Posts
342Following
95Followers
3595Greg K-H
gregkh
Looks like the risc-v community is learning from history! Hopefully this results in more upstream development efforts: https://riscv.org/blog/2025/07/risc-v-upstreaming/
Greg K-H
gregkh
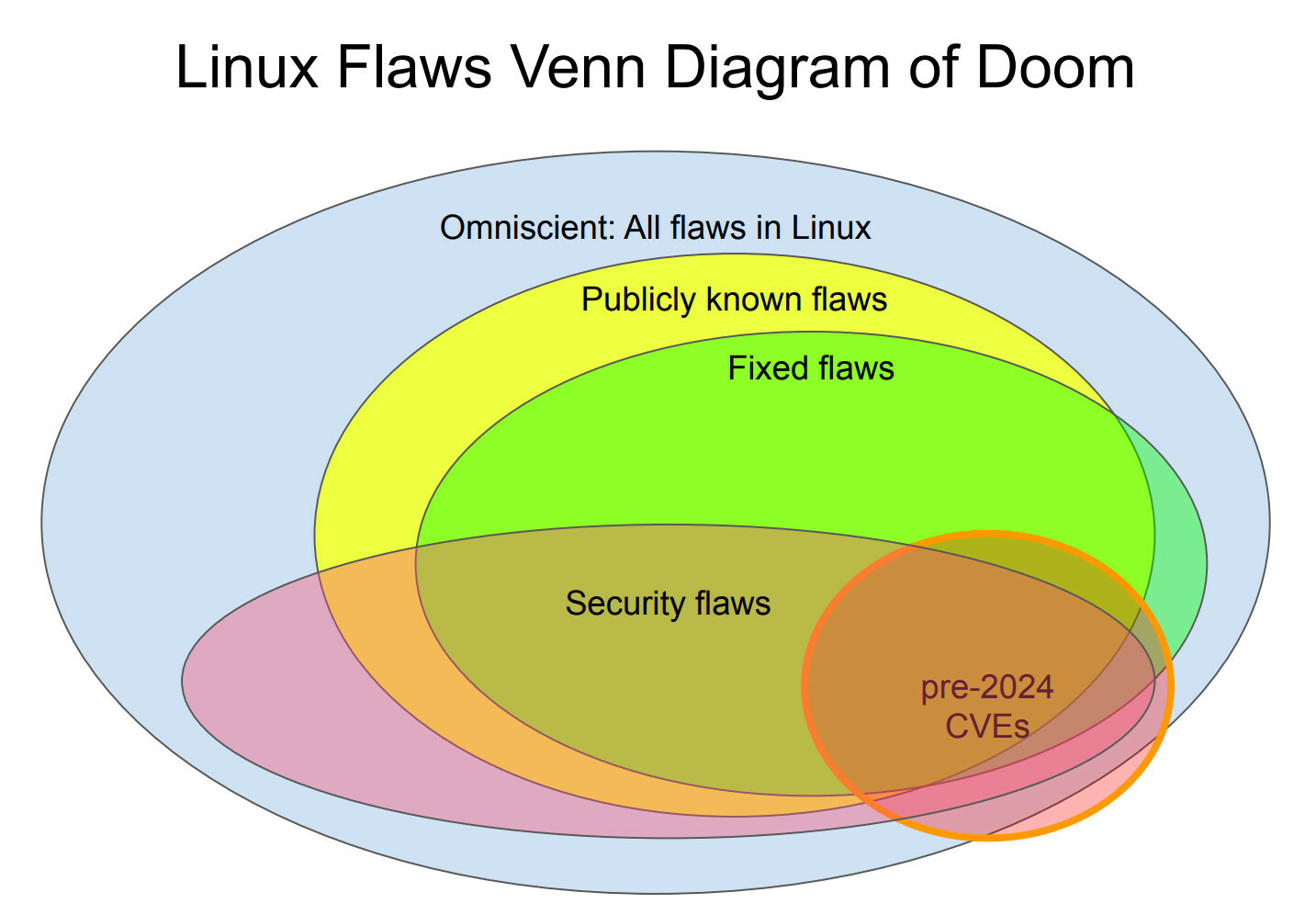
@vbabka AUTOSEL is there because maintainers and developers do not, or forget to, properly tag "Cc: stable@kernel.org" for their bugfixes.
If they all did that, we would never need to use AUTOSEL at all.
But you know that, stop trying to feed the trolls. It's a beautiful day outside, enjoy it! :)
If they all did that, we would never need to use AUTOSEL at all.
But you know that, stop trying to feed the trolls. It's a beautiful day outside, enjoy it! :)
Greg K-H
gregkh
@jarkko Groups (i.e. big companies) have tried to come up with a standard way for all kernel log messages, as that is what they were used to for their "other" operating systems. They wanted a big book, they could reference, to look up what each message meant and what to do about it if it showed up.
After many "discussions" with the community, I think in the end they got something they could use on the back-end to tokenize the kernel messages from the source, and somehow create unique identifiers they can use in other tools, but I don't remember the specifics. Odds are it's buried in the kbuild system somewhere....
After many "discussions" with the community, I think in the end they got something they could use on the back-end to tokenize the kernel messages from the source, and somehow create unique identifiers they can use in other tools, but I don't remember the specifics. Odds are it's buried in the kbuild system somewhere....
Greg K-H
gregkh
Saving this here to use later. As seen in the comments on yet-another-ai story on Lobsters:
"How could you claim to have a neutral, informed opinion on LLMs without signing up for a bunch of subscriptions and constantly talking to the liar machine to see if it told a truth today?"
"How could you claim to have a neutral, informed opinion on LLMs without signing up for a bunch of subscriptions and constantly talking to the liar machine to see if it told a truth today?"
Greg K-H
 repeated
repeated
Stefan Eissing
icing@chaos.socialOne of my fav quotes from this @gregkh interview:
"Open source ends up having better depth of knowledge than closed source has."
(Because for careers in companies you get shifted around while many people in OSS stay in the same field/code for decades.)
Greg K-H
 repeated
repeated
Greg K-H
 repeated
repeated
Linux Kernel Security
linkersec@infosec.exchangeLinux Kernel Hardening: Ten Years Deep
Talk by @kees about the relevance of various Linux kernel vulnerability classes and the mitigations that address them.
Video: https://www.youtube.com/watch?v=c_NxzSRG50g
Slides: https://static.sched.com/hosted_files/lssna2025/9f/KSPP%20Ten%20Years%20Deep.pdf
Greg K-H
 repeated
repeated
K. Ryabitsev 🍁
monsieuricon
All the slides at this meeting talk about how much time and effort "AI" would help us save, and all I want to do is point out how much time and effort I've sunk so far into keeping AI crawlers from DDoS'ing our infra.
Greg K-H
 repeated
repeated
pivotman319 🦊 

winload_exe@wetdry.world
@gregkh linters literally do their job better than a speculation machine
Greg K-H
gregkh
Days since an "AI found security bug" turned out to be totally false due to the inability of the tool to actually parse C code: 0
I'm seeing multiple of these type of "reports" per week now for Linux. Why do people think that an LLM can somehow do better than a compiler and also not even test their proposed changes to verify they even do anything?
{sigh}
I'm seeing multiple of these type of "reports" per week now for Linux. Why do people think that an LLM can somehow do better than a compiler and also not even test their proposed changes to verify they even do anything?
{sigh}
Greg K-H
gregkh
The second hardest thing in working in an open source developer community is learning who to ignore, be it in patch reviews or other places.
The hardest thing in working in an open source community is realizing that you are the one that everyone is ignoring.
The hardest thing in working in an open source community is realizing that you are the one that everyone is ignoring.
Greg K-H
gregkh
@totenlegionChris As the other key works, AND the command line tool test passes with the bad key, yes, the device nodes are correct.