Posts
350Following
95Followers
3923Greg K-H
gregkhIt's a fun thread, recommended for anyone who deals with compilers and trying to get them to do what you would think would be a "easy" thing to do and the hacks around them to get them to do that (hint adding "+ 0" to an expression tricks the compiler into doing what you meant it to do is usually a sign that something is wrong somewhere...)
Mike Dolan
mdolan@fosstodon.org"Census III of Free and #OpenSource Software: Application Libraries leans on more than 12M data points from security tools such as Black Duck, FOSSA, Snyk, and Sonatype, which have been deployed at more than 10k companies"
https://techcrunch.com/2024/12/04/linux-foundation-report-highlights-the-true-state-of-open-source-libraries-in-production-apps/ #cybersecurity
Greg K-H
gregkhhttps://lore.kernel.org/lkml/2024120520-preorder-untracked-6e5b@gregkh/T/
Please move to a more modern kernel if you are somehow still running this one, which I strongly would not recommend doing.
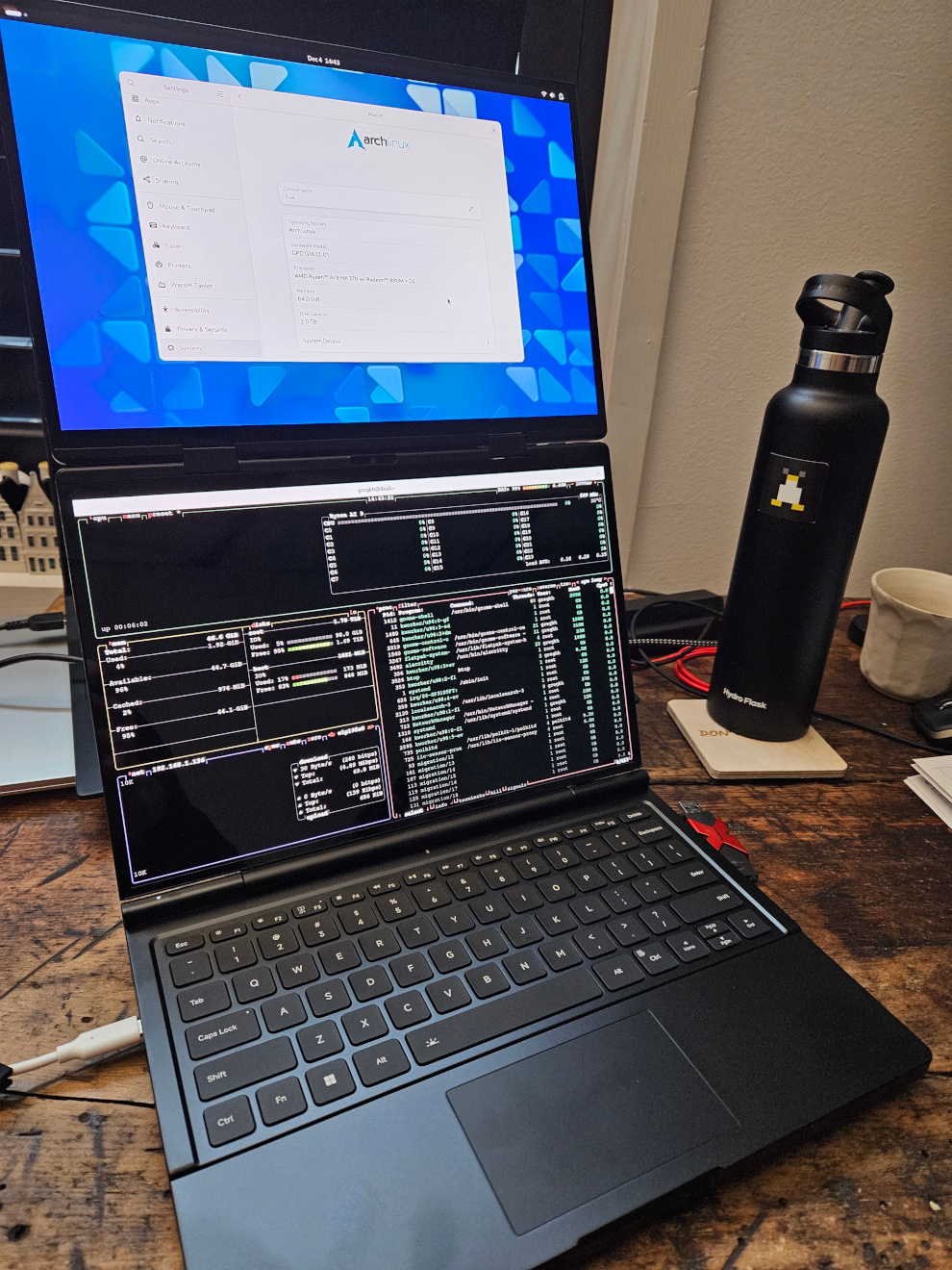
Greg K-H
gregkhWater bottle for scale.
Jens Axboe
axboe@fosstodon.orgIn today’s news: man with zero self reflection goes on lengthy one sided rant highlighting just that.
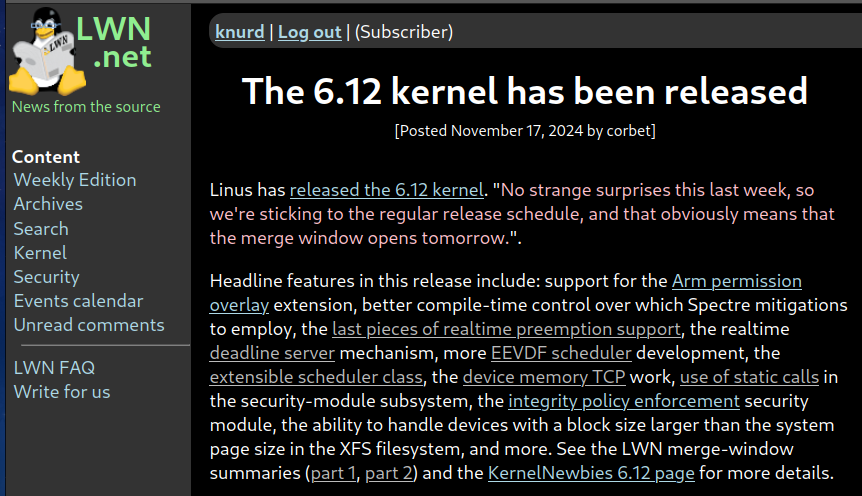
Thorsten Leemhuis (acct. 1/4)
kernellogger@fosstodon.org#Linux 6.12 is out. For a list of new features see:
* This short LWN story: https://lwn.net/Articles/997958/ (screenshotted)
* Two detailed stories from LWN: https://lwn.net/Articles/990750/ & https://lwn.net/Articles/991301/
* The kernelnewbies page: https://kernelnewbies.org/Linux_6.12
See also the announcement from @torvalds:
https://lore.kernel.org/lkml/CAHk-=wgtGkHshfvaAe_O2ntnFBH3EprNk1juieLmjcF2HBwBgQ@mail.gmail.com/
'"No strange surprises this last week, so we're sticking to the regular release schedule, and that obviously means that the merge window opens tomorrow."'
Greg K-H
gregkh{sigh} Go home CodeQL, you are drunk…
int main(int argc, char *argv[])
Poorly documented function: fewer than 2% comments for a function of 129 lines.
Code in question is at: https://github.com/gregkh/usbutils/blob/master/lsusb.c#L3835 if people are curious. It’s as if the tool hasn’t seen C code before…
Greg K-H
gregkhFor the usbutils project, developers have helpfully set up a bunch of github actions to help with build tests and the like, and it also includes github's "security scanning" toolsets. Unfortunately the output of such tools is pretty useless and unhelpful to a fault.
Example, this "result": https://github.com/gregkh/usbutils/security/code-scanning/2291
which claims "short global name" yet there is no such actual global variable `i` in the codebase at all.
Because of stuff like this, the tools "claim" there are 63 "security" issues in the usbutils project. Since when did using single character names become a security issue, even if we were doing that, but ok...
So, how to turn this off, or better yet, fix the test to not report issues that are actually in the tests themselves?
Thorsten Leemhuis (acct. 1/4)
kernellogger@fosstodon.org#usbutils (which contains lsusb and the more modern lsusb.py) 018 is out:
https://lore.kernel.org/all/Zxd0oZefuehqhA7z@kroah.com/
@gregkh writes:
'"For users, the largest change will be that the '-v' option to lsusb will now show the negoitated speed of the device on the bus […], and there is better handling for new device descriptor fields and information in the '-v' output as well."'
Eric A. Meyer
Meyerweb@mastodon.socialSo… O’Reilly sent me email today hyping up how my books (really, just the one, I assume) is going to be AI-translated into Spanish and German, with other languages to follow. This was probably inevitable, but I still have concerns.
First: are there no human translators of these languages?
Second: who’s going to proof-read all 1,126 pages to make sure nothing got botched, especially given the technical nature of the content? The readers? Which isn’t even crowd-sourcing: it’s customer-sourcing.
Greg K-H
gregkhBut no way is it better than an email-based review workflow, whereby I can just tear through hundreds of patches in a very short amount of time, all while sitting behind a very slow/laggy internet connection, or totally disconnected (i.e. better for distraction-free work).
As almost no other project is at the rate of change or size of the Linux kernel, gerrit might be wonderful for your smaller one. But for ones that are our size, realize that centralized workflows like gerrit and the like just do not scale at all.
Programming Quotes
programming_quotes@mastodon.socialEvery language has an optimization operator. In C++ that operator is //'
K. Ryabitsev-Prime 🍁
monsieuriconLennart Poettering
pid_eins@mastodon.socialIn systemd we started to do more and more Varlink IPC (instead of or 9n addition to D-Bus), and you might wonder what that is all about. In this AllSystemsGo talk I try to explain things a bit, enjoy: https://media.ccc.de/v/all-systems-go-2024-276-varlink-now-
I'm at Kernel Recipes 2024, starting the live blog now https://kernel-recipes.org/en/2024/category/live-blog/
Day 1 Morning: https://kernel-recipes.org/en/2024/2024/09/18/live-blog-day-1-morning/
Have offered to help (or at least be cc'd in hopes I have time for it :) on mm binding stuff fwiw from the kernel side.
And also I really do have to sit down with rust finally... Maybe advent of code this year...
Steven Rostedt
rostedtTHIS IS IT!!!
The last hurdle for PREEMPT_RT being merged into mainline has just removed by this pull request. Leaving the door open for PREEMPT_RT to be added to 6.12!
Kees Cook (old account)
kees@fosstodon.org"Defects-in-Depth: Analyzing the Integration of Effective Defenses against One-Day Exploits in Android Kernels" is a great read:
https://www.usenix.org/system/files/usenixsecurity24-maar-defects.pdf
"integrating defense-in-depth mechanisms from the mainline Android kernel could mitigate 84.6% of these exploitation flows"
h/t @rene_mobile
@IAIK