Posts
4796Following
319Followers
489OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkoTrying to make a new version of my “TPM2 signers” patch set and stumbling into a weird problem.
Here’s the script I’m looking at:
#!/usr/bin/env bash
set -e
PRIMARY=0x81000001
function egress {
keyctl clear @u
tpm2_evictcontrol -C o -c $PRIMARY 2> /dev/null
tpm2_getcap handles-transient
tpm2_getcap handles-persistent
}
trap egress EXIT
openssl ecparam -name prime256v1 -genkey -noout -out ecc.pem
openssl pkcs8 -topk8 -inform PEM -outform DER -nocrypt -in ecc.pem -out ecc_pkcs8.der
tpm2_createprimary --hierarchy o -G ecc -c owner.txt
tpm2_evictcontrol -c owner.txt $PRIMARY
# EC parameters to TPM2 blob:
tpm2_import -C $PRIMARY -G ecc -i ecc.pem -u tpm2.pub -r tpm2.priv
# TPM2 blob to ASN.1:
tpm2_encodeobject -C $PRIMARY -u tpm2.pub -r tpm2.priv -o tpm2.pem
openssl asn1parse -inform pem -in tpm2.pem -noout -out tpm2.der
# Populate asymmetric keys:
tpm2_ecc_key=`keyctl padd asymmetric "tpm_ecc" @u < tpm2.der`
kernel_ecc_key=`keyctl padd asymmetric "kernel_ecc" @u < ecc_pkcs8.der`
echo "SECRET" > doc.txt
echo TPM2 ECC SIGN
keyctl pkey_sign $tpm2_ecc_key 0 doc.txt hash=sha256 > doc.txt.sig
echo TPM2 VERIFY
keyctl pkey_verify $kernel_ecc_key 0 doc.txt doc.txt.sig
The error message generated is:
keyctl_pkey_verify: Invalid argument
If I verify with the TPM2 ECC key /it will pass, in other words replacing the list statement with:
keyctl pkey_verify $tpm2_ecc_key 0 doc.txt doc.txt.sig hash=sha256
In the final version I’m going to remove signature verification from TPM2 ECC key as that is kind of the point here: sign certificate with a private key protected by TPM and allow any party verify the signature with the known public key.
Jarkko Sakkinen
jarkkohttps://social.kernel.org/notice/AnPuVswNBKAitj9wxc
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoSometimes bad looking solution can have non-intuitive but still legit reasoning - all rotten looking is not actually rotten ;-)
These are at least my empirical learnings over the years working with open source...
Jarkko Sakkinen
jarkko1. A new inline comment
2. A new test case
If you start to seek appropriate places while implementing a feature, that can lead to over-saturation of comments, which dissolves the important ones.
Jarkko Sakkinen
jarkko1. https://lore.kernel.org/linux-integrity/D5CYH0IJXX72.35A25M1YICZRP@kernel.org/T/#u
2. https://bugzilla.kernel.org/show_bug.cgi?id=219383
This bug for early weeks of the current release cycle has already landed: https://bugzilla.kernel.org/show_bug.cgi?id=219229
Right now that I don't do kernel as my main job I prioritize users instead kernel developers when picking fixes for during the cycle PR's :-) Other fixes can wait until 6.13 PR.
#linux #kernel
Jarkko Sakkinen
jarkkoThe next step I'm planning to improve this is adding JTAG probe into it :-) I have one waiting for this already.
Jarkko Sakkinen
jarkkoI don't know what you mean by "green board" and "black board" but this is:
1. VisionQuest 2 RISC-V board
2. A shield providing RS-232 through USB ordered from AliExpress
3. LetsTrust TPM SPI module (Infineon SLB 9672)
I do most of kernel testing in QEMU ATM but this is my bare metal choice because single USB cable gives both power and serial link and board has jumpers to configure it to SDIO mode (i.e. all stages read from provided SD card). RISC-V is a bit irrelevant here but gives confidence that changes work in multiple platforms and not just on x86. And also slowness is a feature for catching performance regressions.
Jarkko Sakkinen
jarkkoThe “convenience of LSP” with kernel:
make ARCH=x86_64 O=../linux-tpmdd-clangd x86_64_defconfig
make O=../linux-tpmdd-clangd/ CC="ccache gcc" -j`nproc`
scripts/clang-tools/gen_compile_commands.py -d ../linux-tpmdd-clangd
This is least distracting way I’ve found to use it (I use it only with VSCodium when just browsing around):
- Uses host architecture (target architecture can be “whatever”).
- Uses defconfig that works well for this task.
- Does not disturb other uses of the Git tree.
E.g. I use LINUX_OVERRIDE_SRCDIR a lot with BuildRoot and usually clean kernel directory in such cases causes least troubles…
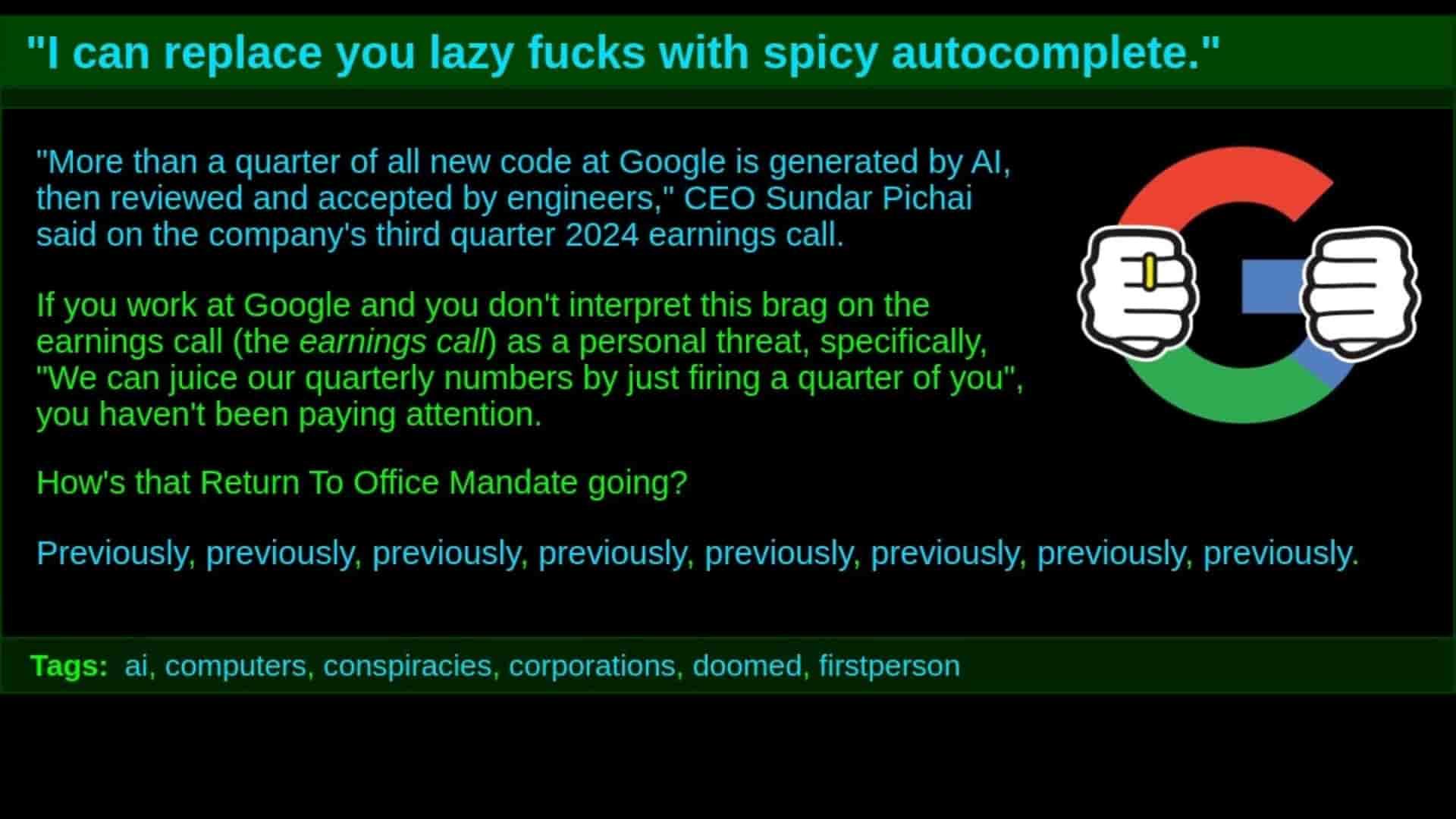
"I can replace you lazy fucks with spicy autocomplete."
"More than a quarter of all new code at Google is generated by AI, then reviewed and accepted by engineers," CEO Sundar Pichai said on the company's third quarter 2024 earnings call. If you work...
https://jwz.org/b/ykb8
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkohttps://lore.kernel.org/linux-integrity/20241102152226.2593598-1-jarkko@kernel.org/T/#t
It's guaranteed race-free (as patch set version does not take ops_sem into account) and for anything security usually it is just only good practice to keep functionality irreversible (one-shot) on success as repetition is bad for security ;-)