Posts
4823Following
321Followers
487OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
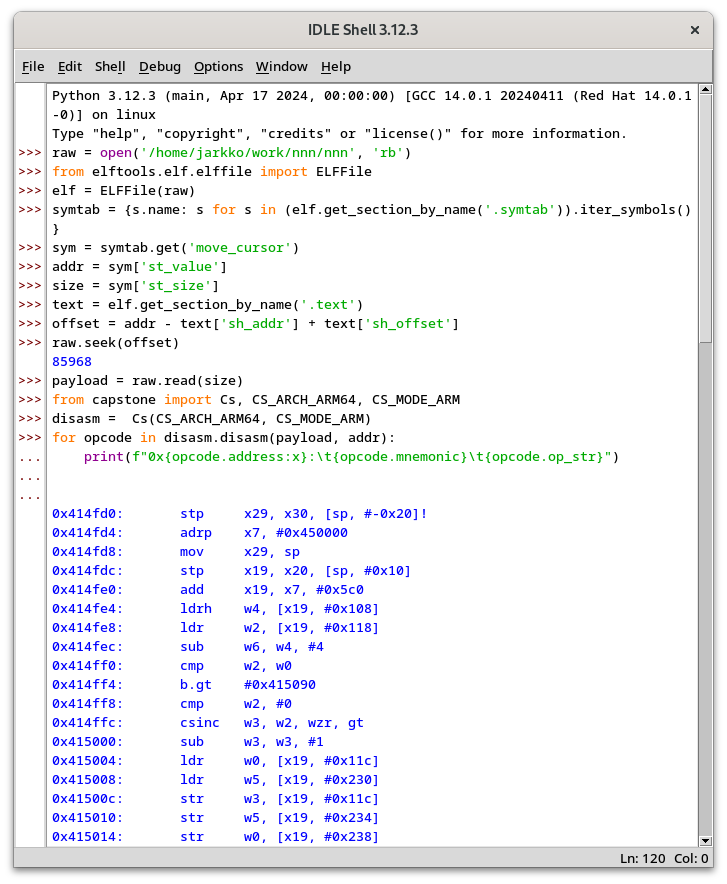
jarkkoIf #Radare2 vs #Rizin makes no sense to you, perhaps #Python will. It is pretty solid tool for driving #Capstone :-)
Transcript:
raw = open('/home/jarkko/work/nnn/nnn', 'rb')
from elftools.elf.elffile import ELFFile
elf = ELFFile(raw)
symtab = {s.name: s for s in (elf.get_section_by_name('.symtab')).iter_symbols()}
sym = symtab.get('move_cursor')
addr = sym['st_value']
size = sym['st_size']
text = elf.get_section_by_name('.text')
offset = addr - text['sh_addr'] + text['sh_offset']
raw.seek(offset)
payload = raw.read(size)
from capstone import Cs, CS_ARCH_ARM64, CS_MODE_ARM)
disasm = Cs(CS_ARCH_ARM64, CS_MODE_ARM)
for opcode in disasm.disasm(payload, addr):
print(f"0x{opcode.address:x}:\t{opcode.mnemonic}\t{opcode.op_str}")
Just got a bit familiar this. The main benefits are obviously:
- Recursive traversal #disassembly (vs linear sweep style in
objdump) - Re-usable analysis
- No boundaries how you can post-process the analysis (or visualize it)
I find this super fascinating!
Jarkko Sakkinen
jarkkoAfter reading #Ueber’s post about their use of #Zig, I tried it to random C and C++ projects:
export CC="zig cc"
export CXX="zig c++"
make
At least for relatively small projects such as nnn this seems to result working results. Still quite impressive. Next iteration would to replace Makefile with build.rs.
Also one tool that I like, ncdu, has successfully executed such conversion: https://dev.yorhel.nl/ncdu
I think I’ll try Linux with tinyconfig next by using this hacky script as basis next:
#!/usr/bin/env bash
set -e
make defconfig
scripts/config --set-str CONFIG_INITRAMFS_SOURCE "initramfs.txt"
yes '' | make oldconfig
cat > initramfs.txt << EOF
dir /dev 755 0 0
nod /dev/console 644 0 0 c 5 1
nod /dev/loop0 644 0 0 b 7 0
dir /bin 755 1000 1000
slink /bin/sh busybox 777 0 0
file /bin/busybox initramfs/busybox 755 0 0
dir /proc 755 0 0
dir /sys 755 0 0
dir /mnt 755 0 0
file /init initramfs/init.sh 755 0 0
EOF
mkdir initramfs
curl -sSf https://dl-cdn.alpinelinux.org/alpine/edge/main/x86_64/busybox-static-1.36.1-r25.apk | tar zx --strip-components 1
cp busybox.static initramfs/busybox
cat > initramfs/init.sh << EOF
#!/bin/sh
mount -t proc none /proc
mount -t sysfs none /sys
sh
EOF
It is from my old’ish post: https://social.kernel.org/notice/AgzHqrYFGplZuYr3gG
Phoronix
phoronix@masto.aiPipeWire 1.2 Released With Async Processing, Explicit Sync & Other Features
PipeWire 1.2 was christened today as the latest major feature update to this solution common to the modern Linux desktop for managing audio/video streams...
https://www.phoronix.com/news/PipeWire-1.2-Released
Jarkko Sakkinen
jarkkorpm -qpR signal-desktop-7.13.0.aarch64.rpm
/bin/sh
/bin/sh
at-spi2-core
gtk3
libXScrnSaver
libXtst
libnotify
libuuid
nss
rpmlib(CompressedFileNames) <= 3.0.4-1
rpmlib(PayloadFilesHavePrefix) <= 4.0-1
rpmlib(PayloadIsXz) <= 5.2-1
xdg-utils
I don’t get the #xscreensaver dependency that #Signal has…
Jarkko Sakkinen
jarkkoJust an observation but if considering testing ARM64-Linux, Apple is actually a “budget choice” compared to:
- Low-volume Linux ARM64 laptops (few available).
- ARM64 server racks.
Especially if you take -1 gen Apple hardware, which you can get for bargain prices pre/post the next WWDC ;-) The laptop seen in previous screenshot is M1 Pro, and it is quite nice and fast , and that is even -2 gen.
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoUseful #kernel feature for #hibernate might be a file that would tell the number of pages required for hibernate.
The "O-figure" for hibernate is AFAIK O(n+sqrt(n)) but exact number is dependent on kernel internals but in theory could be calculated by simulating the process without committing.
Instead of swap it might also be useful to have "spare" volume of ~100 GB for doing hibernate and e2scrub type of operations, which could have its own design for encryption etc. Swap for swapping overcommitted memory more than few at most GiB is not that useful these days.
#linux
Jarkko Sakkinen
jarkkoOn the bright side, it means that US has no age racism I guess then 🤷
Marcus "MajorLinux" Summers
majorlinux@toot.majorshouse.comI feel like if you are going to take time to talk to Tucker Carlson, you deserve everything that's about to come to you.
I do, however, hope nothing happens to the users.
Telegram says it has 'about 30 engineers'; security experts say that's a red flag | TechCrunch
https://techcrunch.com/2024/06/24/experts-say-telegrams-30-engineers-team-is-a-security-red-flag/
Jarkko Sakkinen
jarkko1. Guantanamo Bay
2. ADX Florence
This is not same as saying that I would fully support all the choices and values of the person in question.
Jarkko Sakkinen
jarkkoAnyway, congrats to Mr Tanenbaum, well deserved! Only thing that surprises me is that why he did receive ACM award earlier than this.
https://vu.nl/en/news/2024/andrew-s-tanenbaum-receives-acm-software-system-award
#minix #linux #acm
Phoronix
phoronix@masto.aiNUMA Emulation Yields "Significant Performance Uplift" To Raspberry Pi 5
Engineers at consulting firm Igalia are exploring NUMA emulation for ARM64 (AArch64) due to the potential of "significant" performance uplift as observed on the popular Raspberry Pi 5 single board computer...
https://www.phoronix.com/news/ARM64-NUMA-Emulation-RPi5
Jarkko Sakkinen
jarkkoFor me it feels sometimes that quite many commercial web sites reached their tip point maybe about 10-12 years ago. Since then they've started to add stuff that I don't want, and sometimes even quite controversial features, which I need to then proactively disable.
It's a bit same as with yogurt based food products. Yogurt is a product that does not really develop anymore but still food companies have new versions of this product for every season with supplements added and stuff like that.
So I guess I can draw the conclusion that commercial web reached the "yogurt state" around 2012 :-)
Jarkko Sakkinen
jarkkoWould it be unorthodox for sbsign to use kernel crypto API (optionally) instead of OpenSSL?
One use case for this would be MOK private key that is encrypted while at rest with TPM, and never exposed to CPU.
This would be a great application for the kernel feature that I’m working on i.e. an asymmetric TPM2 key (patch set is slowly getting together, right now at iteration seven).
Just to name an example, this is how Ubuntu manages that key as of today: https://wiki.ubuntu.com/UEFI/SecureBoot/Signing. [for the record, Ubuntu is not doing worse job in this than anyone else, they just have awesome documentation, thus the example]
Jarkko Sakkinen
jarkkosq is #openpgp implementation: https://sequoia-pgp.org/
I wonder if sequoia can git tag -s?
Also need to test if smartcard support is already working https://sequoia-pgp.org/blog/2021/12/20/202112-openpgp-card-ci/
And most importantly has a gpg-agent implementation: https://lib.rs/crates/sequoia-gpg-agent. But have to check how stable that is.
These three are minimum set of features that any OpenPGP implementation needs to fully support in order to be compatible with kernel development workflows.