Posts
350Following
95Followers
3946Greg K-H
gregkhAnyway, got me to thinking, a while ago a friend (also a kernel developer) had the idea of a presentation for the yearly Kernel Recipes conference that would be him sending me a patch, me reviewing it, talking about how it is reviewed, and the back and forth between us on getting it into a mergable state. That process is one that someone else recently asked me "what presentations can you recommend for new kernel developers to explain how this review process works" and I didn't have any suggestions, but it really is an important thing that is not taught at all in school, or in any company that I know of.
So maybe, a series of videos, or talks, where a maintainer gets a patch series and walks through how they review it, what they look for, what they expect, and how its tested (if at all), might be interesting? Or "here's a reported bug, how do you debug it?" type of presentation to put a developer through the steps of attacking something unknown, and figuring out what the problem is, and how it could possibly be solved.
Brings me back to the days of the Plumbers conference session where we had "bring us your laptop and we will get suspend/resume to work on it" tracks that ended up being a lot of fun for everyone involved as crazy hardware/bios issues were debugged live.
Would this even be interesting? I think it might need a lot of good editing, you don't want to see me staring numly at a terminal window for a few hours while reading lots of inscrutable driver code tracing it to find a bug, that would put everyone to sleep...
Greg K-H
gregkhRE: https://fosstodon.org/users/kernellogger/statuses/110855114931496454
Greg K-H
gregkhJohn did it much better with one less adapter than I so this stack could be smaller if needed, but this is all I could find locally.
Greg K-H
gregkhhttps://kccnceu2023.sched.com/event/1Lnv0
Should be fun, if you are at KubeCon, stop by and ask questions, it's meant to be a discussion. A recording will be made public afterwards too.
Greg K-H
gregkhbpftrace fun question of the week I’ve been beating my head against for a while now.
Given the following bpftrace program:
tracepoint:syscalls:sys_enter_open,
tracepoint:syscalls:sys_enter_openat
{
$g = "magic_command_to_exit_trace";
$s = str(args->filename);
printf("%s\n", $s);
if ($s == $g) {
exit();
}
}
I get the lovely warning:
WARNING: Addrspace mismatch
if ($s == $g) {
which I can understand. But what I can’t figure out is how to resolve this (hint, the program works just fine, when opening the “magic” file, the trace exits), as how to turn a literal string into the proper address space that args->filename is?
I’ve dug into too many bpftrace git commits to try to figure it out, to no luck. Anyone have a hint?
Oh, and if you want to see where this is used, it’s in this “fun” script: https://github.com/gregkh/gregkh-linux/blob/master/scripts/trace_kernel_build.sh
Warning, realpath takes a long time when processing millions of files, be patient when running the script.
Greg K-H
gregkhhttps://social.kernel.org/notice/AU5IphRPUsQvvkx732
But why does any of this matter? As most everyone knows, Linux kernel development happens through email, and the Message-Id of an email is a unique identifier that is used to track messages in our patch handling tools and archives (see https://lore.kernel.org for the archives.) By crafting shorter-but-still-unique message ids it's easier to reference those messages in other places, and using words is just prettier overall than random UUID values (https://i.redd.it/64gl4t9s52ra1.jpg for an example)
Bonus to all of this is that people don't realize that most of the patches we send out are actually signed and can be validated as coming from the person that sent them. The tool we use for that looks at the body of the email, and a small subset of the Header tags in the email. By providing to the tool our custom Message-Id, that adds yet another portion of the email that is now able to be signed and validated, providing a tiny bit more security overall in the patch submission processes (very very tiny, I know, but it's real, as I found out when I submitted a patch with a broken message-id from what was signed and our tools caught it.)
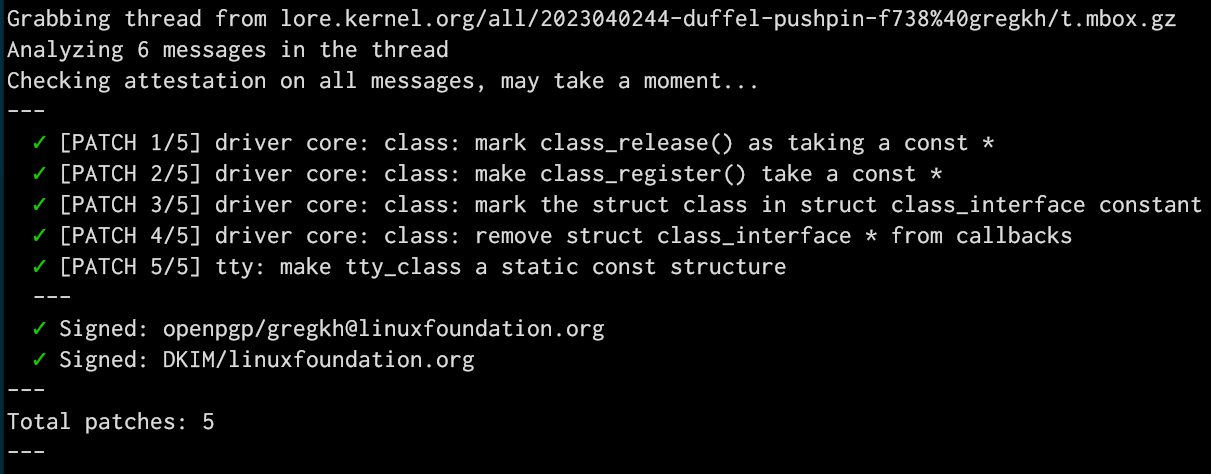
Anyway, all of that is a long way of showing off a tiny core change to the kernel that allows some core structures to be moved to read-only memory that I've been working on for a few months now. Here's the last portion of that work being sucked off of the email archives and validated as coming from me:
K. Ryabitsev-Prime 🍁
monsieuricon@gregkh: challenge accepted!
Greg K-H
gregkhHopefully things now settle down to the normal constant crazy pace we are used to (1-2 releases a week), instead of the mass of releases we had in the past few days.
Greg K-H
gregkhGreg K-H
gregkh"Yes that is an odd set of things to remember."
"I don't know, historical reasons."
"Yes, graphical editors are prettier, but sometimes you will have to use this."
Parents, don't forget to have the uncomfortable conversation with your children about vim _before_ they leave for college and are exposed to the siren-call of vscode.
Greg K-H
gregkhhttps://git.kernel.org/pub/scm/docs/kernel/website.git/commit/?id=5cca06606a7dcb2a0a6b6a818072b81b21287b3b
K. Ryabitsev-Prime 🍁
monsieuriconEveryone using "b4 send" must upgrade to stop hitting Python email module bugs.
https://lore.kernel.org/tools/20230120165712.rznwonw6nbfhc7fo@meerkat.local/
Greg K-H
gregkhhttps://www.theverge.com/23513517/steam-deck-long-term-test-valve
Now if only they would switch to use the LTS kernel releases, I'd be totally satisfied.
Greg K-H
gregkhTook me forever to try to figure out what was wrong with the kernel code itself, should have realized it was the host system issue instead. Hermetic Android builds must have come later in the Android release cycle.
Greg K-H
gregkhCompanies will have to update their kernel to a newer version over the lifespan of the device in order to stay in compliance.
As I heard recently in a meeting with one Android vendor, "Android updates consist of over 2000 programs updated to the latest version, what's so hard about adding 1 more to it?"
So if the requirement from Android to have a 6 year supported kernel version is now gone, maybe we don't have to do it upstream either? That will make so many people very happy.
Also, Apple has been doing this for a long time for their devices, why do people feel it is somehow impossible? :)
https://ec.europa.eu/info/law/better-regulation/have-your-say/initiatives/12797-Designing-mobile-phones-and-tablets-to-be-sustainable-ecodesign_en
Greg K-H
gregkhK. Ryabitsev-Prime 🍁
monsieuricon@gregkh: [PATCH 6.1 0000/1146]