Posts
5051Following
330Followers
505OpenPGP: 3AB05486C7752FE1
Jarkko Sakkinen
jarkkoFor me it feels sometimes that quite many commercial web sites reached their tip point maybe about 10-12 years ago. Since then they've started to add stuff that I don't want, and sometimes even quite controversial features, which I need to then proactively disable.
It's a bit same as with yogurt based food products. Yogurt is a product that does not really develop anymore but still food companies have new versions of this product for every season with supplements added and stuff like that.
So I guess I can draw the conclusion that commercial web reached the "yogurt state" around 2012 :-)
Jarkko Sakkinen
jarkkoWould it be unorthodox for sbsign to use kernel crypto API (optionally) instead of OpenSSL?
One use case for this would be MOK private key that is encrypted while at rest with TPM, and never exposed to CPU.
This would be a great application for the kernel feature that I’m working on i.e. an asymmetric TPM2 key (patch set is slowly getting together, right now at iteration seven).
Just to name an example, this is how Ubuntu manages that key as of today: https://wiki.ubuntu.com/UEFI/SecureBoot/Signing. [for the record, Ubuntu is not doing worse job in this than anyone else, they just have awesome documentation, thus the example]
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkosq is #openpgp implementation: https://sequoia-pgp.org/
I wonder if sequoia can git tag -s?
Also need to test if smartcard support is already working https://sequoia-pgp.org/blog/2021/12/20/202112-openpgp-card-ci/
And most importantly has a gpg-agent implementation: https://lib.rs/crates/sequoia-gpg-agent. But have to check how stable that is.
These three are minimum set of features that any OpenPGP implementation needs to fully support in order to be compatible with kernel development workflows.
Jarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoJarkko Sakkinen
jarkkoIt even has tool called icat for raw shell.
Jarkko Sakkinen
jarkkosecond, it takes me less time to modify sbsign than mkosi for testing the features in question (e.g. tests tweak mok signing procedure).
sometimes, if you don't have anything constructive to say, it is best to say nothing.
Foone🏳️⚧️
foone@digipres.clubtwo of the best feelings when programming are:
1. figuring out a really clever way to solve a problem
2. figuring out a really stupid way to solve a problem
Paskajärven kaunis Charlotta
menneisyytesi@eliitin-some.fiKun juhannusyönä pistät seitsemän yrttiä ja kukkaa tyynyn alle, niin Kela määrittelee sinut maatalousyrittäjäksi ja näet unta presidentti Väyrysestä
Jarkko Sakkinen
jarkko@pid_eins I was setting up systemd with UKI manually for the first time and mixed up systemd and arch specific configuration :-) So I’m spreading FUD apparently…
Where this spins of has a legit motivation: I’m trying to get my host desktop and VM guests to be in par with latest systemd with UKI kernel so that I can debug keyring and TPM related issues in a relevant environment [1]. I’m co-maintainer for both keyring and TPM, and if you think those kernel subsystems, today systemd is the substantial user for both, and thus a great user space QA target. It is always using the latest stuff that we are delivering.
In arch specific mkinitcpio.conf there’s an array MODULES=(<list of modules>), and all examples I’ve seen put like MODULES(tpm_tis) there. A script (unsurpsingly) called `mkinitcpio then takes that description and includes them to the final initrd. Even being distro specific, that does not calculate tho, I mean any possible use case for TPM requires it to be initramfs (e.g. IMA). It is pretty much a brick unless that is the case :-) So without testing I’d guess that those examples must be wrong and I’ll try first not to add anything to MODULES… Yep, and obviously they are autoloaded, when initramfs has them. [1] https://codeberg.org/jarkko/archest-linux
Threema
threemaapp@mastodon.socialEU Commission: “End encryption!”
Internet users: “End-to-end encryption!”
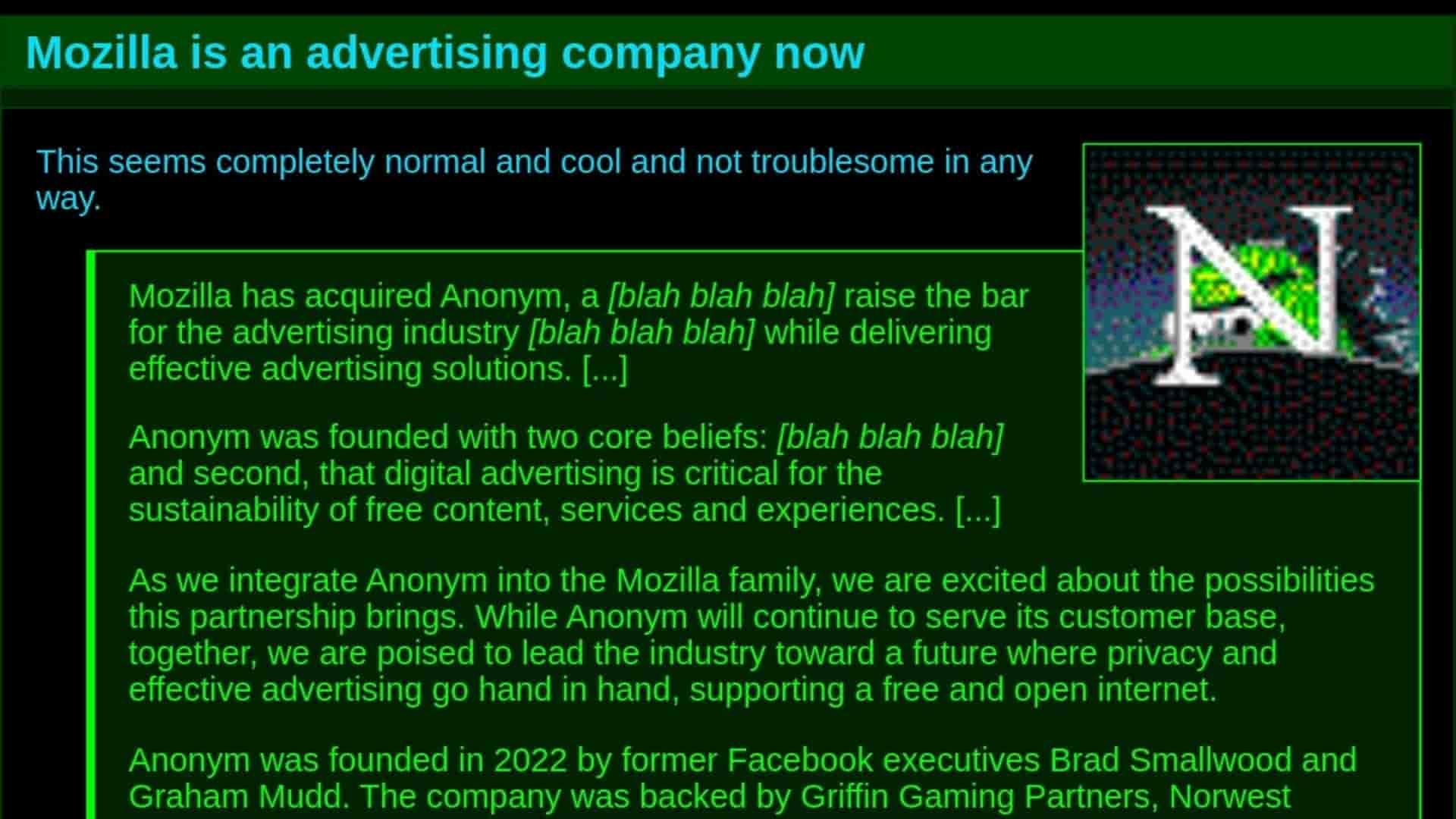
Mozilla is an advertising company now.
This seems completely normal and cool and not troublesome in any way.
Mozilla has acquired Anonym, a [blah blah blah] raise the bar for the advertising industry [blah blah blah] while delivering effective...
https://jwz.org/b/ykVg