Posts
5116Following
331Followers
505OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkohttps://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git/commit/?id=f5e0e82aaad3135be73c3f7a35aaec08e78cfe7c
I.e. if a command or response acts weird the dump can be put either "response.txt" or "command.txt" and roundtrip parse-build-compare will be peformed when running either "cargo test" or "make test".
Jarkko Sakkinen
jarkkohttps://lore.kernel.org/tpm-protocol/20250902165455.3680143-1-jarkko@kernel.org/
Fixed in https://crates.io/crates/tpm2-protocol/0.10.21
Once MockTPM is mature enough I use it also as the unprivileged default backed for tpm2sh.
That enabled two useful features:
1. Dry-run TPM operations with tpm2sh against swTPM with support also for e.g. persistence.
2. Windows and macOS support! They just compile out device parameter and use MockTPM unconditionally.
#linux #rust #tpm
Jarkko Sakkinen
jarkkoI have now a single unified expression language in tpm2sh, which is used in all PCR and policy commands.
You can e.g., express crazy things like or(pcr("sha256:0"), secret(tpm://0x40000001)) with it for instance.
I’ve replaced three separate pest parsers with a single unified nom parser. So much manual control was required anyhow so that diff was pretty much +- 0.
Jarkko Sakkinen
jarkkohttps://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git/commit/?h=queue&id=4efa57b484039b8fa9fb41b647b11b623e60fcde
I actually had to re-learn partly how my own software works but it all looks like fairly sound and logical to me :-) Was a good mental exercise really.
#linux #rust #tpm
Jarkko Sakkinen
jarkkoHad to do the cli extremely wrong, unintuive and pain to maintain to discover what would be actually right in this case. No one has really ever though how to make TPM2 nice to use from command-line so this part of the process :-)
Jarkko Sakkinen
jarkkohttps://bsky.app/profile/linuxfoundation.org/post/3lxu6seyxzc2m
Jarkko Sakkinen
jarkkoIn the current stable (0.10.x) memory interaction can be broken down as follows:
1. There is no internal buffering, meaning that internal state does not consume stack.
2. The result is stored in stack.
In the next version (0.11.x) the memory semantics reduce into:
1. Like in the previous version no internal buffering.
2. There's neither parsing nor building. The macros generate a set of interfacs and all parts can be observed with a set of macro generated traits. This builds on the foundation of the DSL developed for describing TCG specs.
I.e. absolutely minimum requirements to run it are:
1. ROM
2. CPU or microcontroller with reasonable register space.
Jarkko Sakkinen
jarkkoNow that I don't do active development on tpm2-protocol, I'm going to make the first actually somewhat stable 0.11.0 release of tpm2sh.
It has quite verbose interface, which will break also easily for that reason. Thus, before pursuing seriously to the possible bugs, I developed MockTPM, a simple TPM emulator that is used as the "TPM end" for subcommand integration tests..,
#linux #kernel #rust #tpm
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoWith TPM protocol shenanigans people tend to go generation path because writing all data types manually would be ridiculous amount of work.
By creating DSL with macros, "ridiculous" factored down to "huge" but only for the initial pass i.e., to reach the current TCG standard version. And given that I have now efficient DSL, keeping the implementation up to date is almost cost-free. And since none of the compiled code is a generation artifact, it is easy to "shift away" in selected places, and write down traits manually.
Jarkko Sakkinen
jarkkoI’m working on a bash and Makefile based project called “himmelblau-dev”, which provides low-barrier entry point to start contributing to that upstream project. I have not really contributed to that project much because there is no a meaningful edit-compile-run-cycle and that is what I’m resolving with this project.
I’ve taken a lot of trouble to not use containers, not even in the build, because containers always mean looking for problems when translating a development environment from one machine to another.
[To be completely honest, for any possible project I interpret “I have to use a container” into “my solution is going to be a trainwreck”]
Instead, I do the build with a combination of deboostrap and guestfish tricks. The project has makefile targets for running resulting QCOW2 in QEMU, contains a settings file (parser implemented in bash) and automatic download of OVMF images and logic for managing EFI vars file.
It’s a bit like embedded build system centered around a single upstream project.
Layout right now:
❯ tree
.
├── bootstrap
│ ├── settings.sh
│ └── start.sh
├── config
│ ├── debian.sh
│ ├── himmeblau.sh
│ └── start.sh
├── himmelblau.version
├── Makefile
├── qemu.json
├── README.md
└── vm
├── qemu.sh
├── start.sh
└── swtpm.sh
I need to fine-tunet his for a while still before I publish it. It’s all GPL3 license as I see no point of using any other license for this.
qemu.json is just my own ad-hoc VM configuration format:
{
"args": {
"enable-kvm": true,
"machine": "q35,accel=kvm",
"cpu": "host",
"memory": "4G",
"rtc": "base=localtime"
},
"networking": {
"user": [
{ "netdev": "user,id=net0,hostfwd=tcp::10022-:22" },
{ "device": "virtio-net-pci,netdev=net0" }
],
"bridge": [
{ "netdev": "bridge,id=net0,br=br0" },
{ "device": "virtio-net-pci,netdev=net0" }
]
},
"tpm": {
"enabled": true,
"tpmdev": "emulator,id=tpm0,chardev=chrtpm",
"device": "tpm-tis,tpmdev=tpm0"
},
"drives": [
{
"if": "pflash",
"file": "OVMF_CODE.fd",
"format": "raw",
"readonly": "on"
},
{
"if": "pflash",
"file": "OVMF_VARS.fd",
"format": "raw"
},
{
"file": "himmelblau-demo.qcow2",
"format": "qcow2"
}
]
}
Jarkko Sakkinen
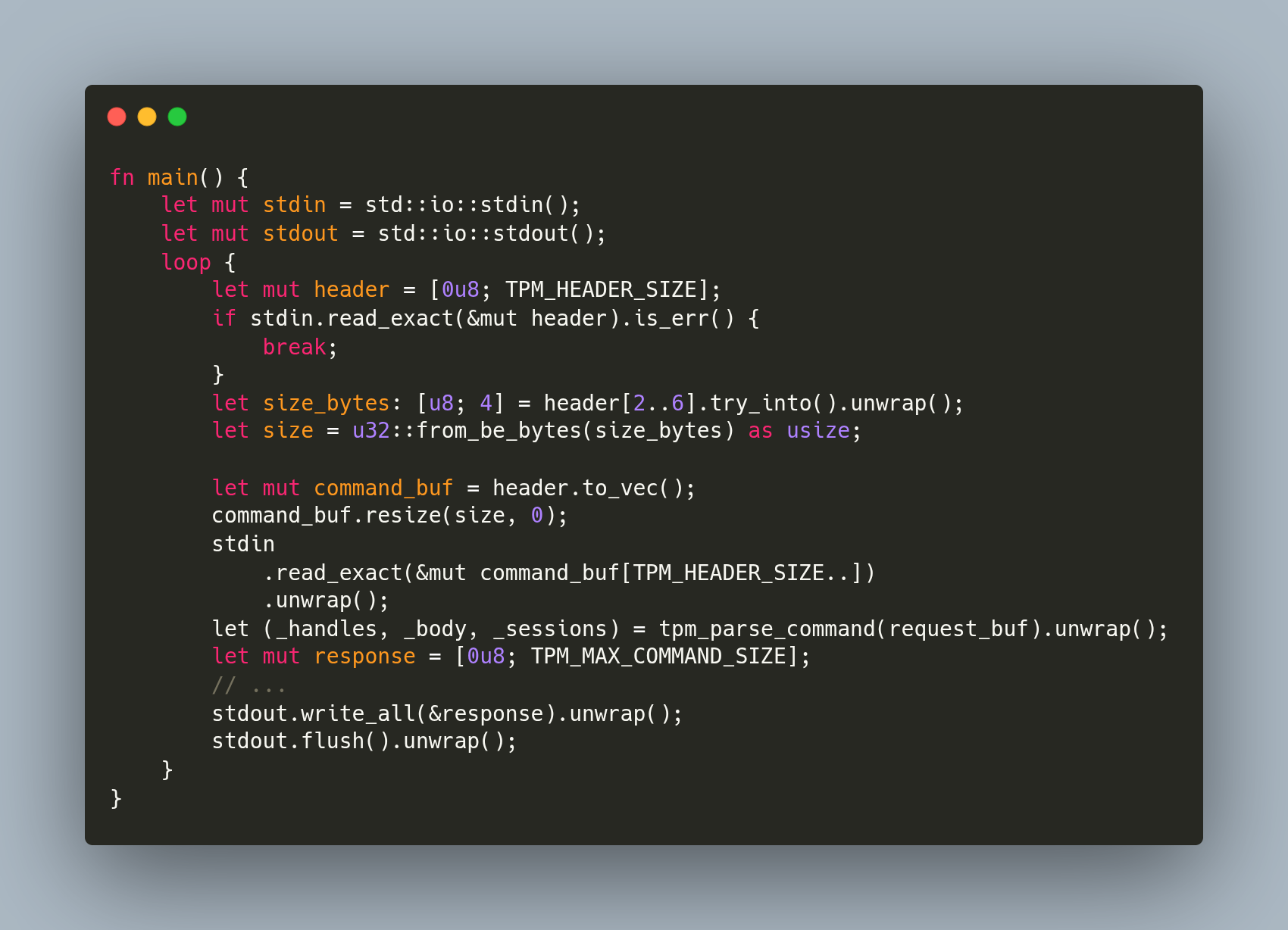
jarkkohttps://github.com/puavo-org/tpm2sh/blob/main/src/bin/mock-tpm.rs
Even at this point it still demonstrates how easy it is to get ongoing with previously as complicated task as writing a TPM emulator.
#linux #kernel #tpm #rust
Jarkko Sakkinen
jarkkoPatches and discussion: tpm-protocol@lists.linux.dev
More information: https://git.kernel.org/pub/scm/linux/kernel/git/jarkko/tpm2-protocol.git/tree/README.md
#linux #kernel #tpm #rust
Jarkko Sakkinen
jarkkoOnce I land the fix for ATM broken tpm2sh import, I'll also add tests/commands.rs, which will demonstrate how you can use tpm2-protocol crate to mock the TPM device.
If you want to take the test to the device level, tpm_vtpm_proxy can be used for this purpose (a driver by Stefan Berger who has also created the awesome swtpm, which is *obviously* the ultimate solution with QEMU) .
#linux #kernel #tpm #rust