Posts
5020Following
329Followers
500OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkko
In Himmelblau evolution it will be interesting to see if there's someday perhaps a subset of graph API to provide "the service' too.
Jarkko Sakkinen
jarkko
@suihkulokki i'm not sure if that page has anything to do with clients. looks like it is related to vms hosted in azure.
Jarkko Sakkinen
jarkko
Cool, got ssh logins through Azure/Intune working to built Ms after fighting for some time with systemd-creds :-) Himmelblau 2.0 feels surprsingly stable environment.
Jarkko Sakkinen
jarkko
This is how wrap get_compile_commands.py:
https://gist.github.com/jarkkojs/00d4fb05474d00bd64df51b4b0028a3b
Sometimes I feel that this should be made somehow a bit more convenient :-)
https://gist.github.com/jarkkojs/00d4fb05474d00bd64df51b4b0028a3b
Sometimes I feel that this should be made somehow a bit more convenient :-)
Jarkko Sakkinen
jarkko
One bottleneck in HMAC encryption that would be easy to solve if TPMKey ASN.1 format would store 'parentPublic', or alternatively 'parentPublicName'.
HMAC encryption requires "extra" TPM2_ReadPublic per unseal transaction because it cannot be stored to the key data.
If it had the field it would be trivial to calculate cryptographic name for the parent object without roundtrip to TPM2 chip when the key is used after creation.
I.e. it is classic value not cached that would be constantly required.
RT @Foxboron
HMAC encryption requires "extra" TPM2_ReadPublic per unseal transaction because it cannot be stored to the key data.
If it had the field it would be trivial to calculate cryptographic name for the parent object without roundtrip to TPM2 chip when the key is used after creation.
I.e. it is classic value not cached that would be constantly required.
RT @Foxboron
Jarkko Sakkinen
jarkko
3rd PR for 6.19: https://lore.kernel.org/linux-integrity/aSthHCovbsDZANsa@kernel.org/T/#u
at least i'm on schedule this time :-)
at least i'm on schedule this time :-)
Jarkko Sakkinen
jarkkoThis is how I manage my pull requests ATM (creating and pushing signed tags, request-pull etc.):
https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/linux-pull-request.git/tree/?h=main
I’m happy with the tiny jq based templating engine for moustache templates. Has worked surprisingly well.
Jarkko Sakkinen
jarkko
Edited 12 days ago
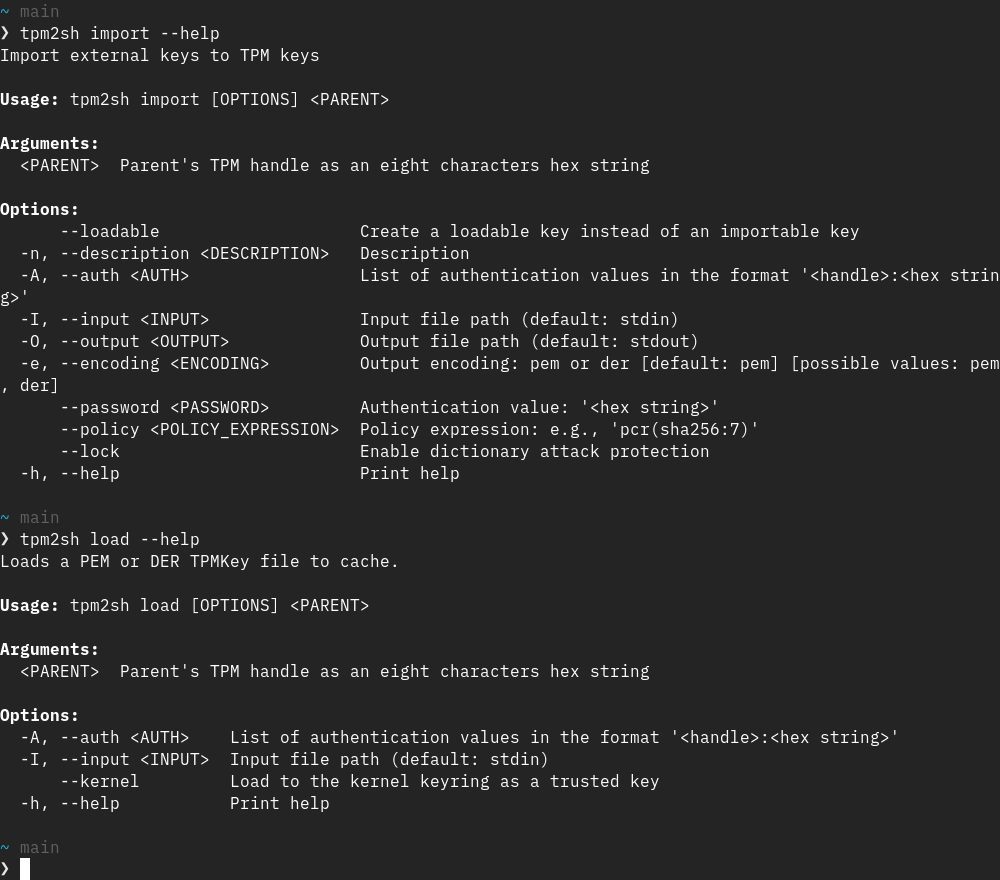
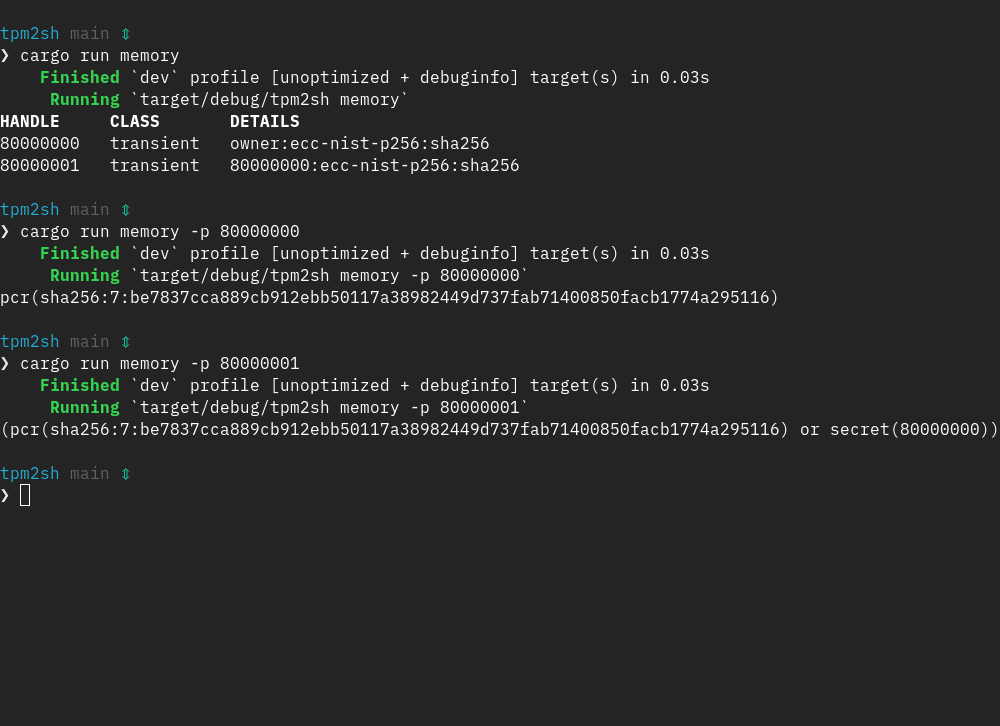
I've been fine-tuning the policy and caching engine in tpm2sh a lot and next version will allow to:
1. View policy as an expression via 'tpm2sh memory -p <handle>'
2. Create primary keys with arbitrary policies (was not just done nothing special in it).
3. Creating, viewing and maintaining policies for persistent keys.
These sort of come as "side-effect" of just cleaning up and polishing the groundwork :-)
#linux #tpm #rustlang
1. View policy as an expression via 'tpm2sh memory -p <handle>'
2. Create primary keys with arbitrary policies (was not just done nothing special in it).
3. Creating, viewing and maintaining policies for persistent keys.
These sort of come as "side-effect" of just cleaning up and polishing the groundwork :-)
#linux #tpm #rustlang
Jarkko Sakkinen
jarkko
What are known good workarounds with systemd-creds for situations like this:
https://github.com/himmelblau-idm/himmelblau/issues/901
I can admit that I don't really know what I'm doing ATM :-)
#systemd
https://github.com/himmelblau-idm/himmelblau/issues/901
I can admit that I don't really know what I'm doing ATM :-)
#systemd
Jarkko Sakkinen
jarkko
Edited 13 days ago
@Foxboron @achilleas I have defacto answer for question four: https://www.joelonsoftware.com/2000/04/06/things-you-should-never-do-part-i/
Jarkko Sakkinen
jarkko
@Foxboron Full spam thread summarized: https://github.com/tpm2-software/tpm2-openssl/issues/120#issuecomment-3583885470
:-)
:-)
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkko
@Foxboron OK that is great. Once there is a IETF draft I don't consider it as a Microsoft proprietary product :-)
As a disclaimer, it's not that I would necessarily want to comment on that. I rather adapt and perhaps workaround key spec in my implementation that proactively drive it because it is simply not my thing :-) This is what happend with parentPublic as cache internally handles it. However, as a maintainer I feel safer to accept change if a key type is driven by a real spec, which is not the case with TPMKey ASN.1 definition (YET).
As a disclaimer, it's not that I would necessarily want to comment on that. I rather adapt and perhaps workaround key spec in my implementation that proactively drive it because it is simply not my thing :-) This is what happend with parentPublic as cache internally handles it. However, as a maintainer I feel safer to accept change if a key type is driven by a real spec, which is not the case with TPMKey ASN.1 definition (YET).