Posts
350Following
95Followers
3920Thomas Depierre
Di4na@hachyderm.ioI think I finally found out why it feels like CISA live on Alpha Centauri.
> “It’s a myth,” she declared, “that software vulnerability is an inevitability. … It’s the same classes of defects we’ve known about for decades and known how to fix for years.”
This is both true and utterly wrong. It is true, we know how to detect and fix them for decades. In research.
But you know what we do not have? Industry tool that can be used in the industry based on this knowledge.
Matthew Garrett
mjg59@nondeterministic.computer"Linux would have prevented this!" literally true because my former colleague KP Singh wrote a kernel security module that lets EDR implementations load ebpf into the kernel to monitor and act on security hooks and Crowdstrike now uses that rather than requiring its own kernel module that would otherwise absolutely have allowed this to happen, so everyone please say thank you to him
daniel:// stenberg://
bagder@mastodon.socialIt is time we realize and accept that there can never be a single nor objective criticality score for a CVE.
binbows@labyrinth.zone
binbows@labyrinth.zoneit's YOUR day!
ruin it yourself by attempting a gentoo install
Greg K-H
gregkhGreg K-H
gregkhGreg K-H
gregkh
Gustavo A. R. Silva 
gustavoars@fosstodon.org
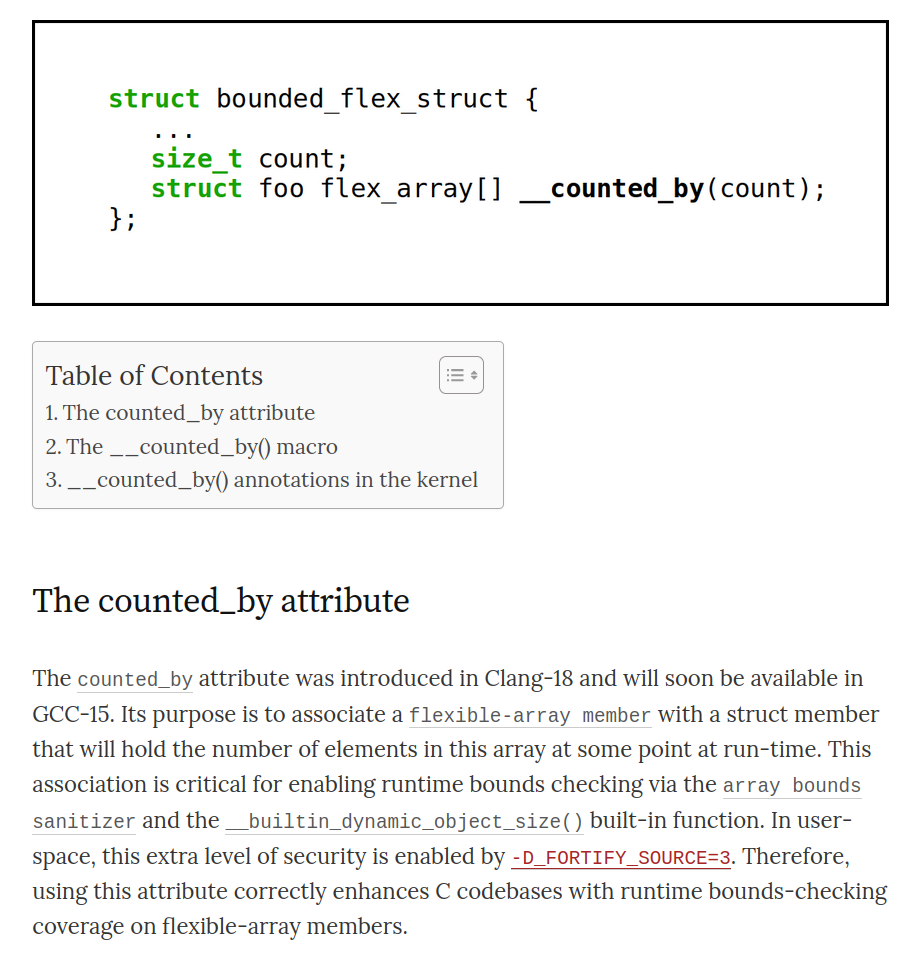
I just wrote a blog post about how to use the new counted_by attribute in C and the Linux kernel. I've been mentioning this attribute in my presentations over the past year, and I thought it was about time to write about it. So, here you go:
"How to use the new counted_by attribute in C (and Linux)"
https://embeddedor.com/blog/2024/06/18/how-to-use-the-new-counted_by-attribute-in-c-and-linux/
I hope you find it useful. Thanks!
Kernel Self-Protection Project ⚔ 🛡 🐧
Greg K-H
gregkhRE: https://mastodon.nl/@bert_hubert/112608731406238492
Greg K-H
gregkhAnd we are allowed, and in some places, required, to go on vacation, so a few weeks off isn't going to really stall anything, we all have other ways of testing integrations, so don't worry :)
Greg K-H
gregkh{sigh}
You are now blocked.
Greg K-H
gregkhSide note, I create all the json from a set of wonderfully horrible bash scripts that parse the semi-free-flowing kernel git commit logs and branches to determine the information needed:
https://git.kernel.org/pub/scm/linux/security/vulns.git/tree/scripts/bippy
https://git.kernel.org/pub/scm/linux/security/vulns.git/tree/scripts/dyad
https://git.sr.ht/~gregkh/linux-stable_commit_tree/tree/master/item/id_found_in
Bert Hubert NL 🇺🇦🇪🇺🇺🇦
bert_hubert@mastodon.nlOver vorige post, je kan ook zeggen dat het kabinet "geen grip heeft op de migratie" (naar de cloud). https://berthub.eu/articles/posts/de-hele-overheid-naar-de-cloud-dat-is-een-politiek-besluit/
Greg K-H
gregkhAll other operating systems are in the same boat, either they are not actually fixing things, or they are not reporting them. You ask them which it is...
Greg K-H
gregkhIf you don't like CVEs, wonderful, just ignore them, they aren't causing you any issues. If you do like CVEs, great, I have loads of them for you :)
Again, the way CVEs for the Linux kernel were being allocated was broken and being abused by many corporations. We have now fixed that by hopefully making it work for _everyone_ who cares about CVEs, not just the few in the past that were taking advantage of it for their own gain. That is not "trolling", that is "working to fix the broken system that was previously in place".
Greg K-H
gregkhBut what I'm saying now is that I am NOT trolling anyone. The number of CVEs created for the kernel is exactly what cve.org wants us to do here as now we ARE allowed to be a CNA. And by being a CNA, we must follow the rules of cve.org which is what we are doing. I have had many meetings with the cve.org employees and board about this, and everyone seems to be in agreement that what we are doing now is correct and should be done this way.
Again, I'm not trolling anyone, and again, the kernel development model has not changed, all that has changed is that finally we are marking all potential vulnerability fixes as CVEs.
Again, if anyone knows of any CVE entries that we have assigned that should not be CVE entries, please let us know.
Greg K-H
gregkhAnd that means assigning CVEs to everything that meets the definition of vulnerability as defined by cve.org. If you, or anyone else notices a CVE we issue that does NOT meet that definition, please let us know and we will be glad to reject it.
Odds are other operating system kernels will start doing the same as Linux does, if they wish to be a CNA for their project. We aren't alone here, it's just that we report our fixes, others don't, or aren't actually developing any fixes. You be the judge of which is the case for various projects :)
Morten Linderud
Foxboron@chaos.socialOf course it has. CVE identifiers have been misinterpreted/misused/misunderstood this way for years.