Posts
5167Following
335Followers
509OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkoIt even has tool called icat for raw shell.
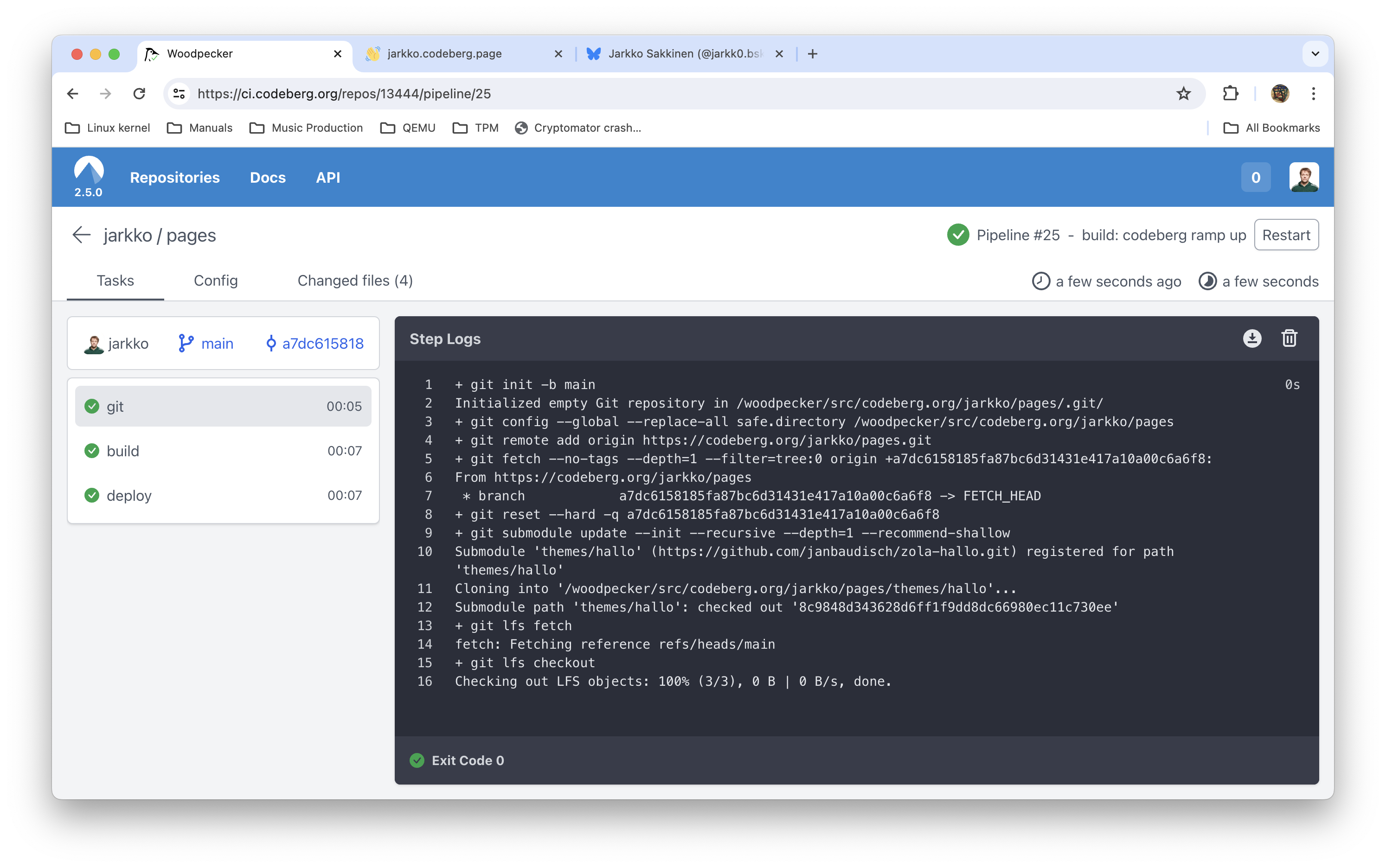
Jarkko Sakkinen
jarkkoJarkko Sakkinen
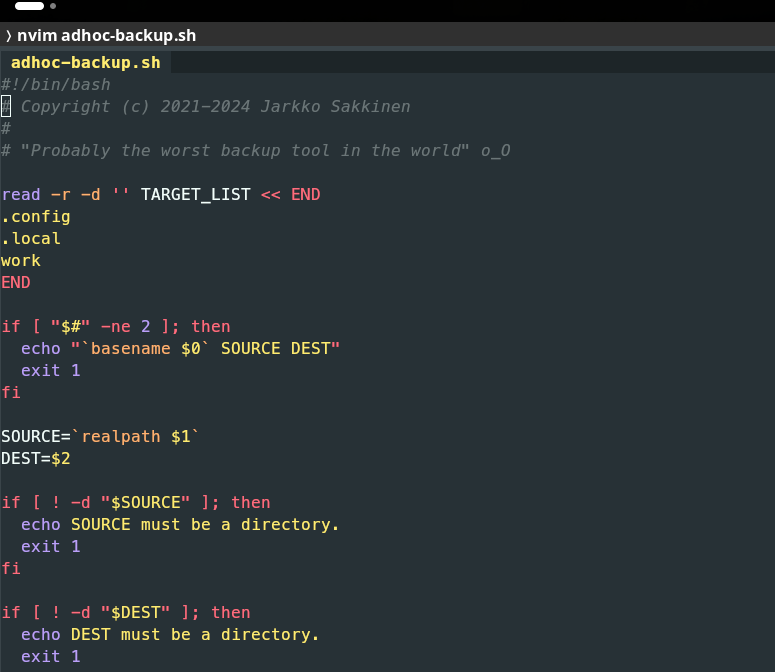
jarkkoneed this for my #btrfs to #ext4 migration 🤷 https://codeberg.org/jarkko/adhoc-backup #git
#codesberg - “Probably the best git hosting in the world”
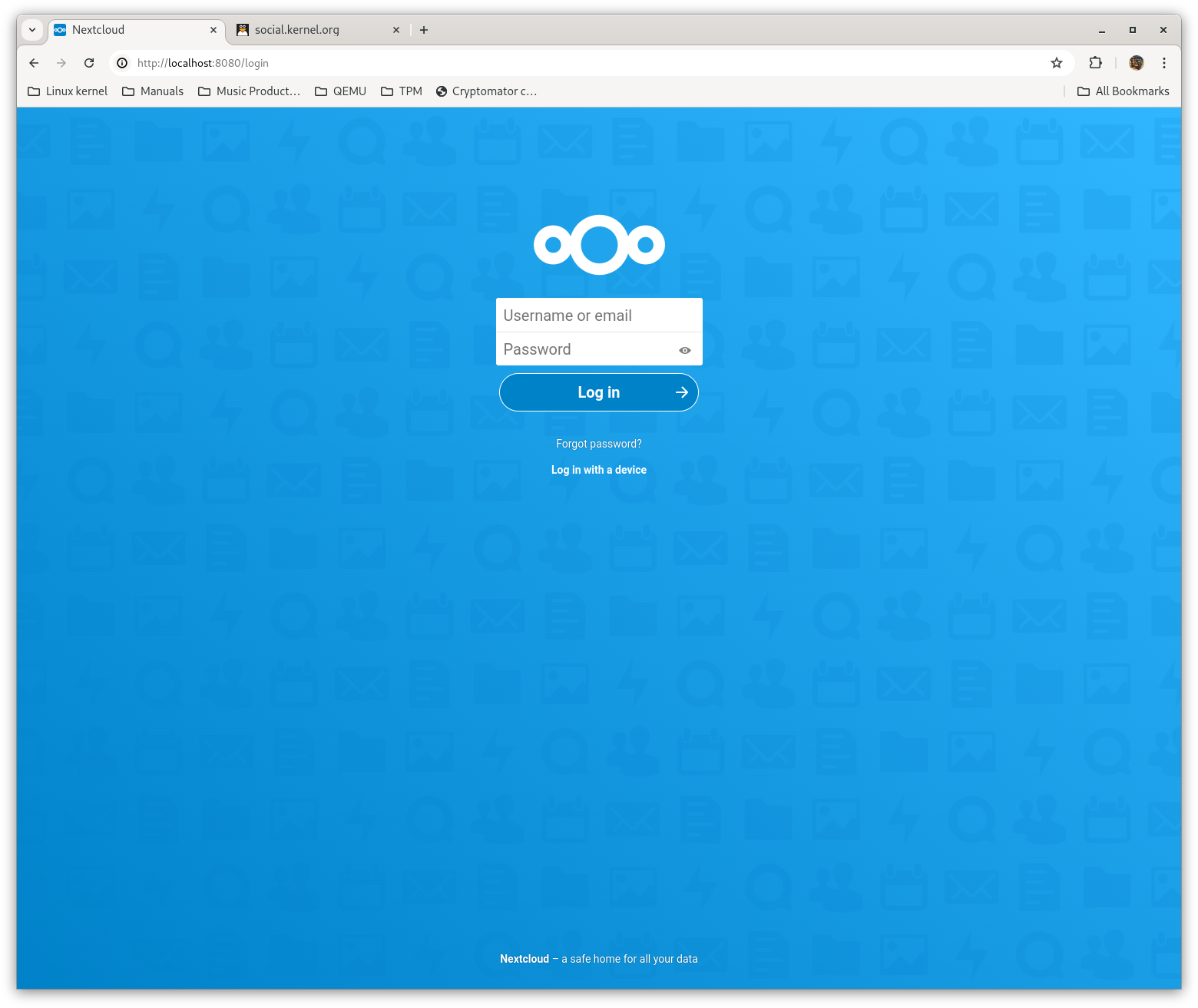
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoUsing #Storj and local #Nextcloud (one per machine) is actually quite easy:
!/usr/bin/env bash
# Taken from https://fedoramagazine.org/nextcloud-20-on-fedora-linux-with-podman/.
podman network create nextcloud-net
podman volume create nextcloud-app
podman volume create nextcloud-data
podman volume create nextcloud-db
# MariaDB
podman run --detach \
--env MYSQL_DATABASE=nextcloud \
--env MYSQL_USER=nextcloud \
--env MYSQL_PASSWORD=DB_USER_PASSWORD \
--env MYSQL_ROOT_PASSWORD=DB_ROOT_PASSWORD \
--volume nextcloud-db:/var/lib/mysql \
--network nextcloud-net \
--restart on-failure \
--name nextcloud-db \
docker.io/library/mariadb:10
# Nextcloud
podman run --detach \
--env MYSQL_HOST=nextcloud-db.dns.podman \
--env MYSQL_DATABASE=nextcloud \
--env MYSQL_USER=nextcloud \
--env MYSQL_PASSWORD=DB_USER_PASSWORD \
--env NEXTCLOUD_ADMIN_USER=NC_ADMIN \
--env NEXTCLOUD_ADMIN_PASSWORD=NC_PASSWORD \
--volume nextcloud-app:/var/www/html \
--volume nextcloud-data:/var/www/html/data \
--network nextcloud-net \
--restart on-failure \
--name nextcloud \
--publish 8080:80 \
docker.io/library/nextcloud:20
So no need to use Oracle cloud for this. And instances do not really need to necessarily to sync up given the user count.
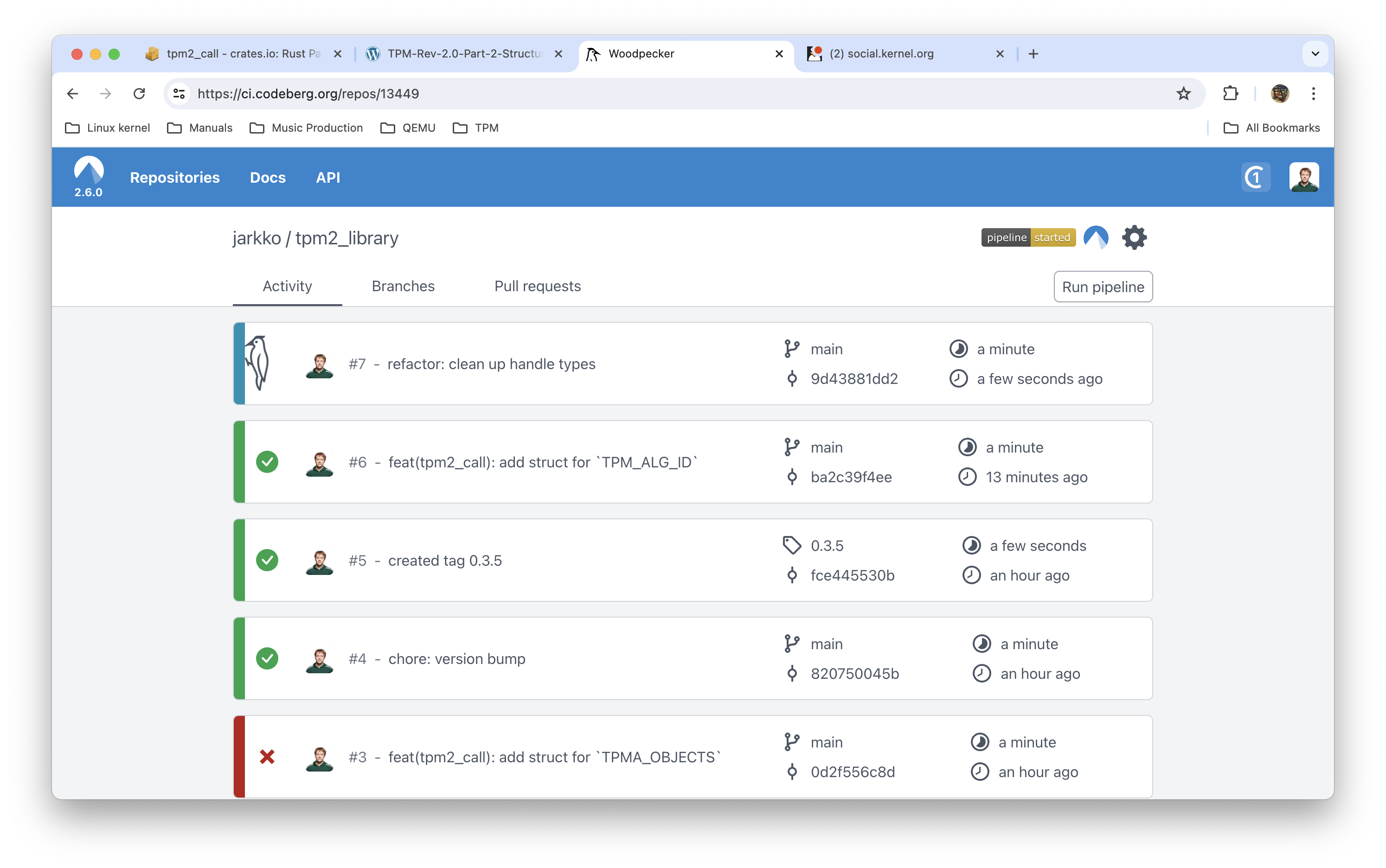
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoStumped into a bug straight out right in the get-go ;-) It goes like this…
First, consider:
❯ cat pubkey.txt
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC3un58bzSwrEXD5PMNuT9nYhyBfdiEeDrcQd3Facw9PZihlFwfec+iz00u4bbNmcrG0YhT056PSnqIR4DqGSK3N2iancS1anBfgNS7Se02jcOyoHsgrDFH6MxEgkZLoFY8XodE5NPDGt6rPoiy6MeN0jKNvuMMQ9UFge67ky0pWZjyDjdyXERZWEIjcp+OQXMaFAU3zJCbnaLgVn7CizZcwriu2ElMg0tVvxdkW59QW9dSgmCdF4zwSvLN6XVpaCw+fiXV+09Wq5PT65qT/rWC/0yO4BWuZFteX8gXyDQBJqEzNKjkvACNFI4ublSUQO7zYnyFQjlww04+afTFkWZYIV2UtOZYzJaTg90DT3fQBkJMxsHHc4G8eF+SveIy1tiOq7jf8btvdKLCyvIrNMlhB99YPAzBFUd/X/w7uOEtm7L4zoWa+6YRjtKiPtuaeGGQVr3CEU/L9rtPY9PfkPOxGUahnM5M2MsST5NPZ9+tWvhjEFX4nSYo5EShFBE9m01sa675mzrOwsBXwi7AlBZtT4hEYN1jvVUVXrwEC8W7RKy3C0mgU/mlnxXHp23af9YEkjiYA5ZBmK4+q85o0pBf616cLAhzebDwoT5v9VkYY+q1t3nLWpaG9HAH0BmPyEW0jlB1jxqwUvlmWQ14vtZUOAzrFnAoUKDVLTeuK+w5vw== cardno:23_610_166
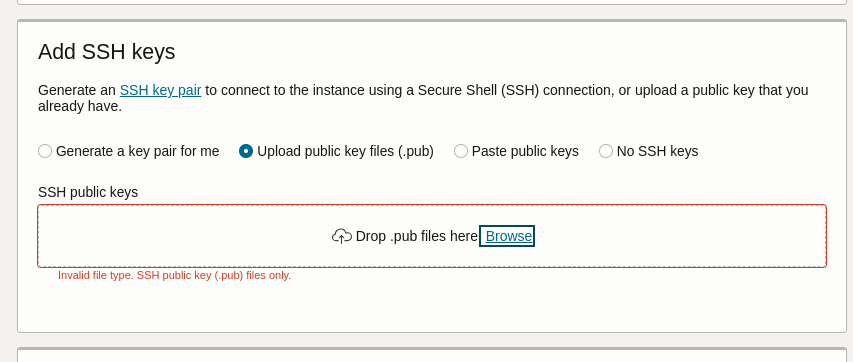
Uploading this results “Invalid file type. SSH public key (.pub) files only” (screenshot #1).
Then, consider:
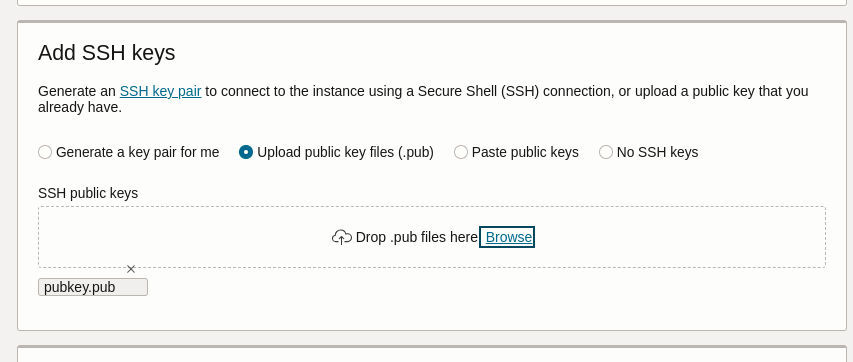
❯ mv pubkey.{txt,pub}
❯ cat pubkey.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC3un58bzSwrEXD5PMNuT9nYhyBfdiEeDrcQd3Facw9PZihlFwfec+iz00u4bbNmcrG0YhT056PSnqIR4DqGSK3N2iancS1anBfgNS7Se02jcOyoHsgrDFH6MxEgkZLoFY8XodE5NPDGt6rPoiy6MeN0jKNvuMMQ9UFge67ky0pWZjyDjdyXERZWEIjcp+OQXMaFAU3zJCbnaLgVn7CizZcwriu2ElMg0tVvxdkW59QW9dSgmCdF4zwSvLN6XVpaCw+fiXV+09Wq5PT65qT/rWC/0yO4BWuZFteX8gXyDQBJqEzNKjkvACNFI4ublSUQO7zYnyFQjlww04+afTFkWZYIV2UtOZYzJaTg90DT3fQBkJMxsHHc4G8eF+SveIy1tiOq7jf8btvdKLCyvIrNMlhB99YPAzBFUd/X/w7uOEtm7L4zoWa+6YRjtKiPtuaeGGQVr3CEU/L9rtPY9PfkPOxGUahnM5M2MsST5NPZ9+tWvhjEFX4nSYo5EShFBE9m01sa675mzrOwsBXwi7AlBZtT4hEYN1jvVUVXrwEC8W7RKy3C0mgU/mlnxXHp23af9YEkjiYA5ZBmK4+q85o0pBf616cLAhzebDwoT5v9VkYY+q1t3nLWpaG9HAH0BmPyEW0jlB1jxqwUvlmWQ14vtZUOAzrFnAoUKDVLTeuK+w5vw== cardno:23_610_166
As can been seen from screenshot #2, the public key was successfully uploaded. For me this looks like as if validation was based on the filename extension o_O
A correct validation would ignore the file’s name and base validation on RFC 4716: The Secure Shell (SSH) Public Key File Format.
Jarkko Sakkinen
jarkkoNOT true. TPM_ECC_CURVE_448 exists in the TCG algorithm registry. Table 5.1 in this same specifications enumerates ECC curves supported by TPM firmware (or in the spec TCG “TPM 2.0 Library”) interface.
Sometimes features can even land through firmware updates. especially for fTPM’s in Intel, ARM (via SMC AMD CPU’s this is feasible approach.
I’ve been also started to lobby the idea of getting P256K1 to the registry based on principle of equally feasible playing field for established corporations and growth companies of variable side (aka startups):
- Corporates need to have their NIST curves.
- There’s a critical mass of blockchain associated startups, in varying levels. So to have working capitalism also “Bitcoin curve” should be there.
I’m going to also write P256K1 software primitives to Linux kernel to enable more secure options for managing that sort of assets.
I do it part of my role as Linux kernel key-ring co-maintainer. My job is to identity widely use key types, enable them and call it a day, i.e. create equal capitalist market place for every actor.
I would enable P256K1 even if I hated blockchains by guts because it is my freaking job :-) Liking and disliking about stuff is part of leisure time (or when getting drunk which is part of leisure time ;-)).
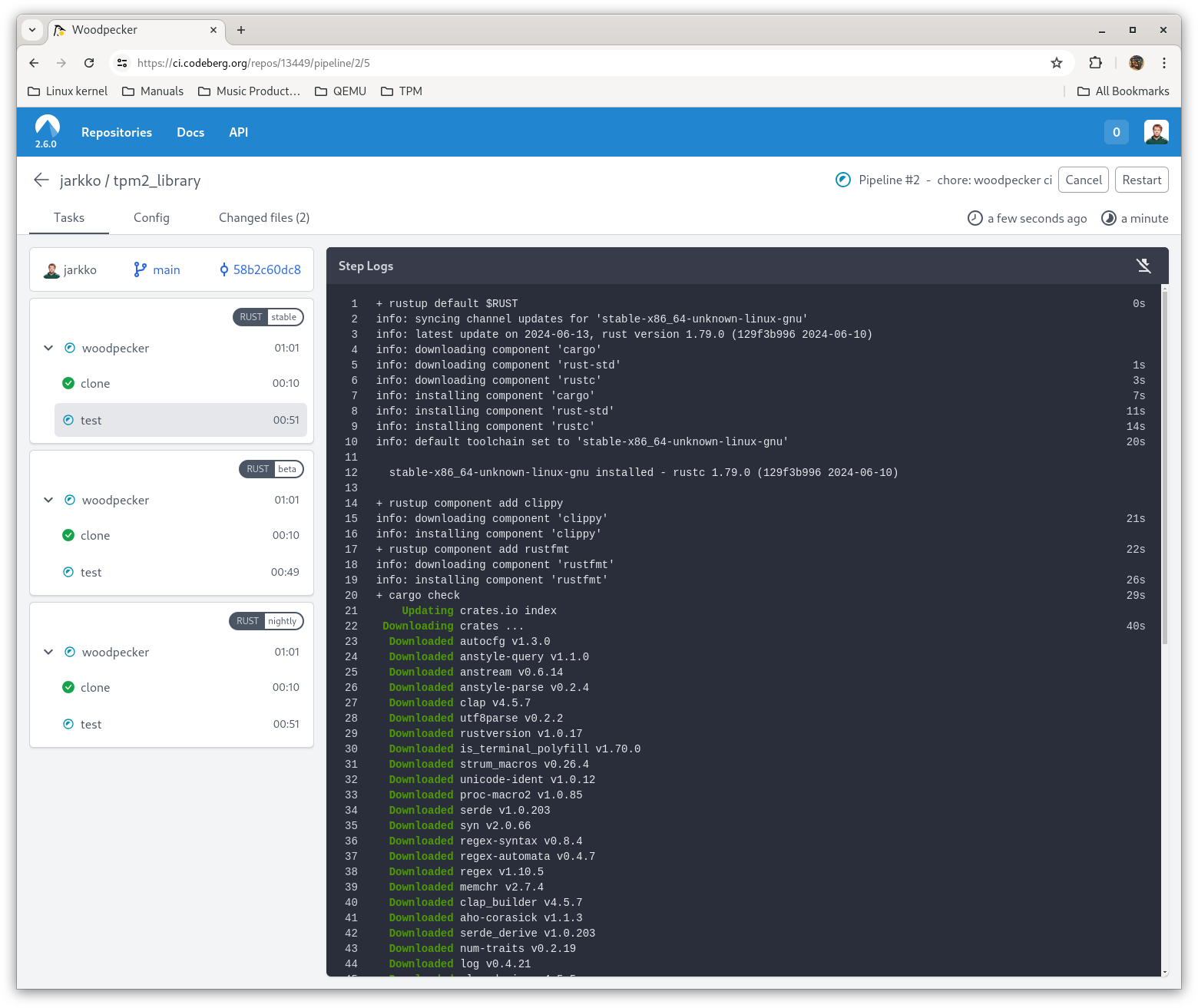
Jarkko Sakkinen
jarkkoRamping up #systemd #kernel #QA: DONE!
URL: https://gitlab.com/jarkkojs/linux-tpmdd-test
Contents:
CMakeLists.txt
Config.in
LICENSE
README.md
board/x86_64/buildroot.conf
board/x86_64/genimage.cfg
board/x86_64/kselftest-tpm2.exp.in
board/x86_64/linux.config
board/x86_64/post-build.sh
board/x86_64/post-image.sh
board/x86_64/run-qemu.sh.in
board/x86_64/run-tests.sh.in
board/x86_64/ssh_config.in
buildroot-2024.02.3.patch
configs/x86_64_defconfig
external.desc
external.mk
I’ve been editing the history while ramping up this starting point but I will stop this chaotic workflow now and commit to this baseline :-) So no worries if sending pull requests…
This is also CI capable environment assuming that runner has:
- QEMU
- swtpm
The GIF-animation shows the proof that it actually also works.