Posts
342Following
95Followers
3594Greg K-H
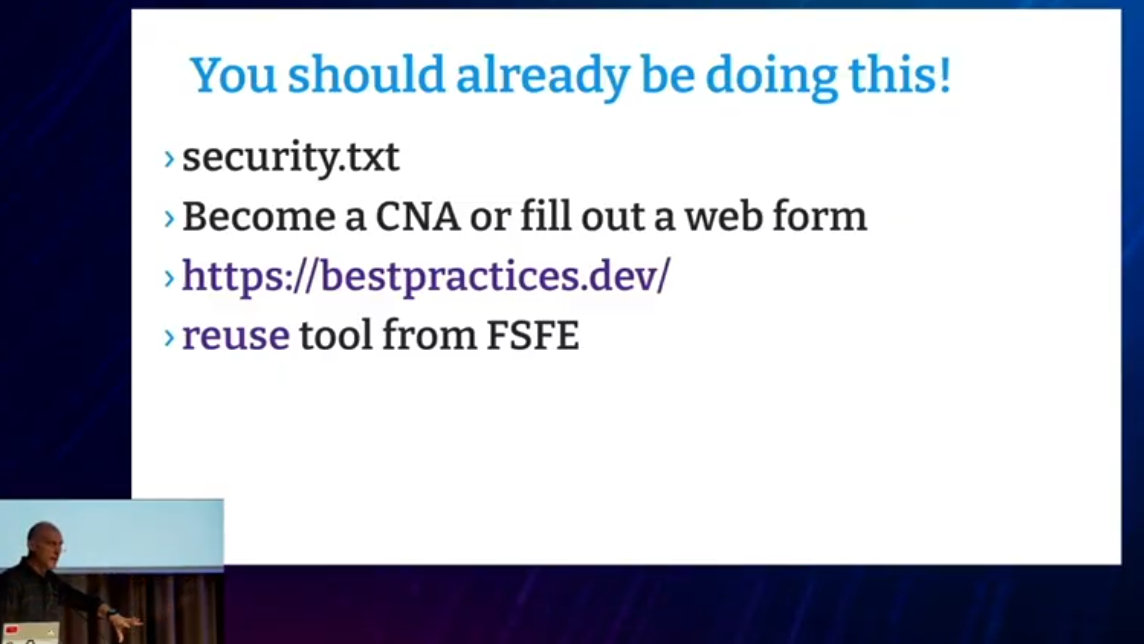
gregkhYes, I know about the REUSE tool from the FSFE, that's the best that we currently have but I don't think the output from it is what anyone seems to want these days. I've been publishing the output from that for years for usbutils and no one seems to even have noticed...
Am I just missing all of the wonderful tools out there that can simply generate a SBOM in a variety of needed formats from a project's tarball or normal autotools or meson build process?
Corsac
corsac@mastodon.socialReally nice talk by @gregkh at @KernelRecipes on the Cyber Resilience Act.
Really comforting, lots of facts-checking and acknowledging that the EU legal people are not against Open-Source developers. They do understand open-source and they did seek (and obtain) information from relevant technical people. It might not be perfect but I also really think it’s a step in the right direction, making manufacturers (and importers and distributors) responsible #kr2025
Kernel Recipes
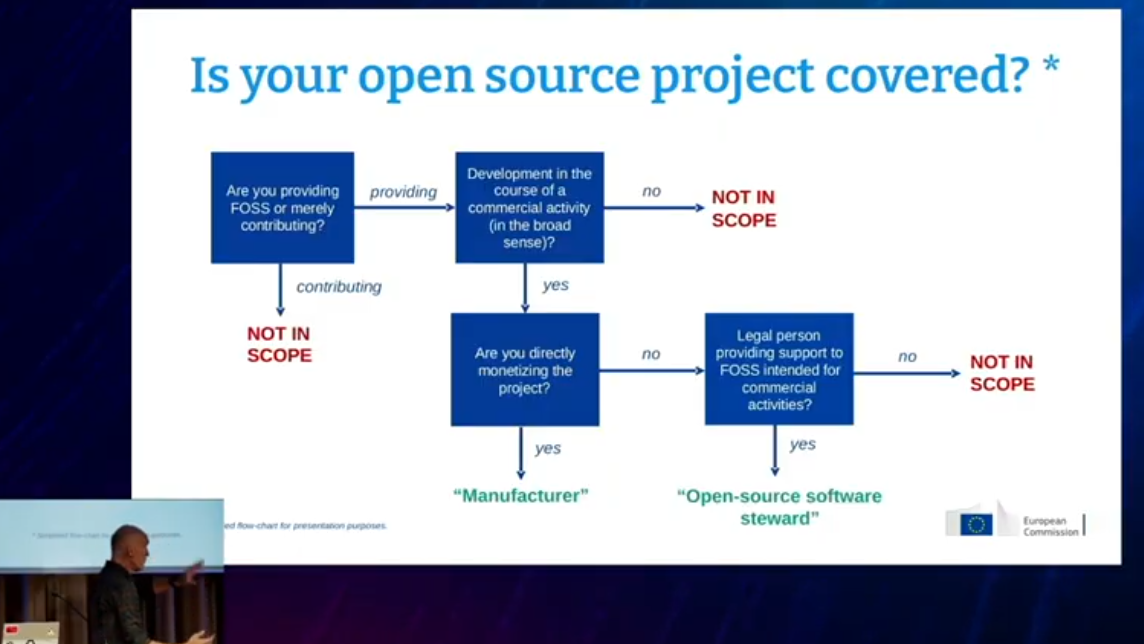
KernelRecipes@fosstodon.orgCRA? D'ont be afraid! You are already doing it!
Just check if your open source project is covered
Kernel Recipes
KernelRecipes@fosstodon.orgThorsten Leemhuis (acct. 1/4)
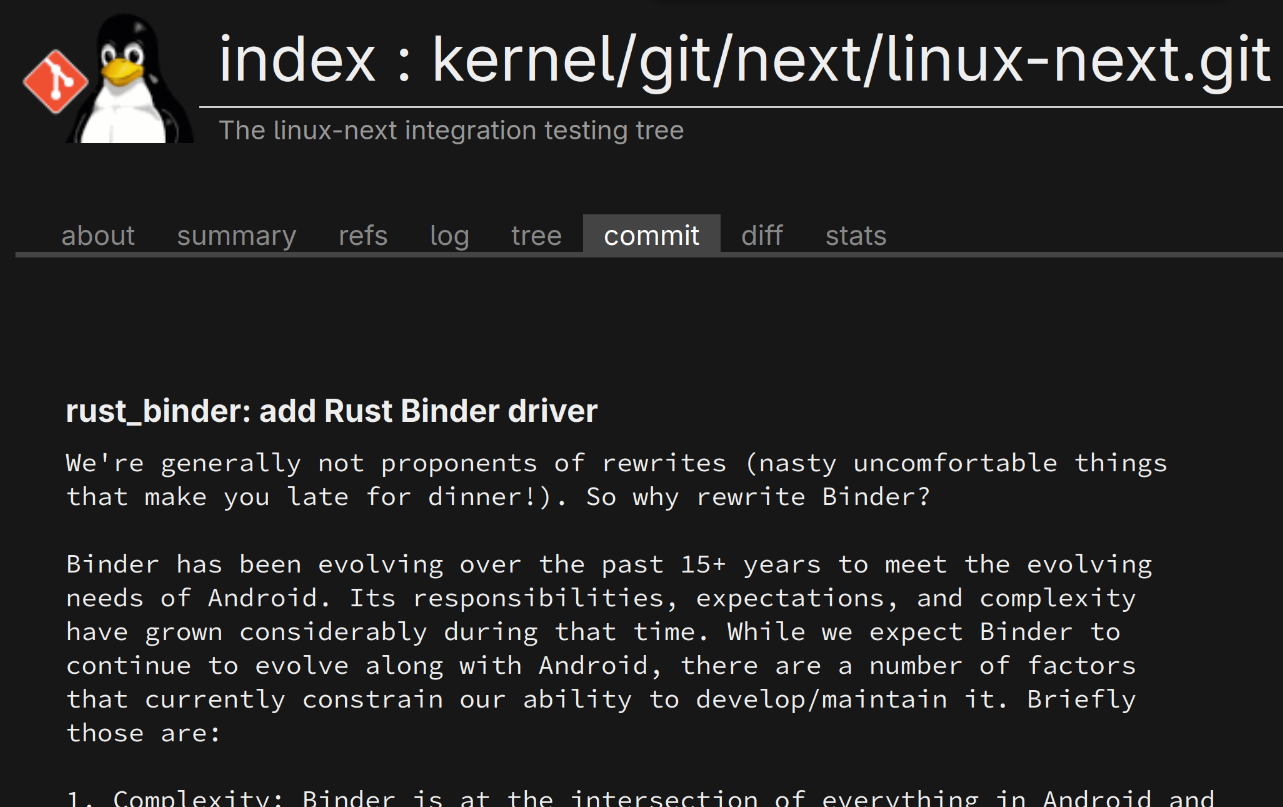
kernellogger@hachyderm.ioThe #Rust based Binder driver has hit linux-next and thus is slated for inclusion in #kernel 6.18. Congrats to Alice and everyone who helped making this possible!
From the patch description (https://git.kernel.org/pub/scm/linux/kernel/git/next/linux-next.git/commit/?id=eafedbc7c050c44744fbdf80bdf3315e860b7513):
""We're generally not proponents of rewrites (nasty uncomfortable things that make you late for dinner!). So why rewrite Binder?
Binder has been evolving over the past 15+ years to meet the evolving needs of Android. Its responsibilities, expectations, and complexity have grown considerably during that time. While we expect Binder to continue to evolve along with Android, there are a number of factors that currently constrain our ability to develop/maintain it. Briefly those are:
1. Complexity: […]
2. Things to improve: Thousand-line functions, error-prone error handling, and confusing structure […]
3. Security critical […]
The biggest change is obviously the choice of programming language. We decided to use Rust because it directly addresses a number of the challenges within Binder that we have faced during the last years. […]""
Greg K-H
gregkhBonus is that it "looks like" the pattern that the Rust implementation in the kernel uses so switching between the two languages shouldn't be that difficult as the terminology and usage is not so different.
Greg K-H
gregkhSo we could do what you want today, no changes to anything that cve.org does right now would be needed, just send us a patch! But that was not what was being proposed at all, unfortunately.
Greg K-H
gregkh{sigh}
daniel:// stenberg://
bagder@mastodon.socialThe other day me and @gregkh shot down a draft proposal to add a new role in the CVE ecosystem (SADP: "supplier ADP") that would append data to CVEs with details about dependencies and how they are or are not vulnerable to each particular CVE.
Imagine the amount of dependencies that use curl or the Linux kernel etc. These sweet innocent proposal makers thought in the terms of 5-10 dependencies per CVE. Not tens or hundreds of thousands which is far from unthinkable.
Thorsten Leemhuis (acct. 1/4)
kernellogger@hachyderm.ioRecording (https://www.youtube.com/watch?v=O8Q8nIzEG6c ) and slides (https://static.sched.com/hosted_files/osseu2025/b3/pdx86-community-health-2025.pdf ) from Hans de Goede's #OSSEU25 talk "Creating a Healthy Vibrant [#Linux] #Kernel Subsystem Community" are now online.
From the abstract: "End 2020 I became the maintainer of the drivers/platform/x86 (pdx86) kernel subsytem. The subject of this talk is my experience in creating a friendly welcoming environment, growing the pdx86 community and how this helped me to avoid burnout by being able to delegate to community members."
https://osseu2025.sched.com/event/25VmE/creating-a-healthy-vibrant-kernel-subsystem-community-hans-de-goede-red-hat #LinuxKernel
Gustavo A. R. Silva 
gustavoars@fosstodon.org
The video of my presentation at OSSummit Europe is now available. 🇳🇱🐧
Those were 180 slides in 40 mins. 🫣😁 I hope people find it useful. Thanks! 🙂
Abstract & slides in the comments.
Linux Kernel Self-Protection Project 🐧🛡⚔️
#OSSummit #Linux #OpenSource
Michael Opdenacker
MichaelOpdenacker@fosstodon.orgSuggestion for the week-end: Open Source Summit Europe 2025 video binge watching.
The Linux Foundation has just released all the videos they took at the OSS EU 2025 conference in Amsterdam. They are so many of them that they are hard to count!
https://www.youtube.com/watch?v=IGDWXA32xG4&list=PLbzoR-pLrL6qKwLt8A787ggMLHNivOHve
So, now you can attend OSS EU 2025 and the Embedded Linux Conference Europe 2025 free of charge, or if you attended, you can watch the many interesting talks that you missed.
Thanks to Ross Burton for sharing the news!
postmarketOS
postmarketOS@social.treehouse.systemsour community have always tried to embrace the upstream-first approach to development, and one of the largest roadblocks in that respect is often the Linux Kernel itself.
For better or worse it takes quite a lot of effort to get devicetree files and drivers upstreamed, but this is by far one of the more important goals for wider Linux Mobile adoption: upstream support makes devices more visible and encourages kernel maintainers to take more of an interest in the work we do
with that in mind, we are proposing an adjustment to the community device category requirements: to get your device into the community category it would now HAVE to have a devicetree in upstream, more specifically the upstream kernel needs to boot with some kind of display output and a working USB port - the bare minimum for easy tinkering, testing, and further development.
We hope that this will encourage device maintainers to get involved in upstream kernel development and submit their work rather than keeping everything in a kernel fork that they maintain
We are very open to feedback on this, please let us know what you think in the GitLab issue
https://gitlab.postmarketos.org/postmarketOS/postmarketos/-/issues/116
Joe Groff
joe@f.duriansoftware.comTill Kamppeter
till@ubuntu.socialUrgent help for OpenPrinting needed!
As many here know, I am co-founder and lead of OpenPrinting since 2001, known as the print guru for Linux and free software by many. I also got one of the 8 fellows of the Linux Foundation for this.
Up to now I was working at Canonical, hired back in 2006 just to run OpenPrinting and also to maintain printing-related Ubuntu packages.
... 🧵
Please boost.
#OpenPrinting #LinuxFoundation #getfedihired