Posts
350Following
95Followers
3867Tweakers
Tweakers@mastodon.socialMinister Adriaansens: verhuizing SIDN naar Amazon 'nog geen voldongen feit' https://tweakers.net/nieuws/220102/minister-adriaansens-verhuizing-sidn-naar-amazon-nog-geen-voldongen-feit.html
Greg K-H
gregkhLinux Kernel Ecosystem" in which different distros, and Android, are evaluated as to how up to date they stay with upstream fixes. Note that RHEL or CentOS is not evaluated "because of the lack of public git repositories or insufficient data."
About time someone started writing papers about this stuff...
Omkhar
Omkhar@infosec.exchangeWe're #hiring at the @openssf !
Our mission is to ensure the security of open source software for all.
Are you a seasoned Technical Program Manager excited about #cybersecurity and #opensource who wants a full-time #remotejob?
Apply: https://openssf.jobboard.io/jobs/314008394-technical-program-manager-at-openssf
K. Ryabitsev-Prime 🍁
monsieuriconThorsten Leemhuis (acct. 1/4)
kernellogger@fosstodon.orgDid a quick *rough* check:
* 65 #Linux #kernel CVE announcements from Greg so far
* 55 of those refer to a mainline commit
* 10 of those were marked for backporting to stable/longterm
And that's why Greg backports a lot of #LinuxKernel mainline commits to stable/longterm that are *not* tagged for backporting -- and why "only backport changes mainline developers[1] tagged for backporting" is a bad idea.
[1] reminder, such tagging is optional, as participation in stable/longterm is optional
sjvn
sjvn@mastodon.socialThe #Linux kernel developers are now issuing their own, more accurate Common Vulnerabilities and Exposures #security bulletins. https://opensourcewatch.beehiiv.com/p/linux-gets-cve-security-business by @sjvn
The Linux kernel developers are now in charge of its Common Vulnerabilities and Exposures (CVE) security problems.
lcamtuf 


lcamtuf@infosec.exchange
Computer folks, remember the precedence of operators! Consult this handy list if in doubt:
() [] -> .
! ~ ++ --
* / %
+ -
<< >>
< <= > >=
== != &=
=== &&& |||
?: ??= ( ^..^)ノ
(╯°□°)╯︵ ┻━┻
Kees Cook (old account)
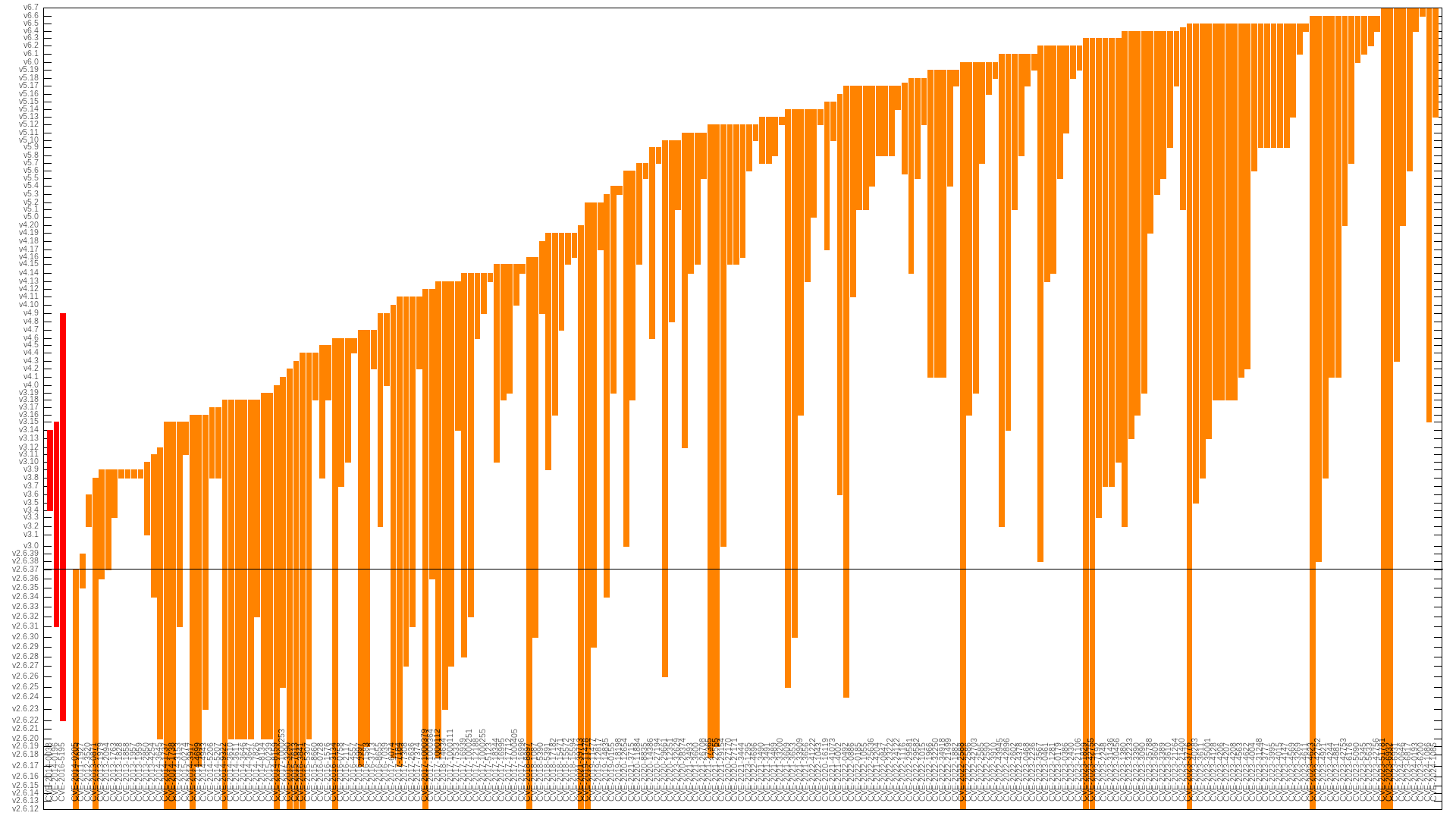
kees@fosstodon.orgLast time I did a Linux kernel security flaw lifetime analysis was back in 2021. It showed the average time between flaw introduction and fix was 5.5 years for 108 "high priority" CVEs:
https://outflux.net/slides/2021/lss/kspp.pdf
I refreshed my dataset today and was surprised to see that now with 103 more CVEs, it's still holding at 5.5 years. This actually means Linux is getting faster at finding issues, but the (diminishing) technical debt of the past is still dragging down the average.
LWN.net is now @LWN@lwn.net
LWN@fosstodon.org[$] A turning point for CVE numbers https://lwn.net/Articles/961978/ #LWN
Greg K-H
gregkhThis has taken a long time, I'd like to thank all the groups that helped, and especially the CVE group themselves. Our application was a bit different than other groups, but they understood that this is important for security overall.
Greg K-H
gregkhK. Ryabitsev-Prime 🍁
monsieuriconHowever, I do have to manage multiple priorities and my #1 priority remains supporting the LF IT backend infrastructure for kernel.org (plus a few other similarly aligned projects), in addition to managing a small team of fellow IT pros. If I have to choose between working on tooling and working on something that requires attention from the infra side of things, the infra work is always prioritized for practical/operational/security reasons.
So, when I say that "my request hasn't been approved yet" I don't mean it in the sense that someone is telling me not to work on b4 or bugbot -- it just means that we haven't properly reallocated resources to allow me to prioritize tooling work -- yet. To properly request these resources, I need to present a clear vision of what we are trying to accomplish, why it makes sense to work on that (as opposed to, say, just moving things over to some large commercial forge and telling everyone to switch to that), and how this effort helps Linux development in the overall scheme of things. I'm sure we'll get there soon, I'm just explaining why we're not there yet (and hence why some cool stuff I've talked about hasn't made it to b4). :)
LWN.net is now @LWN@lwn.net
LWN@fosstodon.orgSome weekend stable kernel updates https://lwn.net/Articles/958860/ #LWN
Kees Cook (old account)
kees@fosstodon.orgAfter 4 years the strlcpy() API has been fully removed from the Linux kernel. Long live strscpy().
https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=d26270061ae66b915138af7cd73ca6f8b85e6b44
Next up, strncpy()!
https://github.com/KSPP/linux/issues/90
Luis Villa
luis_in_brief@social.coop"We estimate the supply-side value of widely-used OSS is $4.15 billion, but that the demand-side value [replacement value for each firm that uses the software] is much larger at $8.8 trillion. We find that firms would need to spend 3.5 times more on software than they currently do if OSS did not exist."
Greg K-H
gregkh— How to say you are a government agency without saying you are a government agency.
Kees Cook (old account)
kees@fosstodon.orgSequentially in my feed: a toot about the Mars helicopter Ingenuity and its continued flying around, followed by a toot about Linux 4.14 reaching EOL.
Which reminds me, Ingenuity is running a 3.6 kernel. And it has the only excuse I can tolerate for having not been upgraded: it's on a different planet. ;)
Greg K-H
gregkhIt's been a good 6 years, and it was a solid kernel version for its time, but anyone still using it should have moved off it a long time ago as it has been showing its age for quite a while.
Bert Hubert NL 🇺🇦🇪🇺🇺🇦
bert_hubert@mastodon.nlUPDATE: Blijkt dat het artikel 73 al sinds 2013 vragen oproept.
Vandaag in het nieuws dat een AIVD agent meegeholpen zou hebben aan het saboteren van het Iraanse kernwapenprogramma. Dit lijkt me uitstekend. Maar politiek Den Haag schijnt van niets geweten te hebben. En dat zou best kunnen, want de AIVD en MIVD mogen agenten dingen laten saboteren zonder toestemming van minister of toetsingscommissie, en dat is raar:
https://berthub.eu/articles/posts/het-curieuze-artikel-73-aivd-mivd/
Greg K-H
gregkhhttps://www.volkskrant.nl/kijkverder/v/2024/sabotage-in-iran-een-missie-in-duisternis~v989743/
(disclaimer, yes, it's in Dutch, but tools like google translate work well on it, and no, my Dutch is not good enough to read it in the native form, still working on that, ik lees een beetje Nederlands.)