Posts
2150Following
230Followers
2545This account is for Linux/Kernel/FOSS topics in general: #linux, #kernel, #foss, #git, #sysadmin, #infrastructure.
For my personal account, please follow @monsieuricon@castoranxieux.ca.
Montréal, Québec, Canada 🇨🇦🇺🇦
K. Ryabitsev-Prime 🍁
 repeated
repeated
akkoma stuff
akkoma@ihatebeinga.live
attention duelists!
a rather important security update has just been released (v.3.13.2)
i'd advise upgrading asap
no special intervention needed, just a standard upgrade
https://meta.akkoma.dev/t/akkoma-stable-2024-04-straight-up-fixing-it-in-the-git-and-by-it-haha-well-i-mean-our-bhackend/715/15?u=floatingghost
a rather important security update has just been released (v.3.13.2)
i'd advise upgrading asap
no special intervention needed, just a standard upgrade
https://meta.akkoma.dev/t/akkoma-stable-2024-04-straight-up-fixing-it-in-the-git-and-by-it-haha-well-i-mean-our-bhackend/715/15?u=floatingghost
K. Ryabitsev-Prime 🍁
monsieuricon
@CurtAdams We need to normalize that it's okay to be excited about the promise of a technology, but at the same time recognize that it is not safe for general use. That's going to be my general advise to anyone -- it's something to watch, but as of right now, using FSD creates dangerous situations on the roads and can result in fatalities, so should be only used in controlled environments.
K. Ryabitsev-Prime 🍁
monsieuricon
@ljs You may be right! I'll try driving on the left side for a day and let you know if there's any marked improvement.
K. Ryabitsev-Prime 🍁
monsieuricon
@ljs I believe it's the default mode of all drivers (except me, of course, I'm the only excellent driver on the road).
K. Ryabitsev-Prime 🍁
monsieuricon
Tesla is running a deep discount on the "Full Self Drive (FSD)" subscription right now, so I got it for a month just to try it out. I've completely turned it off after a couple of days:
- It tried to drive me through red lights a couple of times, because apparently, it has no concept of "green arrow" and assumes anything greenish-looking means green in all directions.
- I can sense the frustration from other drivers, because the FSD is stupidly indecisive at intersections with all-direction stop signs -- it waits for too long, and then tries to go when the other driver has given up waiting on me.
- When it auto-changes lanes to pass a slower vehicle, it just stays in the left lane and only moves right when something comes up behind at higher speed -- and at that point the other driver is already changing lanes to pass me on the right because I'm clearly stupid.
- And overall, it's like permanently having a grossly incompetent driver's ed graduate drive you around.
Don't bother. It will make everyone angry and then try to kill you.
- It tried to drive me through red lights a couple of times, because apparently, it has no concept of "green arrow" and assumes anything greenish-looking means green in all directions.
- I can sense the frustration from other drivers, because the FSD is stupidly indecisive at intersections with all-direction stop signs -- it waits for too long, and then tries to go when the other driver has given up waiting on me.
- When it auto-changes lanes to pass a slower vehicle, it just stays in the left lane and only moves right when something comes up behind at higher speed -- and at that point the other driver is already changing lanes to pass me on the right because I'm clearly stupid.
- And overall, it's like permanently having a grossly incompetent driver's ed graduate drive you around.
Don't bother. It will make everyone angry and then try to kill you.
K. Ryabitsev-Prime 🍁
monsieuricon
@dangoodin @triskelion Dan, thank you for following up. I do not speak for the Linux Foundation, so I cannot address any of the items you highlighted in any official way. However, two important facts to keep in mind: 1) at the time of the break-in, k.org infrastructure was NOT managed by LF. It was managed by a team of volunteers from the kernel development community. LF only took the stewardship of k.org infrastructure several months after the incident. I believe I was the first actual LF employee to get access to k.org infrastructure, and that was in November of 2011, when I started at the Foundation. 2) the findings in the paper about "2 years" were as new to me as to everyone else, and I have no idea about the source on which they base this claim. I believe that all hardware involved in the compromise was turned over to the FBI as part of the investigation and I didn't get to touch any of it -- physically or otherwise.
For the transparency aspect of things, I want to direct you to my talk I gave to the Linux Security Summit last year: https://youtu.be/K3SVt1WCheY?si=KbbCWTGCypfFTdSy
In it, I go over a lot of things, including how we try to make ourselves more resilient to any repeat compromises, should they happen (or if they already have and we just don't know it yet).
HTH.
For the transparency aspect of things, I want to direct you to my talk I gave to the Linux Security Summit last year: https://youtu.be/K3SVt1WCheY?si=KbbCWTGCypfFTdSy
In it, I go over a lot of things, including how we try to make ourselves more resilient to any repeat compromises, should they happen (or if they already have and we just don't know it yet).
HTH.
K. Ryabitsev-Prime 🍁
monsieuricon
@becomingwisest I'm not out to be rude. I just forwarded it up the chain.
K. Ryabitsev-Prime 🍁
monsieuricon
@triskelion @dangoodin Dude, I don't know what I did to make you hostile to me. I wasn't there when any promises were made by previous k.org admins and I've certainly made transparency the core principle of our work. /o\
K. Ryabitsev-Prime 🍁
monsieuricon
@wyatt8740 When reading "Equal Rites," do you get the vibe that JK Rowling also read that book and went "huh, an outcast applying for a wizarding school, that's a pretty neat plot"?
K. Ryabitsev-Prime 🍁
monsieuricon
Heh, this dude emailed the helpdesk address at 4:40PM my time asking for a comment on a sensitive matter, and gave me a 2-hour turnaround to respond.
shrugging_pony.gif
shrugging_pony.gif
K. Ryabitsev-Prime 🍁
monsieuricon
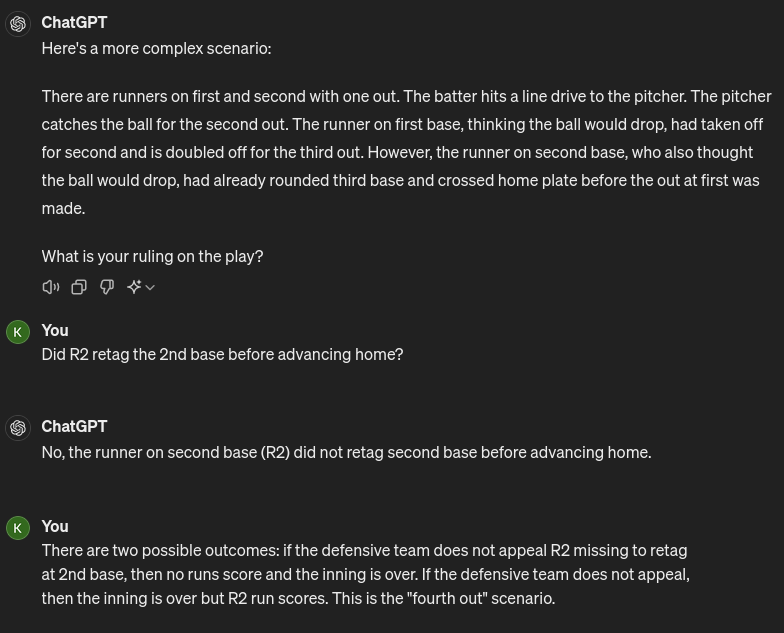
I've got to admit that ChatGPT 4o does a lot better at complex baseball scenarios than its predecessors. It still gives me invalid answers every now and again, but now they aren't nearly as frequent.
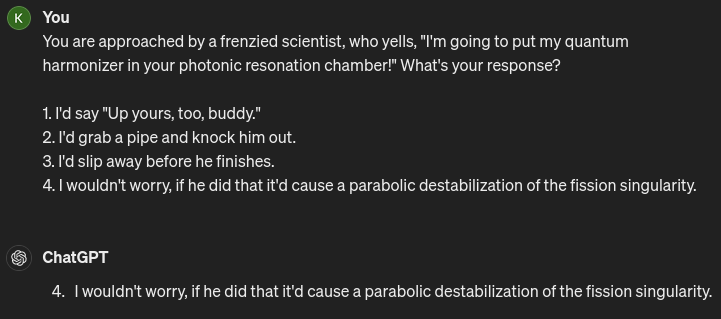
Just as a synth would do.
Just as a synth would do.
K. Ryabitsev-Prime 🍁
monsieuricon
That said, "EatKernel" could totally be a legit fuzzing tool.
K. Ryabitsev-Prime 🍁
monsieuricon
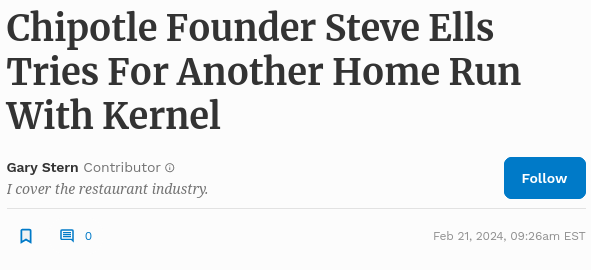
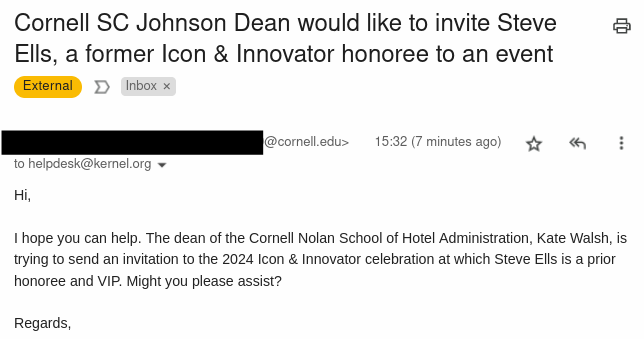
I'd like to know how someone can manage to find the helpdesk address on the kernel.org site, and yet not figure out that, you know, maybe it's not the site for the restaurant chain launched by the former Chipotle Mexican Grill CEO.