Posts
4655Following
319Followers
484OpenPGP: 3AB05486C7752FE1
Jonathan Corbet
corbethttps://lwn.net/Articles/979912/
What an incredible loss.
Jarkko Sakkinen
jarkkoMy fav feature so far: systemd-run0. It's excellent debugging tool for testing PolKit and other access control layers in Linux (in my daily use I still tend to sudo).
Jarkko Sakkinen
jarkkoI put my old Unprivileged #Nix notes to Medium so that I won’t loose them by mistake: https://medium.com/@jarkko.sakkinen/unprivileged-nix-2c9f06b99f8e
I.e. how to get a fresh and most recent userland to any remote Linux system that you have SSH access to when exactly two contraints are met:
- User NS is ON.
- PID NS is ON.
Or to put in other words: Nix Home Manager without NixOS recipe…
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkko#Rust #RustCrypto #rustlang
Tobias Bieniek
tb@hachyderm.io crates.io celebrates its 10 year anniversary today! 🎉
crates.io celebrates its 10 year anniversary today! 🎉
On 2014-06-25 Alex Crichton created the initial commit in the crates.io git repository: https://github.com/rust-lang/crates.io/commit/54cfc8d
A lot has happened since then, and the current crates.io team would like to say "thank you!" to all current and former contributors to crates.io and the ecosystem around it! 🤗
Jarkko Sakkinen
jarkkoBoth are used for disassembly but still pretty different type of instruments.
Depite reverse engineering of malware and kernel engineering have commonalities in tools, they're still different type of Sudoku's... Malware has more "easter eggs" so to speak ;-) And requires factors more dynamic analysis and simulation.
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
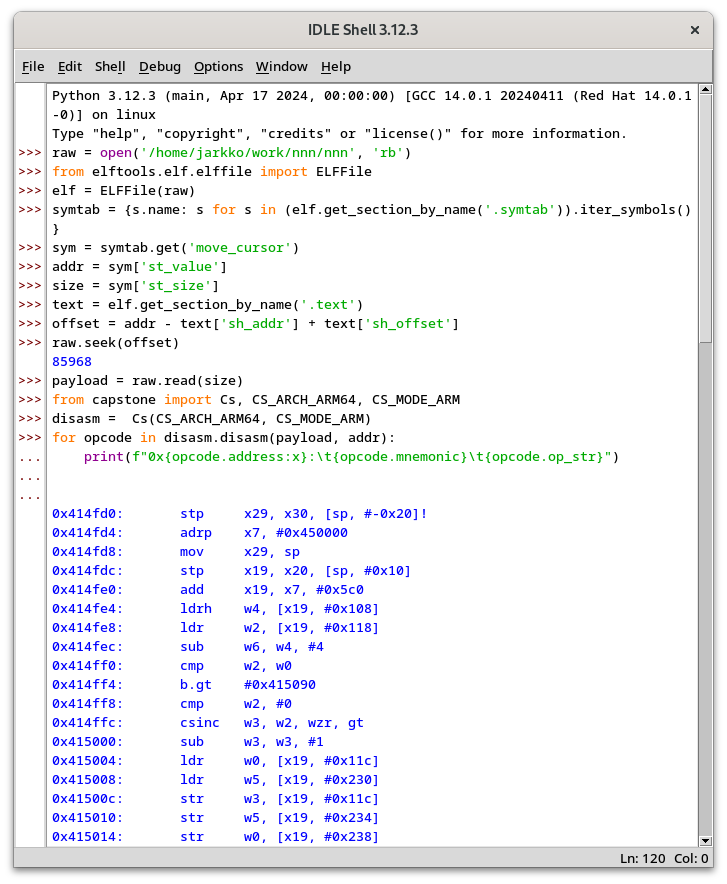
jarkkoIf #Radare2 vs #Rizin makes no sense to you, perhaps #Python will. It is pretty solid tool for driving #Capstone :-)
Transcript:
raw = open('/home/jarkko/work/nnn/nnn', 'rb')
from elftools.elf.elffile import ELFFile
elf = ELFFile(raw)
symtab = {s.name: s for s in (elf.get_section_by_name('.symtab')).iter_symbols()}
sym = symtab.get('move_cursor')
addr = sym['st_value']
size = sym['st_size']
text = elf.get_section_by_name('.text')
offset = addr - text['sh_addr'] + text['sh_offset']
raw.seek(offset)
payload = raw.read(size)
from capstone import Cs, CS_ARCH_ARM64, CS_MODE_ARM)
disasm = Cs(CS_ARCH_ARM64, CS_MODE_ARM)
for opcode in disasm.disasm(payload, addr):
print(f"0x{opcode.address:x}:\t{opcode.mnemonic}\t{opcode.op_str}")
Just got a bit familiar this. The main benefits are obviously:
- Recursive traversal #disassembly (vs linear sweep style in
objdump) - Re-usable analysis
- No boundaries how you can post-process the analysis (or visualize it)
I find this super fascinating!