Posts
350Following
95Followers
3908Greg K-H
gregkhYear Reserved Assigned Rejected Total
2019: 47 2 1 50
2020: 37 13 0 50
2021: 45 205 0 250
2022: 45 5 0 50
2023: 51 145 4 200
2024: 502 48 0 550
Total: 727 418 5 1150
Majority so far is back-filling in from the GSD entries. We've only really done 2-3 stable releases so far, we have a bunch of review to catch up with, you can see the current status in our git repo if people are curious what is being discussed/reviewed.
Greg K-H
gregkhK. Ryabitsev-Prime 🍁
monsieuriconGreg K-H
gregkhGreg K-H
gregkhGreg K-H
gregkhThey have a strong "Get your changes upstream first" rule with their OEMs and you can see the interactions with those companies uptream has increased dramatically over the past years been because of this.
ChromeOS portion of Google also has a strong "upstream first" rule, and is very good about taking updates and getting changes merged properly.
The Pixel out-of-tree stuff is due to other "reasons", but that is a separate division and there have been many patch submissions recently upstream to resolve that delta, so that is being whittled down.
Greg K-H
gregkhGreg K-H
gregkhGreg K-H
gregkh@kernellogger Your data is going to be a bit skewed here, we have ONLY processed the v6.7..v6.7.1 and most of the v6.7.1..v6.7.2 commits so far for CVE-related stuff, which by far the majority have only Fixes: tags due to my travel schedule during those releases (i.e. I didn’t have the cycles to catch up with the cc: stable@ tagged commits. I bet the numbers will level out over time as we catch up with the rest of the commits in the v6.7.Y releases.
And it’s good to see people paying attention, thank you!
Thorsten Leemhuis (acct. 1/4)
kernellogger@fosstodon.orgDid a quick *rough* check:
* 65 #Linux #kernel CVE announcements from Greg so far
* 55 of those refer to a mainline commit
* 10 of those were marked for backporting to stable/longterm
And that's why Greg backports a lot of #LinuxKernel mainline commits to stable/longterm that are *not* tagged for backporting -- and why "only backport changes mainline developers[1] tagged for backporting" is a bad idea.
[1] reminder, such tagging is optional, as participation in stable/longterm is optional
Greg K-H
gregkhGreg K-H
gregkhsjvn
sjvn@mastodon.socialThe #Linux kernel developers are now issuing their own, more accurate Common Vulnerabilities and Exposures #security bulletins. https://opensourcewatch.beehiiv.com/p/linux-gets-cve-security-business by @sjvn
The Linux kernel developers are now in charge of its Common Vulnerabilities and Exposures (CVE) security problems.
lcamtuf 


lcamtuf@infosec.exchange
Computer folks, remember the precedence of operators! Consult this handy list if in doubt:
() [] -> .
! ~ ++ --
* / %
+ -
<< >>
< <= > >=
== != &=
=== &&& |||
?: ??= ( ^..^)ノ
(╯°□°)╯︵ ┻━┻
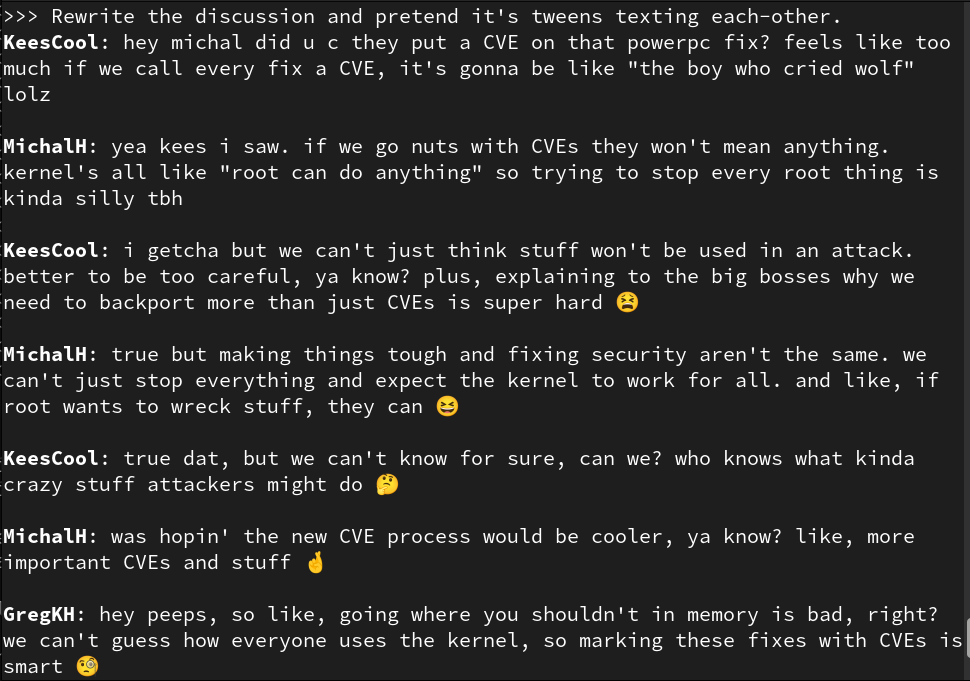
Kees Cook (old account)
kees@fosstodon.orgv6.5 fixed almost twice as many "high" CVEs (19) than the second most prolific release, v6.6 (11), with v6.4 & v5.17 tied for 3rd place (9). It seems like the rate of fixing is picking up.
Ignoring the first git release (v2.6.12), the "high" flaw introduction counts are relatively even. Highest (i.e. most well tested/researched) releases have been v3.8 (9), v3.18 & v2.6.20 tied (8), and v5.9 & v4.1 tied (6).
But certainly more flaws are in all releases -- they just haven't been found yet.