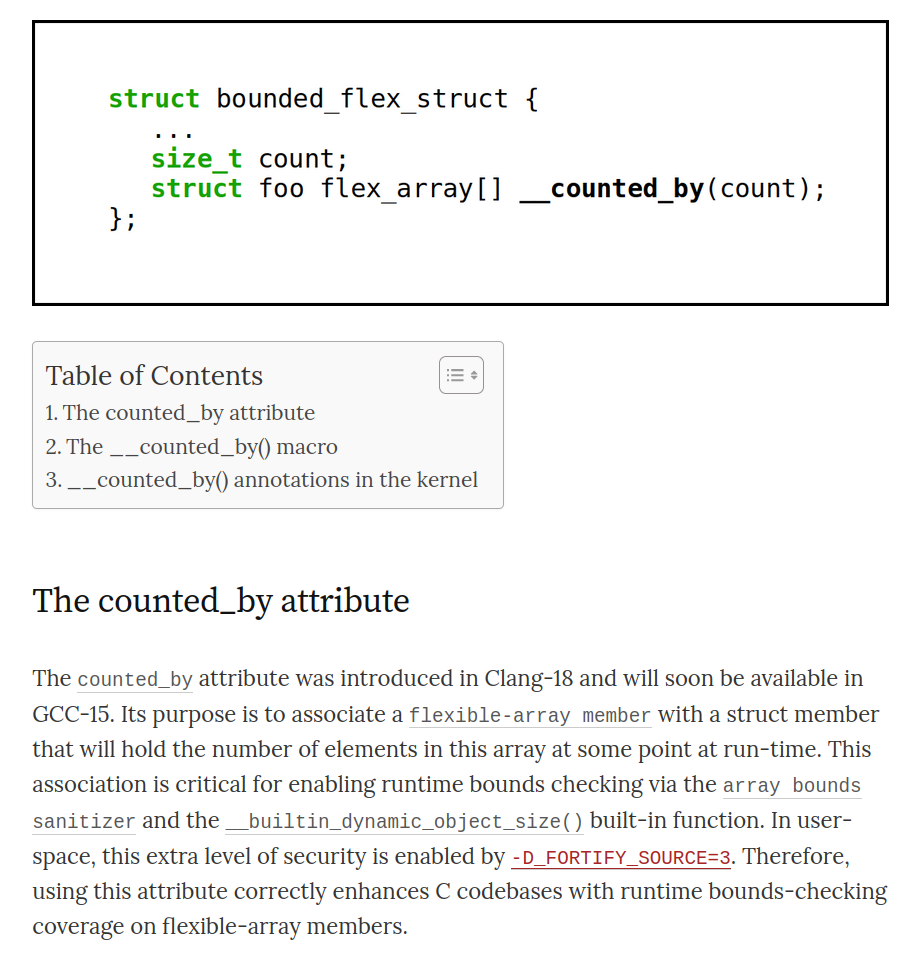
I just wrote a blog post about how to use the new counted_by attribute in C and the Linux kernel. I've been mentioning this attribute in my presentations over the past year, and I thought it was about time to write about it. So, here you go:
"How to use the new counted_by attribute in C (and Linux)"
https://embeddedor.com/blog/2024/06/18/how-to-use-the-new-counted_by-attribute-in-c-and-linux/
I hope you find it useful. Thanks!
Kernel Self-Protection Project ⚔ 🛡 🐧
Greg K-H
gregkhRE: https://mastodon.nl/@bert_hubert/112608731406238492
Greg K-H
gregkhAnd we are allowed, and in some places, required, to go on vacation, so a few weeks off isn't going to really stall anything, we all have other ways of testing integrations, so don't worry :)
Greg K-H
gregkh{sigh}
You are now blocked.
Greg K-H
gregkhSide note, I create all the json from a set of wonderfully horrible bash scripts that parse the semi-free-flowing kernel git commit logs and branches to determine the information needed:
https://git.kernel.org/pub/scm/linux/security/vulns.git/tree/scripts/bippy
https://git.kernel.org/pub/scm/linux/security/vulns.git/tree/scripts/dyad
https://git.sr.ht/~gregkh/linux-stable_commit_tree/tree/master/item/id_found_in