Posts
351Following
95Followers
3956Lennart Poettering
pid_eins@mastodon.socialIn systemd we started to do more and more Varlink IPC (instead of or 9n addition to D-Bus), and you might wonder what that is all about. In this AllSystemsGo talk I try to explain things a bit, enjoy: https://media.ccc.de/v/all-systems-go-2024-276-varlink-now-
I'm at Kernel Recipes 2024, starting the live blog now https://kernel-recipes.org/en/2024/category/live-blog/
Day 1 Morning: https://kernel-recipes.org/en/2024/2024/09/18/live-blog-day-1-morning/
Have offered to help (or at least be cc'd in hopes I have time for it :) on mm binding stuff fwiw from the kernel side.
And also I really do have to sit down with rust finally... Maybe advent of code this year...
Steven Rostedt
rostedtTHIS IS IT!!!
The last hurdle for PREEMPT_RT being merged into mainline has just removed by this pull request. Leaving the door open for PREEMPT_RT to be added to 6.12!
Kees Cook (old account)
kees@fosstodon.org"Defects-in-Depth: Analyzing the Integration of Effective Defenses against One-Day Exploits in Android Kernels" is a great read:
https://www.usenix.org/system/files/usenixsecurity24-maar-defects.pdf
"integrating defense-in-depth mechanisms from the mainline Android kernel could mitigate 84.6% of these exploitation flows"
h/t @rene_mobile
@IAIK
Thorsten Leemhuis (acct. 1/4)
kernellogger@fosstodon.org#Linux 6.11 is out:
https://lore.kernel.org/lkml/CAHk-=whVpSHw9+4ov=oLevfv8sPYbh59T_9VKif-6Vqkr41jQA@mail.gmail.com/
'"I'm once again on the road and not in my normal timezone, but it's Sunday afternoon here in Vienna, and 6.11 is out.
The last week was actually pretty quiet and calm, which is nice to see. […]
Anyway, with this, the merge window will obviously open tomorrow, and I already have 40+ pull requests pending. That said, exactly _because_ I'm on the road, it will probably be a fairly slow start […] please be patient."'
Greg K-H
gregkhhttps://lore.kernel.org/all/20240913112643.542914-1-benno.lossin@proton.me/
It's not a "silver bullet" for why we should be using rust in the Linux kernel, but it is a "big giant sledgehammer" to help squash and prevent from happening MANY common types of kernel vulnerabilities and bugs (remember, "all input is evil!" and this change forces you to always be aware of that, which is something that C in the kernel does not.)
I had always felt that Rust was the future for what we need to do in Linux, but now I'm sure, because if we can do stuff like this, with no overhead involved (it's all checked at build time), then we would be foolish not to give it a real try.
And yes, I've asked for this for years from the C developers, and maybe we can also do it there, but it's not obvious how and no one has come up with a way to do so. Maybe now they will have some more incentive :)
Jani Nikula
jani@fosstodon.orgMust not make a comparison. Really. Must not. But just saying...
Clang Built Linux took literally years of effort. And it's all still C, just a different compiler.
Did anyone really expect Rust for Linux to be a breeze?
I know, I know, apples and oranges.
🐧sima🐧
sima@chaos.socialkangrejos in copenhagen was great, but the absolute 🤯 moment was when I learned that GFP_ stands for get_free_pages
I had no idea. and @gregkh next to me had the same https://xkcd.com/1053/ experience
Paul Moore
securepaul@fosstodon.orgAnyone else often find themselves starting a retort/reply to a thread here, only to abandon the effort part way through, because you realize your time is better spent supporting/fixing/making things than trying to educate people who haven't bothered to do any of the most basic level of self-education on the given topic?
Greg K-H
gregkhhttps://lore.kernel.org/all/TYUPR06MB6217E6BD48B0B491AA169E67D29D2@TYUPR06MB6217.apcprd06.prod.outlook.com/
Greg K-H
gregkhhttps://git.sr.ht/~gregkh/usbutils/commit/86dcab8964901d15b87b156546559c8ae28bd9fe
jelly
jelly@dodgy.downloadNew blogpost about creating bit-by-bit reproducible images with mkosi(!)
https://vdwaa.nl/mkosi-reproducible-arch-images.html
#archlinux #systemd #mkosi
K. Ryabitsev-Prime 🍁
monsieuriconMe: "Oh, yeah, for sure."
Greg K-H
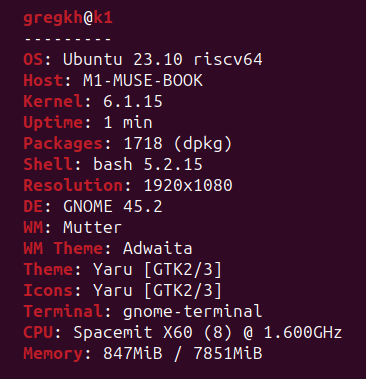
gregkhKernel source is all public (there's a 6.1.y and 6.6.y tree at the moment), hopefully will start working on getting it all merged upstream to make it a proper platform for others to use.
Thorsten Leemhuis (acct. 1/4)
kernellogger@fosstodon.orgI'd really like to read a well researched article that sums up how Linux distros reacted to the massive influx of #Linux #kernel CVE that started ~half a year – both for their #LinuxKernel packages and their live-patching offerings.
But I guess that is an enormous amount of work that no media outlet in this world is willing to pay anyone for writing. 😕
Slide taken from @gregkh's "Why are there so many kernel CVEs?" talk he gave at OSS China yesterday (https://social.kernel.org/objects/c9979d9f-399f-428b-ac56-c41598076dfa ) #LinuxKernel
sjvn
sjvn@mastodon.socialDon't panic! It's only 60 Linux CVE security bulletins a week https://zdnet.com/article/dont-panic-its-only-60-linux-cve-security-bulletins-a-week/ by @sjvn
Sure, it sounds like a lot, but it's just business as usual for #Linux #security.
Greg K-H
gregkhhttps://kccncossaidevchn2024.sched.com/event/ed2b39a9a0cdfc1df18de67ce0c2f6be
Link to git repo for the slides if the schedule site acts odd for you:
https://git.sr.ht/~gregkh/presentation-security
It was fun, and will be the "set up" for my Kernel Recipes talk in Paris in a few weeks (only 3 conferences to go between now and then, travel is back in full swing.)