Posts
350Following
95Followers
3927Greg K-H
gregkhhttps://www.volkskrant.nl/kijkverder/v/2024/sabotage-in-iran-een-missie-in-duisternis~v989743/
(disclaimer, yes, it's in Dutch, but tools like google translate work well on it, and no, my Dutch is not good enough to read it in the native form, still working on that, ik lees een beetje Nederlands.)
warthog9
warthog9@social.afront.orgOk, Vger's MX is heading off to point to subspace on Thursday. Web services are staying put for now, so if you link to / use Vger it's staying put (possibly with a massive OS upgrade coming).
The fundamental infrastructure isn't going anywhere even if it has to change it's name, and should lists not want to head off to subspace, infradead, etc I've got https://vger.email up and running and capable of picking things up should anyone want to jump.
End of an era, Vger's been independent of kernel.org from it's start, but it's a non-trivial set of lists that literally keep the Linux kernel community moving, and has since it's inception. It's realistically needed an upgrade to deal with a plethora of problems, and frankly various large e-mail providers have made it nearly untenable to keep doing without it nearly being a full time job (at least at the scale that Vger's at)
Mike Dolan
mdolan@fosstodon.orgDirk: "Are you worried about bugs from LLM hallucinations getting into the #Linux kernel?" Linus: "Well I see all the bugs that come in without LLMs, and so, no I don't." (Paraphrasing the exchange)
K. Ryabitsev-Prime 🍁
monsieuriconJens Axboe
axboe@fosstodon.orgIf you enjoy the hairiest of bug hunts with a thrilling conclusion, this one is for you. The hunt and hair pulling:
and the conclusion:
Hats off to Timothy for seeing this one through to completion!
K. Ryabitsev-Prime 🍁
monsieuriconhttps://lore.kernel.org/workflows/20231115-black-partridge-of-growth-54bf2e@nitro/
K. Ryabitsev-Prime 🍁
monsieuriconSo many facts untold,
Queries left unbidden,
Concealed below the fold.
My head droops to the table,
But I must remain informed:
"Is the kernel stable?"
"How is babby formed?"
Kees Cook (old account)
kees@fosstodon.orgRFC for the replacing the Linux kernel #Android #Binder driver with a fully functional #Rust version:
https://lore.kernel.org/lkml/20231101-rust-binder-v1-0-08ba9197f637@google.com/
Embedded Recipes
embeddedrecipes@fosstodon.orgAll the talks from Embedded Recipes 2023 are now online, including "The TTY Layer: the Past, Present, and Future" by @gregkh https://www.youtube.com/watch?v=g4sZUBS57OQ&list=PLwnbCeeZfQ_Mi7gjUpLZxXGOcEBS_K8kH&index=5 #er2023
Greg K-H
gregkhMy policy is that I do not take any output of any "AI" tools unless the providence of the data that was used to feed the AI tool can be proven to be under the proper copyright rules as to be compatible with the GPLv2 license.
So in other words, nothing from chatgpt at all, that's obviously full of copyrighted works that are not allowed to be reused in this manner.
Thorsten Leemhuis (acct. 1/4)
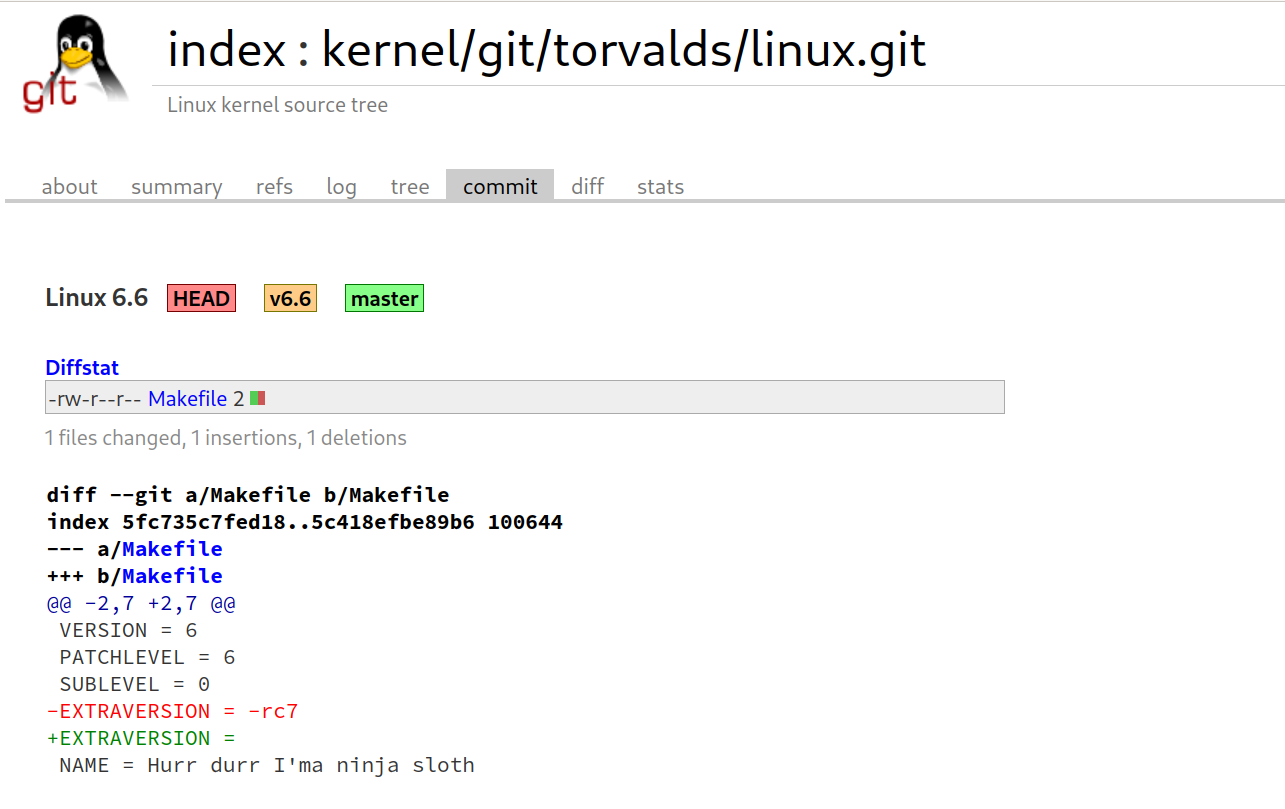
kernellogger@fosstodon.org#Linux #kernel 6.6 is out: https://lore.kernel.org/all/CAHk-=wiZuU984NWVgP4snp8sEt4Ux5Mp_pxAN5MNV9VpcGUo+A@mail.gmail.com/
"""So this last week has been pretty calm, and I have absolutely no excuses to delay the v6.6 release any more, so here it is. […] Linus"""
For an overview of new features, check out the two #LinuxKernel 6.6 merge window articles from @LWN or the Kernelnewbies summary:
https://lwn.net/Articles/942954/ and https://lwn.net/Articles/943245/
Mike Dolan
mdolan@fosstodon.orgNot a tragedy: "The greatest value that #opensource foundations bring is the creation of a neutral collaboration hub for everyone participating in, and taking a dependency on, a project."
Greg K-H
gregkhGreg K-H
gregkhhttps://www.iso.org/standard/72311.html
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgSo I presented today on EU CRA, NIS2 and other initiatives to regulate code/hardware/services. One consistent piece of feedback I got is that the amount of upcoming regulation is so huge that even dedicated professionals are unable to keep track of it all. So it is not just me (or you). It is _a lot_. https://berthub.eu/one/EU%20and%20you.pdf
Embedded Recipes
embeddedrecipes@fosstodon.orgHow to fix the TTY layer in Linux?
@gregkh explains at #er2023
https://git.sr.ht/~gregkh/presentation-tty/tree/9afefcf3171a02e5eee19639ec62456511902a56/item/tty.pdf
Thorsten Leemhuis (acct. 1/4)
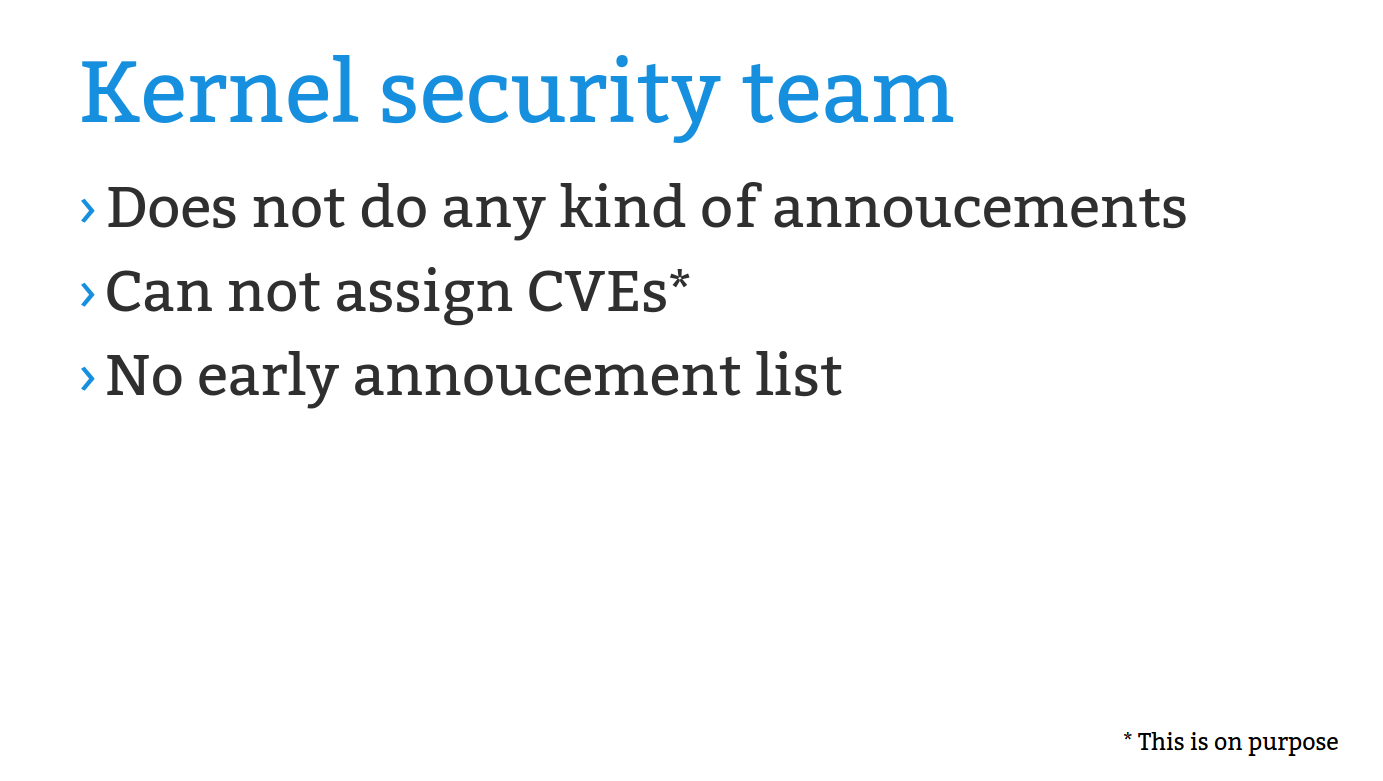
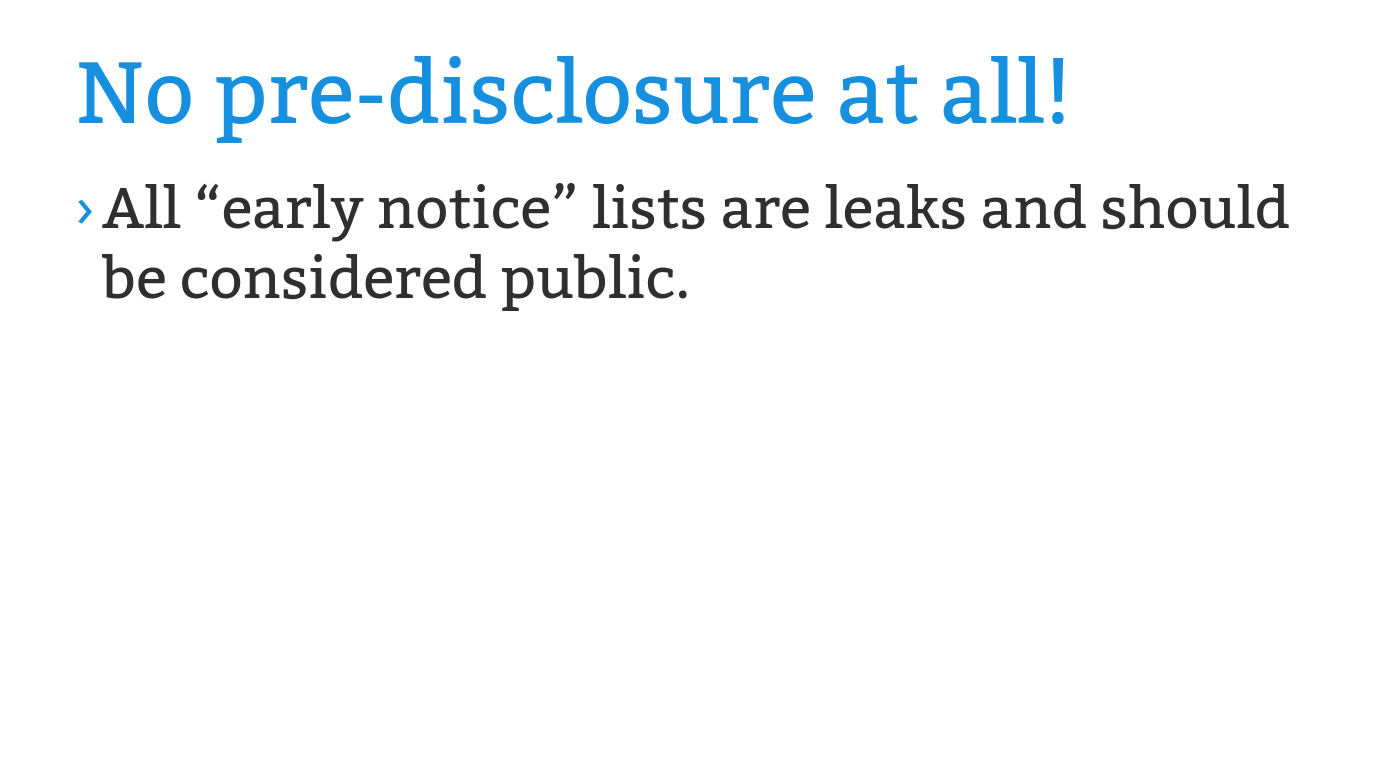
kernellogger@fosstodon.orgSlides and recording of @gregkh's great @KernelRecipes talk "#Linux #Kernel security demistified" are now online:
Video: https://www.youtube.com/watch?v=xDHTn0auo2w&t=14975s (that's a section of the live stream) #LinuxKernel
Greg K-H
gregkhKernel Recipes
KernelRecipes@fosstodon.org@davem_dokebi our godfather on stage for a sump up of netconf 2023 #kr2023