Posts
4818Following
319Followers
488OpenPGP: 3AB05486C7752FE1
Krzysztof Kozlowski
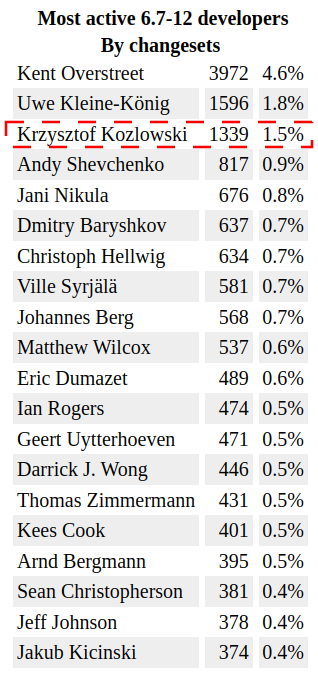
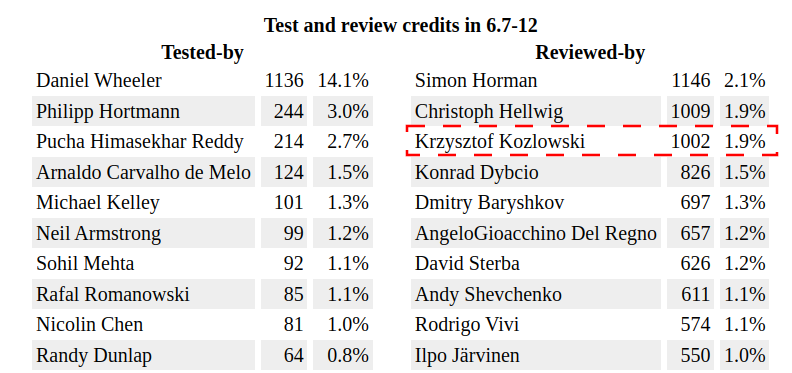
krzkI am however more proud of another impact I made: I am one of the most active reviewers of the last one year of Linux kernel development. Reviewing takes a lot of time, a lot of iterations, a lot of patience, a lot of template answers and results with only "some" of reviewed-by credit going to Linux kernel git history. Yet here I am: ~1000 reviewed-by credits for last year v6.7 - v6.12 Linux kernel.
Source, LWN.net:
https://lwn.net/SubscriberLink/997959/377cf2f076306247/
Jarkko Sakkinen
jarkkoGreat, I made it. Created my own MOK key in Fedora:
$ sudo certutil -d /etc/pki/pesign -L
Certificate Nickname Trust Attributes
SSL,S/MIME,JAR/XPI
Secure Boot Signing Key Pu,Pu,Pu
Steps:
openssl req -config ./MOK.cnf -new -x509 -newkey rsa:4096 -nodes \
-days 36500 -outform DER -keyout "MOK.priv" -out "MOK.der"
sudo certutil -A -i MOK.der -n "Secure Boot Signing Key" -d /etc/pki/pesign/ -t "Pu,Pu,Pu"
sudo openssl pkcs12 -export -out MOK.p12 -inkey MOK.priv -in MOK.der
sudo pk12util -i MOK.p12 -d /etc/pki/pesign
And yeah obviously you also want to do:
sudo mokutil --import MOK.der
Jarkko Sakkinen
jarkkoWhen kernel testing e.g. with BuildRoot this would be more lean than actual eBPF.
"git workspace" gives a reference model for clone snapshotting.
Usually when fixing kernel bug or doing some improvement to kernel, adding a few temp printk's is still imho the king because kernel compiles in no time. Dynamic tracing tools do not support this workflow very well. They support well debugging exactly live systems, which is totally different use case.
#linux #kernel #ebpf
Jarkko Sakkinen
jarkkoIt gives a rough ballpark factor for single core performance against i7-1260P
given that compilation (which distributes best) takes quite insignificant portion of the time, and most is spent in linking...
Jarkko Sakkinen
jarkkoFrom graphical ones GNOME projects Fractal is otherwise great except the lack of thread view.
#matrix
Jarkko Sakkinen
jarkko#fedora #linux
Jarkko Sakkinen
jarkkoThe only other part I know for sure is https://www.fractal-design.com/products/cases/meshify/meshify-2-mini/black-tg-dark-tint/
This is because I only ever buy Fractal Design cases :-)
Can't wait for the smell of a fresh computer...
K. Ryabitsev 🍁
monsieuriconx.x.x.x - - [10/Nov/2024:00:02:37 +0000] "GET / HTTP/1.1" 301 162 "-" "okhttp/4.9.0"
You know what’s interesting about this log line? It repeats 56,686,963 times in www.kernel.org logs for yesterday, across 4 nodes. That’s about 700 times a second, and this has been going on for months.
These requests aren’t intentionally malicious – they issue a simple GET /, receive their 301 redirect, and terminate the connection. From what I can tell, this is some kind of appliance or software installed on mobile clients that uses “can I reach www.kernel.org” as a network test.
This wouldn’t be that big of a deal – a single plaintext “GET /“ that triggers an immediate 301 is very cheap for us to generate, but the number of these requests has been steadily growing.
If you have any idea what this is and how to make it stop, please reach out?
Jarkko Sakkinen
jarkkoAnd DRPK troops terrorizing Europe is unacceptable. Any country who brings them here in this region should pay the consequences. It's even orthogonal to the war situation. North Korea is an enemy state and any aggressive action from such should receive a clear and brutal response.
https://www.independent.co.uk/news/uk/politics/boris-johnson-ukraine-uk-troops-putin-b2645681.html
Jarkko Sakkinen
jarkkoOne feature that I like a lot in Helix is "no plugins" ;-) That's fresh. One thing that I wished it had, and thus not applicable for kernel development, is the support for ".editorconfig". Once it has that I can try to write a kernel patch with it.
#helix #vim #editor
Oxide Computer Company
oxidecomputer@hachyderm.iodtrace.conf(24) is going virtual! We're one month away from the un-conference and are opening the virtual ticket booth for this free event, with optional add-ons for event t-shirts and an on-site social in Emeryville after the event. Bring your topics and prepare to discuss! https://dtraceconf24.eventbrite.com