Posts
4675Following
319Followers
484OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkko@vbabka @sl My favorite call is fallocate() with FL_PUNCH_HOLE flag ;-) With just fallocate() and mmap() fairly complex memory management can be implemented.
Everyone’s favorite gpg-agent demonstrates pretty well vsz/rss ratio:
main 21s
❯ ps -h -p "`pidof gpg-agent`" -o pid,comm,vsz,rss
PID COMM VSZ RSS
3739 gpg-agent 410782624 2480
For the sake of example this was executed in macOS (and for the record, numbers are KiB).
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoQuite amazing.
[1] https://www.uber.com/en-FI/blog/bootstrapping-ubers-infrastructure-on-arm64-with-zig/ #ueber #zig
Jarkko Sakkinen
jarkko@ljs @lkundrak @pony i love its flat and ugly config file, much faster to edit than the modern yaml/toml pollution ;-)
$ cat .config/kitty/kitty.conf
include current-theme.conf
font_family MesloLGM Nerd Font Mono
bold_font auto
italic_font auto
bold_italic_font auto
font_size 12.0
tab_bar_style powerline
tab_powerline_style round
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoI’ll fallback to scripts :-)
Mostly because I want this somewhat rare combination in partioning where LUKS2 is used together with EXT4 and encryption is done without LVM2 layer and swap space huge to allow testing hibernate (especially encrypted hibernate):
!/usr/bin/env sh
set -e
# Partition
sgdisk -Z /dev/nvme0n1
sgdisk -n1:0:+5G -t1:ef00 -c1:EFI /dev/nvme0n1
sgdisk -n2:0:+75G -t2:8200 -c2:secswap /dev/nvme0n1
sgdisk -N3 -t3:8304 -c3:secroot /dev/nvme0n1
partprobe -s /dev/nvme0n1
# Encrypt
cryptsetup luksFormat --type luks2 \
--force-password \
/dev/disk/by-partlabel/secroot
cryptsetup open /dev/disk/by-partlabel/secroot root
cryptsetup open --type plain \
--key-file /dev/urandom \
/dev/disk/by-partlabel/secswap swap
# Initialize swap
mkswap -L swap /dev/mapper/swap
swapon -L swap
# Format
mkfs.fat -F32 -n EFI /dev/disk/by-partlabel/EFI
mkfs.ext4 -L /dev/mapper/root
# Mount
mount /dev/mapper/root /mnt
mount --mkdir /mnt/boot
# Install
pacstrap -K /mnt base base-devel linux linux-firmware amd-ucode intel-ucode lvm2
genfstab -U /mnt >> /mnt/etc/fstab
In the final version TPM2 will unseal the rootfs.
So only intermediate layer in this is dm-crypt. I like how raw and transparent it will become :-) Given trivial filesystem layering and simple rootfs type (ext4) to begin with I can finally have single unified configuration for both my hosts and vm guests. And maximum transperency for debugging given tons of tools to debug ext4.
Jarkko Sakkinen
jarkkoI’ll fallback to scripts :-)
Mostly because I want this somewhat rare combination in partioning where LUKS2 is used together with EXT4 and encryption is done without LVM2 layer and swap space huge to allow testing hibernate (especially encrypted hibernate):
!/usr/bin/env sh
set -e
# Partition
sgdisk -Z /dev/nvme0n1
sgdisk -n1:0:+5G -t1:ef00 -c1:EFI /dev/nvme0n1
sgdisk -n2:0:+75G -t2:8200 -c2:secswap /dev/nvme0n1
sgdisk -N3 -t3:8304 -c3:secroot /dev/nvme0n1
partprobe -s /dev/nvme0n1
# Encrypt
cryptsetup luksFormat --type luks2 \
--force-password \
/dev/disk/by-partlabel/secroot
cryptsetup open /dev/disk/by-partlabel/secroot root
cryptsetup open --type plain \
--key-file /dev/urandom \
/dev/disk/by-partlabel/secswap swap
# Initialize swap
mkswap -L swap /dev/mapper/swap
swapon -L swap
# Format
mkfs.fat -F32 -n EFI /dev/disk/by-partlabel/EFI
mkfs.ext4 -L /dev/mapper/root
# Mount
mount /dev/mapper/root /mnt
mount --mkdir /mnt/boot
# Install
pacstrap -K /mnt base base-devel linux linux-firmware amd-ucode intel-ucode lvm2
genfstab -U /mnt >> /mnt/etc/fstab
In the final version TPM2 will unseal the rootfs.
So only intermediate layer in this is dm-crypt. I like how raw and transparent it will become :-) Given trivial filesystem layering and simple rootfs type (ext4) to begin with I can finally have single unified configuration for both my hosts and vm guests. And maximum transperency for debugging given tons of tools to debug ext4.
Jarkko Sakkinen
jarkkoafter some sleep i look into getting UKI on top of this:
❯ cat partition.sh
#!/usr/bin/env sh
set -e
# Partition
sgdisk -Z /dev/nvme0n1
sgdisk -n1:0:+512M -t1:ef00 -c1:EFI -N2 -t2:8304 -c2:pv0 /dev/nvme0n1
partprobe -s /dev/nvme0n1
cryptsetup luksFormat --type luks2 --force-password /dev/nvme0n1p2
cryptsetup luksOpen /dev/nvme0n1p2 pv0
cryptsetup luksDump /dev/nvme0n1p2
pvcreate /dev/mapper/pv0
vgcreate vg0 /dev/mapper/pv0
lvcreate -L 80G vg0 -n swap
lvcreate -l 100%FREE vg0 -n root
# Format and mounnt
mkfs.ext4 /dev/mapper/vg0-root
mkswap /dev/mapper/vg0-swap
mount /dev/mapper/vg0-root /mnt
swapon /dev/mapper/vg0-swap
mkfs.vfat -F32 /dev/nvme0n1p1
mount --mkdir /dev/nvme0n1p1 /mnt/boot
Jarkko Sakkinen
jarkkomodern example of https://www.joelonsoftware.com/2001/04/21/dont-let-architecture-astronauts-scare-you/
Jarkko Sakkinen
jarkkoI've seen mostly either luks1-lvm-ext4 topology with passphrase and luks2-btrfs topolgy.
And I'm going to give a shot on luks2-lvm-ext4, which is something I'm also interested to see if it can work properly.
So it is also "for the benefit of the mandkind" ;-) Not listed here: https://wiki.archlinux.org/title/dm-crypt/Encrypting_an_entire_system#LVM_on_LUKS
Have to give up on archinstall achieve this and make a script.
Jarkko Sakkinen
jarkkoNot true. It is just kept relatively small (like 2GB and similar figures) because its main job is these days to provide depth in failure tolerance for near OOM situations.
Back in the day it was for "spare slow memory space", which is of course not applicable anymore.
Except: if hibernation is used it obviously need to be larger than the system memory.
Jarkko Sakkinen
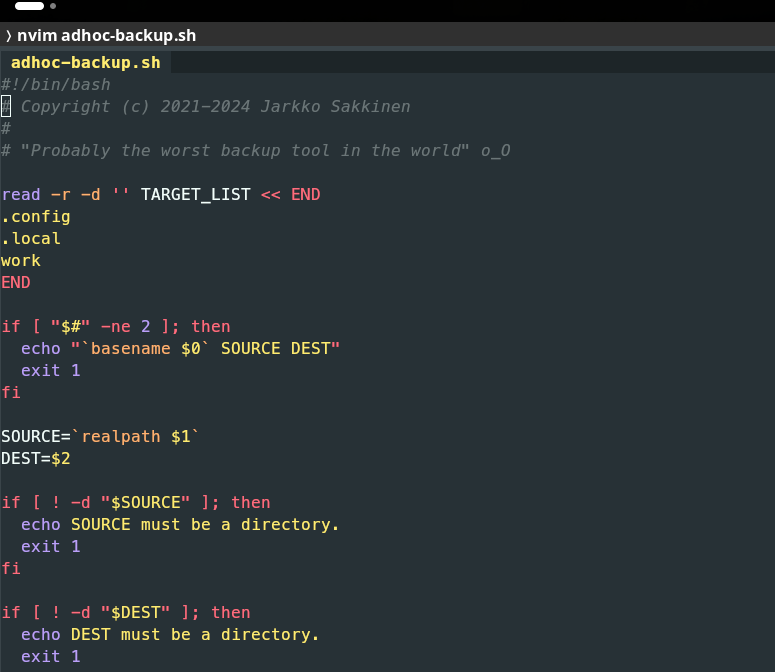
jarkkoneed this for my #btrfs to #ext4 migration 🤷 https://codeberg.org/jarkko/adhoc-backup #git
#codesberg - “Probably the best git hosting in the world”